A Cloud Based Machine Intelligent Framework to Identify DDoS Botnet Attack in Internet of Things Article Swipe
 YOU?
·
· 2022
· Open Access
·
· DOI: https://doi.org/10.55524/ijirem.2022.9.4.1
YOU?
·
· 2022
· Open Access
·
· DOI: https://doi.org/10.55524/ijirem.2022.9.4.1
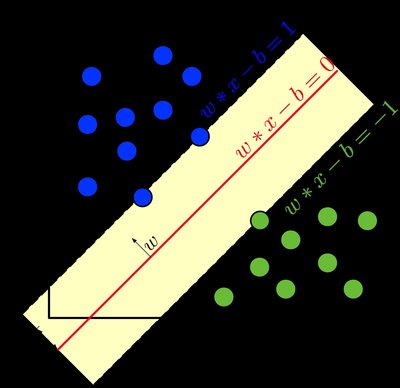
First few Botnet attack is a major issue in security of Internet of Things (IoT) devices and it needs to be identified to secure the system from the attackers. In this paper, a cloud-based machine intelligent framework is proposed to identify DDoS (distributed denial of service) Botnet attack in IoT systems. In this framework, the IoT devices communicating with the cloud are categorized based on their communication record to check the DDoS Botnet attack. In this work, three DDoS botnet attacks are considered such as HTTP, UDP, and TCP. The cloud is installed with a supervised machine intelligent model to classify the type of DDoS attack. The model is selected by considering 4 models such as Tree, stacking classifier, Neural Network (NN), and Support Vector Machine (SVM) and performance is evaluated based on classification accuracy (CA). Here, the stacking classifier is a hybrid model designed using the aggregation of Logistic Regression (LR), NN, and SVM. The performance is evaluated using Python tool. From the results it was found that except Tree all three models show an CA of 1.0. The computation time is also analyzed for four models and it was found that Tree shows less time than other models however, if considered with respect to CA (1.0) then SVM can be preferred as it shows lesser time then other two models. The detection time of the IoT devices is also simulated and result show that if SVM is installed in cloud then the detection time is lesser.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- http://doi.org/10.55524/ijirem.2022.9.4.1
- https://doi.org/10.55524/ijirem.2022.9.4.1
- OA Status
- diamond
- References
- 26
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4294390278
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4294390278Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.55524/ijirem.2022.9.4.1Digital Object Identifier
- Title
-
A Cloud Based Machine Intelligent Framework to Identify DDoS Botnet Attack in Internet of ThingsWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2022Year of publication
- Publication date
-
2022-08-01Full publication date if available
- Authors
-
Sourav Kumar Bhoi, Krishna Prasad KList of authors in order
- Landing page
-
https://doi.org/10.55524/ijirem.2022.9.4.1Publisher landing page
- PDF URL
-
https://doi.org/10.55524/ijirem.2022.9.4.1Direct link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
diamondOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.55524/ijirem.2022.9.4.1Direct OA link when available
- Concepts
-
Botnet, Denial-of-service attack, Computer science, Cloud computing, Support vector machine, Artificial intelligence, Machine learning, Computer security, Internet of Things, Application layer DDoS attack, Computer network, Python (programming language), Random forest, Classifier (UML), The Internet, Data mining, Operating systemTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
0Total citation count in OpenAlex
- References (count)
-
26Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4294390278 |
|---|---|
| doi | https://doi.org/10.55524/ijirem.2022.9.4.1 |
| ids.doi | https://doi.org/10.55524/ijirem.2022.9.4.1 |
| ids.openalex | https://openalex.org/W4294390278 |
| fwci | 0.0 |
| type | article |
| title | A Cloud Based Machine Intelligent Framework to Identify DDoS Botnet Attack in Internet of Things |
| biblio.issue | |
| biblio.volume | |
| biblio.last_page | 5 |
| biblio.first_page | 1 |
| topics[0].id | https://openalex.org/T10400 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9997000098228455 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1705 |
| topics[0].subfield.display_name | Computer Networks and Communications |
| topics[0].display_name | Network Security and Intrusion Detection |
| topics[1].id | https://openalex.org/T11512 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9883000254631042 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1702 |
| topics[1].subfield.display_name | Artificial Intelligence |
| topics[1].display_name | Anomaly Detection Techniques and Applications |
| topics[2].id | https://openalex.org/T11241 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9843999743461609 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1711 |
| topics[2].subfield.display_name | Signal Processing |
| topics[2].display_name | Advanced Malware Detection Techniques |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C22735295 |
| concepts[0].level | 3 |
| concepts[0].score | 0.9486160278320312 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q317671 |
| concepts[0].display_name | Botnet |
| concepts[1].id | https://openalex.org/C38822068 |
| concepts[1].level | 3 |
| concepts[1].score | 0.8518710136413574 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q131406 |
| concepts[1].display_name | Denial-of-service attack |
| concepts[2].id | https://openalex.org/C41008148 |
| concepts[2].level | 0 |
| concepts[2].score | 0.7593629360198975 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[2].display_name | Computer science |
| concepts[3].id | https://openalex.org/C79974875 |
| concepts[3].level | 2 |
| concepts[3].score | 0.7145535349845886 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q483639 |
| concepts[3].display_name | Cloud computing |
| concepts[4].id | https://openalex.org/C12267149 |
| concepts[4].level | 2 |
| concepts[4].score | 0.6755388975143433 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q282453 |
| concepts[4].display_name | Support vector machine |
| concepts[5].id | https://openalex.org/C154945302 |
| concepts[5].level | 1 |
| concepts[5].score | 0.5153767466545105 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[5].display_name | Artificial intelligence |
| concepts[6].id | https://openalex.org/C119857082 |
| concepts[6].level | 1 |
| concepts[6].score | 0.5143436193466187 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q2539 |
| concepts[6].display_name | Machine learning |
| concepts[7].id | https://openalex.org/C38652104 |
| concepts[7].level | 1 |
| concepts[7].score | 0.4579031467437744 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[7].display_name | Computer security |
| concepts[8].id | https://openalex.org/C81860439 |
| concepts[8].level | 2 |
| concepts[8].score | 0.4436275064945221 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q251212 |
| concepts[8].display_name | Internet of Things |
| concepts[9].id | https://openalex.org/C120865594 |
| concepts[9].level | 4 |
| concepts[9].score | 0.44284284114837646 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q131406 |
| concepts[9].display_name | Application layer DDoS attack |
| concepts[10].id | https://openalex.org/C31258907 |
| concepts[10].level | 1 |
| concepts[10].score | 0.4352284073829651 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q1301371 |
| concepts[10].display_name | Computer network |
| concepts[11].id | https://openalex.org/C519991488 |
| concepts[11].level | 2 |
| concepts[11].score | 0.4340035021305084 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q28865 |
| concepts[11].display_name | Python (programming language) |
| concepts[12].id | https://openalex.org/C169258074 |
| concepts[12].level | 2 |
| concepts[12].score | 0.4332467317581177 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q245748 |
| concepts[12].display_name | Random forest |
| concepts[13].id | https://openalex.org/C95623464 |
| concepts[13].level | 2 |
| concepts[13].score | 0.4274728298187256 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q1096149 |
| concepts[13].display_name | Classifier (UML) |
| concepts[14].id | https://openalex.org/C110875604 |
| concepts[14].level | 2 |
| concepts[14].score | 0.3705056309700012 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q75 |
| concepts[14].display_name | The Internet |
| concepts[15].id | https://openalex.org/C124101348 |
| concepts[15].level | 1 |
| concepts[15].score | 0.3612635135650635 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q172491 |
| concepts[15].display_name | Data mining |
| concepts[16].id | https://openalex.org/C111919701 |
| concepts[16].level | 1 |
| concepts[16].score | 0.13384070992469788 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q9135 |
| concepts[16].display_name | Operating system |
| keywords[0].id | https://openalex.org/keywords/botnet |
| keywords[0].score | 0.9486160278320312 |
| keywords[0].display_name | Botnet |
| keywords[1].id | https://openalex.org/keywords/denial-of-service-attack |
| keywords[1].score | 0.8518710136413574 |
| keywords[1].display_name | Denial-of-service attack |
| keywords[2].id | https://openalex.org/keywords/computer-science |
| keywords[2].score | 0.7593629360198975 |
| keywords[2].display_name | Computer science |
| keywords[3].id | https://openalex.org/keywords/cloud-computing |
| keywords[3].score | 0.7145535349845886 |
| keywords[3].display_name | Cloud computing |
| keywords[4].id | https://openalex.org/keywords/support-vector-machine |
| keywords[4].score | 0.6755388975143433 |
| keywords[4].display_name | Support vector machine |
| keywords[5].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[5].score | 0.5153767466545105 |
| keywords[5].display_name | Artificial intelligence |
| keywords[6].id | https://openalex.org/keywords/machine-learning |
| keywords[6].score | 0.5143436193466187 |
| keywords[6].display_name | Machine learning |
| keywords[7].id | https://openalex.org/keywords/computer-security |
| keywords[7].score | 0.4579031467437744 |
| keywords[7].display_name | Computer security |
| keywords[8].id | https://openalex.org/keywords/internet-of-things |
| keywords[8].score | 0.4436275064945221 |
| keywords[8].display_name | Internet of Things |
| keywords[9].id | https://openalex.org/keywords/application-layer-ddos-attack |
| keywords[9].score | 0.44284284114837646 |
| keywords[9].display_name | Application layer DDoS attack |
| keywords[10].id | https://openalex.org/keywords/computer-network |
| keywords[10].score | 0.4352284073829651 |
| keywords[10].display_name | Computer network |
| keywords[11].id | https://openalex.org/keywords/python |
| keywords[11].score | 0.4340035021305084 |
| keywords[11].display_name | Python (programming language) |
| keywords[12].id | https://openalex.org/keywords/random-forest |
| keywords[12].score | 0.4332467317581177 |
| keywords[12].display_name | Random forest |
| keywords[13].id | https://openalex.org/keywords/classifier |
| keywords[13].score | 0.4274728298187256 |
| keywords[13].display_name | Classifier (UML) |
| keywords[14].id | https://openalex.org/keywords/the-internet |
| keywords[14].score | 0.3705056309700012 |
| keywords[14].display_name | The Internet |
| keywords[15].id | https://openalex.org/keywords/data-mining |
| keywords[15].score | 0.3612635135650635 |
| keywords[15].display_name | Data mining |
| keywords[16].id | https://openalex.org/keywords/operating-system |
| keywords[16].score | 0.13384070992469788 |
| keywords[16].display_name | Operating system |
| language | en |
| locations[0].id | doi:10.55524/ijirem.2022.9.4.1 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210225444 |
| locations[0].source.issn | 2350-0557 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2350-0557 |
| locations[0].source.is_core | False |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | International Journal of Innovative Research in Engineering & Management |
| locations[0].source.host_organization | |
| locations[0].source.host_organization_name | |
| locations[0].license | |
| locations[0].pdf_url | https://doi.org/10.55524/ijirem.2022.9.4.1 |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | International Journal of Innovative Research in Engineering & Management |
| locations[0].landing_page_url | http://doi.org/10.55524/ijirem.2022.9.4.1 |
| indexed_in | crossref |
| authorships[0].author.id | https://openalex.org/A5044453219 |
| authorships[0].author.orcid | https://orcid.org/0000-0002-5173-3453 |
| authorships[0].author.display_name | Sourav Kumar Bhoi |
| authorships[0].countries | IN |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I19008122 |
| authorships[0].affiliations[0].raw_affiliation_string | Institute of Computer Science and Information Science, Srinivas University, Mangaluru-575001, Karnataka, India |
| authorships[0].affiliations[1].raw_affiliation_string | Post Doctoral Fellow, Research Center Department, Computer Science and Information Science, |
| authorships[0].institutions[0].id | https://openalex.org/I19008122 |
| authorships[0].institutions[0].ror | https://ror.org/05fep3933 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I19008122 |
| authorships[0].institutions[0].country_code | IN |
| authorships[0].institutions[0].display_name | Mangalore University |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Sourav Kumar Bhoi |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Institute of Computer Science and Information Science, Srinivas University, Mangaluru-575001, Karnataka, India, Post Doctoral Fellow, Research Center Department, Computer Science and Information Science, |
| authorships[1].author.id | https://openalex.org/A5038904775 |
| authorships[1].author.orcid | |
| authorships[1].author.display_name | Krishna Prasad K |
| authorships[1].affiliations[0].raw_affiliation_string | Associate Professor, Institute of Computer Science and Information Science, Srinivas University, Pandeshwar, Mangaluru, Karnataka, India |
| authorships[1].author_position | last |
| authorships[1].raw_author_name | Krishna Prasad K |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Associate Professor, Institute of Computer Science and Information Science, Srinivas University, Pandeshwar, Mangaluru, Karnataka, India |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.55524/ijirem.2022.9.4.1 |
| open_access.oa_status | diamond |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | A Cloud Based Machine Intelligent Framework to Identify DDoS Botnet Attack in Internet of Things |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10400 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9997000098228455 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1705 |
| primary_topic.subfield.display_name | Computer Networks and Communications |
| primary_topic.display_name | Network Security and Intrusion Detection |
| related_works | https://openalex.org/W2783792841, https://openalex.org/W3166165364, https://openalex.org/W2598265749, https://openalex.org/W2560748881, https://openalex.org/W2181380068, https://openalex.org/W4285609096, https://openalex.org/W2389528884, https://openalex.org/W4284680554, https://openalex.org/W2779270152, https://openalex.org/W3026018975 |
| cited_by_count | 0 |
| locations_count | 1 |
| best_oa_location.id | doi:10.55524/ijirem.2022.9.4.1 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210225444 |
| best_oa_location.source.issn | 2350-0557 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2350-0557 |
| best_oa_location.source.is_core | False |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | International Journal of Innovative Research in Engineering & Management |
| best_oa_location.source.host_organization | |
| best_oa_location.source.host_organization_name | |
| best_oa_location.license | |
| best_oa_location.pdf_url | https://doi.org/10.55524/ijirem.2022.9.4.1 |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | International Journal of Innovative Research in Engineering & Management |
| best_oa_location.landing_page_url | http://doi.org/10.55524/ijirem.2022.9.4.1 |
| primary_location.id | doi:10.55524/ijirem.2022.9.4.1 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210225444 |
| primary_location.source.issn | 2350-0557 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2350-0557 |
| primary_location.source.is_core | False |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | International Journal of Innovative Research in Engineering & Management |
| primary_location.source.host_organization | |
| primary_location.source.host_organization_name | |
| primary_location.license | |
| primary_location.pdf_url | https://doi.org/10.55524/ijirem.2022.9.4.1 |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | International Journal of Innovative Research in Engineering & Management |
| primary_location.landing_page_url | http://doi.org/10.55524/ijirem.2022.9.4.1 |
| publication_date | 2022-08-01 |
| publication_year | 2022 |
| referenced_works | https://openalex.org/W2038244154, https://openalex.org/W6745706219, https://openalex.org/W6740998496, https://openalex.org/W2921069441, https://openalex.org/W2965568386, https://openalex.org/W2980038013, https://openalex.org/W3152901292, https://openalex.org/W3109979169, https://openalex.org/W6732952056, https://openalex.org/W3048529935, https://openalex.org/W3117510159, https://openalex.org/W3047314667, https://openalex.org/W3122864121, https://openalex.org/W3124724827, https://openalex.org/W6769357154, https://openalex.org/W4281784247, https://openalex.org/W4281910928, https://openalex.org/W3173500524, https://openalex.org/W3167530566, https://openalex.org/W2981791596, https://openalex.org/W3128098287, https://openalex.org/W2733765803, https://openalex.org/W2768152971, https://openalex.org/W2760063353, https://openalex.org/W4241054193, https://openalex.org/W2586432806 |
| referenced_works_count | 26 |
| abstract_inverted_index.4 | 112 |
| abstract_inverted_index.a | 5, 32, 94, 141 |
| abstract_inverted_index.CA | 176, 206 |
| abstract_inverted_index.In | 29, 51, 74 |
| abstract_inverted_index.an | 175 |
| abstract_inverted_index.as | 84, 115, 213 |
| abstract_inverted_index.be | 20, 211 |
| abstract_inverted_index.by | 110 |
| abstract_inverted_index.if | 201, 236 |
| abstract_inverted_index.in | 8, 48, 240 |
| abstract_inverted_index.is | 4, 37, 91, 108, 129, 140, 157, 182, 229, 238, 246 |
| abstract_inverted_index.it | 17, 165, 189, 214 |
| abstract_inverted_index.of | 10, 12, 44, 103, 148, 177, 225 |
| abstract_inverted_index.on | 64, 132 |
| abstract_inverted_index.to | 19, 22, 39, 68, 99, 205 |
| abstract_inverted_index.IoT | 49, 55, 227 |
| abstract_inverted_index.NN, | 152 |
| abstract_inverted_index.SVM | 209, 237 |
| abstract_inverted_index.The | 89, 106, 155, 179, 222 |
| abstract_inverted_index.all | 171 |
| abstract_inverted_index.and | 16, 87, 122, 127, 153, 188, 232 |
| abstract_inverted_index.are | 61, 81 |
| abstract_inverted_index.can | 210 |
| abstract_inverted_index.few | 1 |
| abstract_inverted_index.for | 185 |
| abstract_inverted_index.the | 24, 27, 54, 59, 70, 101, 137, 146, 163, 226, 243 |
| abstract_inverted_index.two | 220 |
| abstract_inverted_index.was | 166, 190 |
| abstract_inverted_index.1.0. | 178 |
| abstract_inverted_index.DDoS | 41, 71, 78, 104 |
| abstract_inverted_index.From | 162 |
| abstract_inverted_index.SVM. | 154 |
| abstract_inverted_index.TCP. | 88 |
| abstract_inverted_index.Tree | 170, 193 |
| abstract_inverted_index.UDP, | 86 |
| abstract_inverted_index.also | 183, 230 |
| abstract_inverted_index.four | 186 |
| abstract_inverted_index.from | 26 |
| abstract_inverted_index.less | 195 |
| abstract_inverted_index.show | 174, 234 |
| abstract_inverted_index.such | 83, 114 |
| abstract_inverted_index.than | 197 |
| abstract_inverted_index.that | 168, 192, 235 |
| abstract_inverted_index.then | 208, 218, 242 |
| abstract_inverted_index.this | 30, 52, 75 |
| abstract_inverted_index.time | 181, 196, 217, 224, 245 |
| abstract_inverted_index.type | 102 |
| abstract_inverted_index.with | 58, 93, 203 |
| abstract_inverted_index.(1.0) | 207 |
| abstract_inverted_index.(CA). | 135 |
| abstract_inverted_index.(IoT) | 14 |
| abstract_inverted_index.(LR), | 151 |
| abstract_inverted_index.(NN), | 121 |
| abstract_inverted_index.(SVM) | 126 |
| abstract_inverted_index.First | 0 |
| abstract_inverted_index.HTTP, | 85 |
| abstract_inverted_index.Here, | 136 |
| abstract_inverted_index.Tree, | 116 |
| abstract_inverted_index.based | 63, 131 |
| abstract_inverted_index.check | 69 |
| abstract_inverted_index.cloud | 60, 90, 241 |
| abstract_inverted_index.found | 167, 191 |
| abstract_inverted_index.issue | 7 |
| abstract_inverted_index.major | 6 |
| abstract_inverted_index.model | 98, 107, 143 |
| abstract_inverted_index.needs | 18 |
| abstract_inverted_index.other | 198, 219 |
| abstract_inverted_index.shows | 194, 215 |
| abstract_inverted_index.their | 65 |
| abstract_inverted_index.three | 77, 172 |
| abstract_inverted_index.tool. | 161 |
| abstract_inverted_index.using | 145, 159 |
| abstract_inverted_index.work, | 76 |
| abstract_inverted_index.Botnet | 2, 46, 72 |
| abstract_inverted_index.Neural | 119 |
| abstract_inverted_index.Python | 160 |
| abstract_inverted_index.Things | 13 |
| abstract_inverted_index.Vector | 124 |
| abstract_inverted_index.attack | 3, 47 |
| abstract_inverted_index.botnet | 79 |
| abstract_inverted_index.denial | 43 |
| abstract_inverted_index.except | 169 |
| abstract_inverted_index.hybrid | 142 |
| abstract_inverted_index.lesser | 216 |
| abstract_inverted_index.models | 113, 173, 187, 199 |
| abstract_inverted_index.paper, | 31 |
| abstract_inverted_index.record | 67 |
| abstract_inverted_index.result | 233 |
| abstract_inverted_index.secure | 23 |
| abstract_inverted_index.system | 25 |
| abstract_inverted_index.Machine | 125 |
| abstract_inverted_index.Network | 120 |
| abstract_inverted_index.Support | 123 |
| abstract_inverted_index.attack. | 73, 105 |
| abstract_inverted_index.attacks | 80 |
| abstract_inverted_index.devices | 15, 56, 228 |
| abstract_inverted_index.lesser. | 247 |
| abstract_inverted_index.machine | 34, 96 |
| abstract_inverted_index.models. | 221 |
| abstract_inverted_index.respect | 204 |
| abstract_inverted_index.results | 164 |
| abstract_inverted_index.Internet | 11 |
| abstract_inverted_index.Logistic | 149 |
| abstract_inverted_index.accuracy | 134 |
| abstract_inverted_index.analyzed | 184 |
| abstract_inverted_index.classify | 100 |
| abstract_inverted_index.designed | 144 |
| abstract_inverted_index.however, | 200 |
| abstract_inverted_index.identify | 40 |
| abstract_inverted_index.proposed | 38 |
| abstract_inverted_index.security | 9 |
| abstract_inverted_index.selected | 109 |
| abstract_inverted_index.service) | 45 |
| abstract_inverted_index.stacking | 117, 138 |
| abstract_inverted_index.systems. | 50 |
| abstract_inverted_index.detection | 223, 244 |
| abstract_inverted_index.evaluated | 130, 158 |
| abstract_inverted_index.framework | 36 |
| abstract_inverted_index.installed | 92, 239 |
| abstract_inverted_index.preferred | 212 |
| abstract_inverted_index.simulated | 231 |
| abstract_inverted_index.Regression | 150 |
| abstract_inverted_index.attackers. | 28 |
| abstract_inverted_index.classifier | 139 |
| abstract_inverted_index.considered | 82, 202 |
| abstract_inverted_index.framework, | 53 |
| abstract_inverted_index.identified | 21 |
| abstract_inverted_index.supervised | 95 |
| abstract_inverted_index.aggregation | 147 |
| abstract_inverted_index.categorized | 62 |
| abstract_inverted_index.classifier, | 118 |
| abstract_inverted_index.cloud-based | 33 |
| abstract_inverted_index.computation | 180 |
| abstract_inverted_index.considering | 111 |
| abstract_inverted_index.intelligent | 35, 97 |
| abstract_inverted_index.performance | 128, 156 |
| abstract_inverted_index.(distributed | 42 |
| abstract_inverted_index.communicating | 57 |
| abstract_inverted_index.communication | 66 |
| abstract_inverted_index.classification | 133 |
| cited_by_percentile_year | |
| countries_distinct_count | 1 |
| institutions_distinct_count | 2 |
| citation_normalized_percentile.value | 0.11829107 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |