A Comparative Analysis of Machine Learning Algorithms for Intrusion\n Detection in Edge-Enabled IoT Networks Article Swipe
 YOU?
·
· 2021
· Open Access
·
· DOI: https://doi.org/10.48550/arxiv.2111.01383
YOU?
·
· 2021
· Open Access
·
· DOI: https://doi.org/10.48550/arxiv.2111.01383
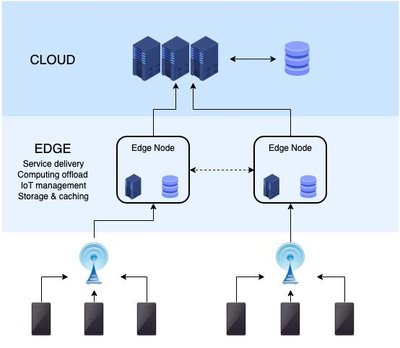
A significant increase in the number of interconnected devices and data\ncommunication through wireless networks has given rise to various threats,\nrisks and security concerns. Internet of Things (IoT) applications is deployed\nin almost every field of daily life, including sensitive environments. The edge\ncomputing paradigm has complemented IoT applications by moving the\ncomputational processing near the data sources. Among various security models,\nMachine Learning (ML) based intrusion detection is the most conceivable defense\nmechanism to combat the anomalous behavior in edge-enabled IoT networks. The ML\nalgorithms are used to classify the network traffic into normal and malicious\nattacks. Intrusion detection is one of the challenging issues in the area of\nnetwork security. The research community has proposed many intrusion detection\nsystems. However, the challenges involved in selecting suitable algorithm(s) to\nprovide security in edge-enabled IoT networks exist. In this paper, a\ncomparative analysis of conventional machine learning classification algorithms\nhas been performed to categorize the network traffic on NSL-KDD dataset using\nJupyter on Pycharm tool. It can be observed that Multi-Layer Perception (MLP)\nhas dependencies between input and output and relies more on network\nconfiguration for intrusion detection. Therefore, MLP can be more appropriate\nfor edge-based IoT networks with a better training time of 1.2 seconds and\ntesting accuracy of 79%.\n
Related Topics
- Type
- preprint
- Landing Page
- http://arxiv.org/abs/2111.01383
- https://arxiv.org/pdf/2111.01383
- OA Status
- green
- Cited By
- 3
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4226105105
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4226105105Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.48550/arxiv.2111.01383Digital Object Identifier
- Title
-
A Comparative Analysis of Machine Learning Algorithms for Intrusion\n Detection in Edge-Enabled IoT NetworksWork title
- Type
-
preprintOpenAlex work type
- Publication year
-
2021Year of publication
- Publication date
-
2021-11-02Full publication date if available
- Authors
-
Poornima Mahadevappa, Syeda Mariam Muzammal, Raja Kumar MurugesanList of authors in order
- Landing page
-
https://arxiv.org/abs/2111.01383Publisher landing page
- PDF URL
-
https://arxiv.org/pdf/2111.01383Direct link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
greenOpen access status per OpenAlex
- OA URL
-
https://arxiv.org/pdf/2111.01383Direct OA link when available
- Concepts
-
Computer science, Intrusion detection system, Enhanced Data Rates for GSM Evolution, Internet of Things, Machine learning, Edge device, Artificial intelligence, Edge computing, Network security, Field (mathematics), Data mining, Computer network, Computer security, Cloud computing, Mathematics, Operating system, Pure mathematicsTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
3Total citation count in OpenAlex
- Citations by year (recent)
-
2024: 2, 2023: 1Per-year citation counts (last 5 years)
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4226105105 |
|---|---|
| doi | https://doi.org/10.48550/arxiv.2111.01383 |
| ids.openalex | https://openalex.org/W4226105105 |
| fwci | 0.49689527 |
| type | preprint |
| title | A Comparative Analysis of Machine Learning Algorithms for Intrusion\n Detection in Edge-Enabled IoT Networks |
| biblio.issue | |
| biblio.volume | |
| biblio.last_page | |
| biblio.first_page | |
| topics[0].id | https://openalex.org/T10400 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9991999864578247 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1705 |
| topics[0].subfield.display_name | Computer Networks and Communications |
| topics[0].display_name | Network Security and Intrusion Detection |
| topics[1].id | https://openalex.org/T11512 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9944000244140625 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1702 |
| topics[1].subfield.display_name | Artificial Intelligence |
| topics[1].display_name | Anomaly Detection Techniques and Applications |
| topics[2].id | https://openalex.org/T12222 |
| topics[2].field.id | https://openalex.org/fields/22 |
| topics[2].field.display_name | Engineering |
| topics[2].score | 0.9866999983787537 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/2208 |
| topics[2].subfield.display_name | Electrical and Electronic Engineering |
| topics[2].display_name | IoT-based Smart Home Systems |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C41008148 |
| concepts[0].level | 0 |
| concepts[0].score | 0.8286041021347046 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[0].display_name | Computer science |
| concepts[1].id | https://openalex.org/C35525427 |
| concepts[1].level | 2 |
| concepts[1].score | 0.7722063660621643 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q745881 |
| concepts[1].display_name | Intrusion detection system |
| concepts[2].id | https://openalex.org/C162307627 |
| concepts[2].level | 2 |
| concepts[2].score | 0.6567530632019043 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q204833 |
| concepts[2].display_name | Enhanced Data Rates for GSM Evolution |
| concepts[3].id | https://openalex.org/C81860439 |
| concepts[3].level | 2 |
| concepts[3].score | 0.570419192314148 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q251212 |
| concepts[3].display_name | Internet of Things |
| concepts[4].id | https://openalex.org/C119857082 |
| concepts[4].level | 1 |
| concepts[4].score | 0.5171982049942017 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q2539 |
| concepts[4].display_name | Machine learning |
| concepts[5].id | https://openalex.org/C138236772 |
| concepts[5].level | 3 |
| concepts[5].score | 0.5118778944015503 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q25098575 |
| concepts[5].display_name | Edge device |
| concepts[6].id | https://openalex.org/C154945302 |
| concepts[6].level | 1 |
| concepts[6].score | 0.4991762638092041 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[6].display_name | Artificial intelligence |
| concepts[7].id | https://openalex.org/C2778456923 |
| concepts[7].level | 3 |
| concepts[7].score | 0.4856392443180084 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q5337692 |
| concepts[7].display_name | Edge computing |
| concepts[8].id | https://openalex.org/C182590292 |
| concepts[8].level | 2 |
| concepts[8].score | 0.4403921663761139 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q989632 |
| concepts[8].display_name | Network security |
| concepts[9].id | https://openalex.org/C9652623 |
| concepts[9].level | 2 |
| concepts[9].score | 0.42709800601005554 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q190109 |
| concepts[9].display_name | Field (mathematics) |
| concepts[10].id | https://openalex.org/C124101348 |
| concepts[10].level | 1 |
| concepts[10].score | 0.3625970780849457 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q172491 |
| concepts[10].display_name | Data mining |
| concepts[11].id | https://openalex.org/C31258907 |
| concepts[11].level | 1 |
| concepts[11].score | 0.3025748133659363 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q1301371 |
| concepts[11].display_name | Computer network |
| concepts[12].id | https://openalex.org/C38652104 |
| concepts[12].level | 1 |
| concepts[12].score | 0.2779364585876465 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[12].display_name | Computer security |
| concepts[13].id | https://openalex.org/C79974875 |
| concepts[13].level | 2 |
| concepts[13].score | 0.09358477592468262 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q483639 |
| concepts[13].display_name | Cloud computing |
| concepts[14].id | https://openalex.org/C33923547 |
| concepts[14].level | 0 |
| concepts[14].score | 0.0 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q395 |
| concepts[14].display_name | Mathematics |
| concepts[15].id | https://openalex.org/C111919701 |
| concepts[15].level | 1 |
| concepts[15].score | 0.0 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q9135 |
| concepts[15].display_name | Operating system |
| concepts[16].id | https://openalex.org/C202444582 |
| concepts[16].level | 1 |
| concepts[16].score | 0.0 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q837863 |
| concepts[16].display_name | Pure mathematics |
| keywords[0].id | https://openalex.org/keywords/computer-science |
| keywords[0].score | 0.8286041021347046 |
| keywords[0].display_name | Computer science |
| keywords[1].id | https://openalex.org/keywords/intrusion-detection-system |
| keywords[1].score | 0.7722063660621643 |
| keywords[1].display_name | Intrusion detection system |
| keywords[2].id | https://openalex.org/keywords/enhanced-data-rates-for-gsm-evolution |
| keywords[2].score | 0.6567530632019043 |
| keywords[2].display_name | Enhanced Data Rates for GSM Evolution |
| keywords[3].id | https://openalex.org/keywords/internet-of-things |
| keywords[3].score | 0.570419192314148 |
| keywords[3].display_name | Internet of Things |
| keywords[4].id | https://openalex.org/keywords/machine-learning |
| keywords[4].score | 0.5171982049942017 |
| keywords[4].display_name | Machine learning |
| keywords[5].id | https://openalex.org/keywords/edge-device |
| keywords[5].score | 0.5118778944015503 |
| keywords[5].display_name | Edge device |
| keywords[6].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[6].score | 0.4991762638092041 |
| keywords[6].display_name | Artificial intelligence |
| keywords[7].id | https://openalex.org/keywords/edge-computing |
| keywords[7].score | 0.4856392443180084 |
| keywords[7].display_name | Edge computing |
| keywords[8].id | https://openalex.org/keywords/network-security |
| keywords[8].score | 0.4403921663761139 |
| keywords[8].display_name | Network security |
| keywords[9].id | https://openalex.org/keywords/field |
| keywords[9].score | 0.42709800601005554 |
| keywords[9].display_name | Field (mathematics) |
| keywords[10].id | https://openalex.org/keywords/data-mining |
| keywords[10].score | 0.3625970780849457 |
| keywords[10].display_name | Data mining |
| keywords[11].id | https://openalex.org/keywords/computer-network |
| keywords[11].score | 0.3025748133659363 |
| keywords[11].display_name | Computer network |
| keywords[12].id | https://openalex.org/keywords/computer-security |
| keywords[12].score | 0.2779364585876465 |
| keywords[12].display_name | Computer security |
| keywords[13].id | https://openalex.org/keywords/cloud-computing |
| keywords[13].score | 0.09358477592468262 |
| keywords[13].display_name | Cloud computing |
| language | |
| locations[0].id | pmh:oai:arXiv.org:2111.01383 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4306400194 |
| locations[0].source.issn | |
| locations[0].source.type | repository |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | |
| locations[0].source.is_core | False |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | arXiv (Cornell University) |
| locations[0].source.host_organization | https://openalex.org/I205783295 |
| locations[0].source.host_organization_name | Cornell University |
| locations[0].source.host_organization_lineage | https://openalex.org/I205783295 |
| locations[0].license | |
| locations[0].pdf_url | https://arxiv.org/pdf/2111.01383 |
| locations[0].version | submittedVersion |
| locations[0].raw_type | |
| locations[0].license_id | |
| locations[0].is_accepted | False |
| locations[0].is_published | False |
| locations[0].raw_source_name | |
| locations[0].landing_page_url | http://arxiv.org/abs/2111.01383 |
| indexed_in | arxiv |
| authorships[0].author.id | https://openalex.org/A5052319000 |
| authorships[0].author.orcid | https://orcid.org/0000-0001-9414-3464 |
| authorships[0].author.display_name | Poornima Mahadevappa |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Mahadevappa, Poornima |
| authorships[0].is_corresponding | False |
| authorships[1].author.id | https://openalex.org/A5065807238 |
| authorships[1].author.orcid | https://orcid.org/0000-0003-2960-1814 |
| authorships[1].author.display_name | Syeda Mariam Muzammal |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Muzammal, Syeda Mariam |
| authorships[1].is_corresponding | False |
| authorships[2].author.id | https://openalex.org/A5062919173 |
| authorships[2].author.orcid | https://orcid.org/0000-0001-9500-1361 |
| authorships[2].author.display_name | Raja Kumar Murugesan |
| authorships[2].author_position | last |
| authorships[2].raw_author_name | Murugesan, Raja Kumar |
| authorships[2].is_corresponding | False |
| has_content.pdf | False |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://arxiv.org/pdf/2111.01383 |
| open_access.oa_status | green |
| open_access.any_repository_has_fulltext | False |
| created_date | 2022-05-05T00:00:00 |
| display_name | A Comparative Analysis of Machine Learning Algorithms for Intrusion\n Detection in Edge-Enabled IoT Networks |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-10-24T21:50:52.558619 |
| primary_topic.id | https://openalex.org/T10400 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9991999864578247 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1705 |
| primary_topic.subfield.display_name | Computer Networks and Communications |
| primary_topic.display_name | Network Security and Intrusion Detection |
| related_works | https://openalex.org/W2061466315, https://openalex.org/W2376886931, https://openalex.org/W1992118813, https://openalex.org/W2010561419, https://openalex.org/W4322761281, https://openalex.org/W2374845301, https://openalex.org/W2351448539, https://openalex.org/W1977863481, https://openalex.org/W4238233472, https://openalex.org/W2384741105 |
| cited_by_count | 3 |
| counts_by_year[0].year | 2024 |
| counts_by_year[0].cited_by_count | 2 |
| counts_by_year[1].year | 2023 |
| counts_by_year[1].cited_by_count | 1 |
| locations_count | 1 |
| best_oa_location.id | pmh:oai:arXiv.org:2111.01383 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4306400194 |
| best_oa_location.source.issn | |
| best_oa_location.source.type | repository |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | |
| best_oa_location.source.is_core | False |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | arXiv (Cornell University) |
| best_oa_location.source.host_organization | https://openalex.org/I205783295 |
| best_oa_location.source.host_organization_name | Cornell University |
| best_oa_location.source.host_organization_lineage | https://openalex.org/I205783295 |
| best_oa_location.license | |
| best_oa_location.pdf_url | https://arxiv.org/pdf/2111.01383 |
| best_oa_location.version | submittedVersion |
| best_oa_location.raw_type | |
| best_oa_location.license_id | |
| best_oa_location.is_accepted | False |
| best_oa_location.is_published | False |
| best_oa_location.raw_source_name | |
| best_oa_location.landing_page_url | http://arxiv.org/abs/2111.01383 |
| primary_location.id | pmh:oai:arXiv.org:2111.01383 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4306400194 |
| primary_location.source.issn | |
| primary_location.source.type | repository |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | |
| primary_location.source.is_core | False |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | arXiv (Cornell University) |
| primary_location.source.host_organization | https://openalex.org/I205783295 |
| primary_location.source.host_organization_name | Cornell University |
| primary_location.source.host_organization_lineage | https://openalex.org/I205783295 |
| primary_location.license | |
| primary_location.pdf_url | https://arxiv.org/pdf/2111.01383 |
| primary_location.version | submittedVersion |
| primary_location.raw_type | |
| primary_location.license_id | |
| primary_location.is_accepted | False |
| primary_location.is_published | False |
| primary_location.raw_source_name | |
| primary_location.landing_page_url | http://arxiv.org/abs/2111.01383 |
| publication_date | 2021-11-02 |
| publication_year | 2021 |
| referenced_works_count | 0 |
| abstract_inverted_index.A | 0 |
| abstract_inverted_index.a | 182 |
| abstract_inverted_index.In | 126 |
| abstract_inverted_index.It | 151 |
| abstract_inverted_index.be | 153, 175 |
| abstract_inverted_index.by | 46 |
| abstract_inverted_index.in | 3, 73, 98, 115, 121 |
| abstract_inverted_index.is | 28, 63, 92 |
| abstract_inverted_index.of | 6, 24, 33, 94, 131, 186, 191 |
| abstract_inverted_index.on | 144, 148, 167 |
| abstract_inverted_index.to | 17, 68, 81, 139 |
| abstract_inverted_index.1.2 | 187 |
| abstract_inverted_index.IoT | 44, 75, 123, 179 |
| abstract_inverted_index.MLP | 173 |
| abstract_inverted_index.The | 39, 77, 103 |
| abstract_inverted_index.and | 9, 20, 88, 162, 164 |
| abstract_inverted_index.are | 79 |
| abstract_inverted_index.can | 152, 174 |
| abstract_inverted_index.for | 169 |
| abstract_inverted_index.has | 14, 42, 106 |
| abstract_inverted_index.one | 93 |
| abstract_inverted_index.the | 4, 51, 64, 70, 83, 95, 99, 112, 141 |
| abstract_inverted_index.(ML) | 59 |
| abstract_inverted_index.area | 100 |
| abstract_inverted_index.been | 137 |
| abstract_inverted_index.data | 52 |
| abstract_inverted_index.into | 86 |
| abstract_inverted_index.many | 108 |
| abstract_inverted_index.more | 166, 176 |
| abstract_inverted_index.most | 65 |
| abstract_inverted_index.near | 50 |
| abstract_inverted_index.rise | 16 |
| abstract_inverted_index.that | 155 |
| abstract_inverted_index.this | 127 |
| abstract_inverted_index.time | 185 |
| abstract_inverted_index.used | 80 |
| abstract_inverted_index.with | 181 |
| abstract_inverted_index.(IoT) | 26 |
| abstract_inverted_index.Among | 54 |
| abstract_inverted_index.based | 60 |
| abstract_inverted_index.daily | 34 |
| abstract_inverted_index.every | 31 |
| abstract_inverted_index.field | 32 |
| abstract_inverted_index.given | 15 |
| abstract_inverted_index.input | 161 |
| abstract_inverted_index.life, | 35 |
| abstract_inverted_index.tool. | 150 |
| abstract_inverted_index.79%.\n | 192 |
| abstract_inverted_index.Things | 25 |
| abstract_inverted_index.almost | 30 |
| abstract_inverted_index.better | 183 |
| abstract_inverted_index.combat | 69 |
| abstract_inverted_index.exist. | 125 |
| abstract_inverted_index.issues | 97 |
| abstract_inverted_index.moving | 47 |
| abstract_inverted_index.normal | 87 |
| abstract_inverted_index.number | 5 |
| abstract_inverted_index.output | 163 |
| abstract_inverted_index.paper, | 128 |
| abstract_inverted_index.relies | 165 |
| abstract_inverted_index.NSL-KDD | 145 |
| abstract_inverted_index.Pycharm | 149 |
| abstract_inverted_index.between | 160 |
| abstract_inverted_index.dataset | 146 |
| abstract_inverted_index.devices | 8 |
| abstract_inverted_index.machine | 133 |
| abstract_inverted_index.network | 84, 142 |
| abstract_inverted_index.seconds | 188 |
| abstract_inverted_index.through | 11 |
| abstract_inverted_index.traffic | 85, 143 |
| abstract_inverted_index.various | 18, 55 |
| abstract_inverted_index.However, | 111 |
| abstract_inverted_index.Internet | 23 |
| abstract_inverted_index.Learning | 58 |
| abstract_inverted_index.accuracy | 190 |
| abstract_inverted_index.analysis | 130 |
| abstract_inverted_index.behavior | 72 |
| abstract_inverted_index.classify | 82 |
| abstract_inverted_index.increase | 2 |
| abstract_inverted_index.involved | 114 |
| abstract_inverted_index.learning | 134 |
| abstract_inverted_index.networks | 13, 124, 180 |
| abstract_inverted_index.observed | 154 |
| abstract_inverted_index.paradigm | 41 |
| abstract_inverted_index.proposed | 107 |
| abstract_inverted_index.research | 104 |
| abstract_inverted_index.security | 21, 56, 120 |
| abstract_inverted_index.sources. | 53 |
| abstract_inverted_index.suitable | 117 |
| abstract_inverted_index.training | 184 |
| abstract_inverted_index.wireless | 12 |
| abstract_inverted_index.Intrusion | 90 |
| abstract_inverted_index.anomalous | 71 |
| abstract_inverted_index.community | 105 |
| abstract_inverted_index.concerns. | 22 |
| abstract_inverted_index.detection | 62, 91 |
| abstract_inverted_index.including | 36 |
| abstract_inverted_index.intrusion | 61, 109, 170 |
| abstract_inverted_index.networks. | 76 |
| abstract_inverted_index.performed | 138 |
| abstract_inverted_index.security. | 102 |
| abstract_inverted_index.selecting | 116 |
| abstract_inverted_index.sensitive | 37 |
| abstract_inverted_index.(MLP)\nhas | 158 |
| abstract_inverted_index.Perception | 157 |
| abstract_inverted_index.Therefore, | 172 |
| abstract_inverted_index.categorize | 140 |
| abstract_inverted_index.challenges | 113 |
| abstract_inverted_index.detection. | 171 |
| abstract_inverted_index.edge-based | 178 |
| abstract_inverted_index.processing | 49 |
| abstract_inverted_index.Multi-Layer | 156 |
| abstract_inverted_index.challenging | 96 |
| abstract_inverted_index.conceivable | 66 |
| abstract_inverted_index.of\nnetwork | 101 |
| abstract_inverted_index.significant | 1 |
| abstract_inverted_index.to\nprovide | 119 |
| abstract_inverted_index.algorithm(s) | 118 |
| abstract_inverted_index.and\ntesting | 189 |
| abstract_inverted_index.applications | 27, 45 |
| abstract_inverted_index.complemented | 43 |
| abstract_inverted_index.conventional | 132 |
| abstract_inverted_index.dependencies | 159 |
| abstract_inverted_index.deployed\nin | 29 |
| abstract_inverted_index.edge-enabled | 74, 122 |
| abstract_inverted_index.environments. | 38 |
| abstract_inverted_index.ML\nalgorithms | 78 |
| abstract_inverted_index.a\ncomparative | 129 |
| abstract_inverted_index.classification | 135 |
| abstract_inverted_index.interconnected | 7 |
| abstract_inverted_index.using\nJupyter | 147 |
| abstract_inverted_index.algorithms\nhas | 136 |
| abstract_inverted_index.edge\ncomputing | 40 |
| abstract_inverted_index.threats,\nrisks | 19 |
| abstract_inverted_index.appropriate\nfor | 177 |
| abstract_inverted_index.models,\nMachine | 57 |
| abstract_inverted_index.defense\nmechanism | 67 |
| abstract_inverted_index.the\ncomputational | 48 |
| abstract_inverted_index.data\ncommunication | 10 |
| abstract_inverted_index.detection\nsystems. | 110 |
| abstract_inverted_index.malicious\nattacks. | 89 |
| abstract_inverted_index.network\nconfiguration | 168 |
| cited_by_percentile_year.max | 96 |
| cited_by_percentile_year.min | 89 |
| countries_distinct_count | 0 |
| institutions_distinct_count | 3 |
| citation_normalized_percentile.value | 0.68207103 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |