A data quarantine model to secure data in edge computing Article Swipe
 YOU?
·
· 2022
· Open Access
·
· DOI: https://doi.org/10.11591/ijece.v12i3.pp3309-3319
YOU?
·
· 2022
· Open Access
·
· DOI: https://doi.org/10.11591/ijece.v12i3.pp3309-3319
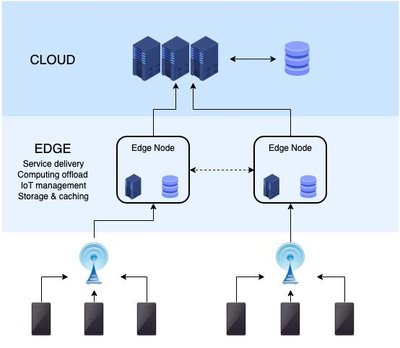
Edge computing provides an agile data processing platform for latency-sensitive and communication-intensive applications through a decentralized cloud and geographically distributed edge nodes. Gaining centralized control over the edge nodes can be challenging due to security issues and threats. Among several security issues, data integrity attacks can lead to inconsistent data and intrude edge data analytics. Further intensification of the attack makes it challenging to mitigate and identify the root cause. Therefore, this paper proposes a new concept of data quarantine model to mitigate data integrity attacks by quarantining intruders. The efficient security solutions in cloud, ad-hoc networks, and computer systems using quarantine have motivated adopting it in edge computing. The data acquisition edge nodes identify the intruders and quarantine all the suspected devices through dimensionality reduction. During quarantine, the proposed concept builds the reputation scores to determine the falsely identified legitimate devices and sanitize their affected data to regain data integrity. As a preliminary investigation, this work identifies an appropriate machine learning method, linear discriminant analysis (LDA), for dimensionality reduction. The LDA results in 72.83% quarantine accuracy and 0.9 seconds training time, which is efficient than other state-of-the-art methods. In future, this would be implemented and validated with ground truth data.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.11591/ijece.v12i3.pp3309-3319
- https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718
- OA Status
- diamond
- Cited By
- 4
- References
- 26
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W3213439587
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W3213439587Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.11591/ijece.v12i3.pp3309-3319Digital Object Identifier
- Title
-
A data quarantine model to secure data in edge computingWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2022Year of publication
- Publication date
-
2022-03-14Full publication date if available
- Authors
-
Poornima Mahadevappa, Raja Kumar MurugesanList of authors in order
- Landing page
-
https://doi.org/10.11591/ijece.v12i3.pp3309-3319Publisher landing page
- PDF URL
-
https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718Direct link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
diamondOpen access status per OpenAlex
- OA URL
-
https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718Direct OA link when available
- Concepts
-
Computer science, Enhanced Data Rates for GSM Evolution, Computer security, Cloud computing, Edge computing, Malware, Artificial intelligence, Operating systemTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
4Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 2, 2023: 1, 2022: 1Per-year citation counts (last 5 years)
- References (count)
-
26Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W3213439587 |
|---|---|
| doi | https://doi.org/10.11591/ijece.v12i3.pp3309-3319 |
| ids.doi | https://doi.org/10.11591/ijece.v12i3.pp3309-3319 |
| ids.mag | 3213439587 |
| ids.openalex | https://openalex.org/W3213439587 |
| fwci | 0.78319528 |
| type | article |
| title | A data quarantine model to secure data in edge computing |
| biblio.issue | 3 |
| biblio.volume | 12 |
| biblio.last_page | 3309 |
| biblio.first_page | 3309 |
| topics[0].id | https://openalex.org/T10764 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.993399977684021 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1702 |
| topics[0].subfield.display_name | Artificial Intelligence |
| topics[0].display_name | Privacy-Preserving Technologies in Data |
| topics[1].id | https://openalex.org/T10273 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9930999875068665 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1705 |
| topics[1].subfield.display_name | Computer Networks and Communications |
| topics[1].display_name | IoT and Edge/Fog Computing |
| topics[2].id | https://openalex.org/T11614 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9929999709129333 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1710 |
| topics[2].subfield.display_name | Information Systems |
| topics[2].display_name | Cloud Data Security Solutions |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C41008148 |
| concepts[0].level | 0 |
| concepts[0].score | 0.7803350687026978 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[0].display_name | Computer science |
| concepts[1].id | https://openalex.org/C162307627 |
| concepts[1].level | 2 |
| concepts[1].score | 0.5528768301010132 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q204833 |
| concepts[1].display_name | Enhanced Data Rates for GSM Evolution |
| concepts[2].id | https://openalex.org/C38652104 |
| concepts[2].level | 1 |
| concepts[2].score | 0.5514347553253174 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[2].display_name | Computer security |
| concepts[3].id | https://openalex.org/C79974875 |
| concepts[3].level | 2 |
| concepts[3].score | 0.5431877374649048 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q483639 |
| concepts[3].display_name | Cloud computing |
| concepts[4].id | https://openalex.org/C2778456923 |
| concepts[4].level | 3 |
| concepts[4].score | 0.5416463017463684 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q5337692 |
| concepts[4].display_name | Edge computing |
| concepts[5].id | https://openalex.org/C541664917 |
| concepts[5].level | 2 |
| concepts[5].score | 0.4616957902908325 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q14001 |
| concepts[5].display_name | Malware |
| concepts[6].id | https://openalex.org/C154945302 |
| concepts[6].level | 1 |
| concepts[6].score | 0.17664304375648499 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[6].display_name | Artificial intelligence |
| concepts[7].id | https://openalex.org/C111919701 |
| concepts[7].level | 1 |
| concepts[7].score | 0.0937919020652771 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q9135 |
| concepts[7].display_name | Operating system |
| keywords[0].id | https://openalex.org/keywords/computer-science |
| keywords[0].score | 0.7803350687026978 |
| keywords[0].display_name | Computer science |
| keywords[1].id | https://openalex.org/keywords/enhanced-data-rates-for-gsm-evolution |
| keywords[1].score | 0.5528768301010132 |
| keywords[1].display_name | Enhanced Data Rates for GSM Evolution |
| keywords[2].id | https://openalex.org/keywords/computer-security |
| keywords[2].score | 0.5514347553253174 |
| keywords[2].display_name | Computer security |
| keywords[3].id | https://openalex.org/keywords/cloud-computing |
| keywords[3].score | 0.5431877374649048 |
| keywords[3].display_name | Cloud computing |
| keywords[4].id | https://openalex.org/keywords/edge-computing |
| keywords[4].score | 0.5416463017463684 |
| keywords[4].display_name | Edge computing |
| keywords[5].id | https://openalex.org/keywords/malware |
| keywords[5].score | 0.4616957902908325 |
| keywords[5].display_name | Malware |
| keywords[6].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[6].score | 0.17664304375648499 |
| keywords[6].display_name | Artificial intelligence |
| keywords[7].id | https://openalex.org/keywords/operating-system |
| keywords[7].score | 0.0937919020652771 |
| keywords[7].display_name | Operating system |
| language | en |
| locations[0].id | doi:10.11591/ijece.v12i3.pp3309-3319 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210235676 |
| locations[0].source.issn | 2722-256X, 2722-2578 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2722-256X |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | International Journal of Power Electronics and Drive Systems/International Journal of Electrical and Computer Engineering |
| locations[0].source.host_organization | https://openalex.org/P4310315009 |
| locations[0].source.host_organization_name | Institute of Advanced Engineering and Science (IAES) |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310315009 |
| locations[0].source.host_organization_lineage_names | Institute of Advanced Engineering and Science (IAES) |
| locations[0].license | |
| locations[0].pdf_url | https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718 |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | International Journal of Electrical and Computer Engineering (IJECE) |
| locations[0].landing_page_url | https://doi.org/10.11591/ijece.v12i3.pp3309-3319 |
| indexed_in | crossref |
| authorships[0].author.id | https://openalex.org/A5052319000 |
| authorships[0].author.orcid | https://orcid.org/0000-0001-9414-3464 |
| authorships[0].author.display_name | Poornima Mahadevappa |
| authorships[0].countries | MY |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I4210143550 |
| authorships[0].affiliations[0].raw_affiliation_string | Taylor's University |
| authorships[0].institutions[0].id | https://openalex.org/I4210143550 |
| authorships[0].institutions[0].ror | https://ror.org/0498pcx51 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I4210143550 |
| authorships[0].institutions[0].country_code | MY |
| authorships[0].institutions[0].display_name | Taylor's University |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Poornima Mahadevappa |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Taylor's University |
| authorships[1].author.id | https://openalex.org/A5062919173 |
| authorships[1].author.orcid | https://orcid.org/0000-0001-9500-1361 |
| authorships[1].author.display_name | Raja Kumar Murugesan |
| authorships[1].countries | MY |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I4210143550 |
| authorships[1].affiliations[0].raw_affiliation_string | Taylor's University |
| authorships[1].institutions[0].id | https://openalex.org/I4210143550 |
| authorships[1].institutions[0].ror | https://ror.org/0498pcx51 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I4210143550 |
| authorships[1].institutions[0].country_code | MY |
| authorships[1].institutions[0].display_name | Taylor's University |
| authorships[1].author_position | last |
| authorships[1].raw_author_name | Raja Kumar Murugesan |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Taylor's University |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718 |
| open_access.oa_status | diamond |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | A data quarantine model to secure data in edge computing |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10764 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.993399977684021 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1702 |
| primary_topic.subfield.display_name | Artificial Intelligence |
| primary_topic.display_name | Privacy-Preserving Technologies in Data |
| related_works | https://openalex.org/W2097492617, https://openalex.org/W2753240997, https://openalex.org/W4366249425, https://openalex.org/W2995938785, https://openalex.org/W2979760315, https://openalex.org/W4324372666, https://openalex.org/W4225706866, https://openalex.org/W4386004629, https://openalex.org/W2942586735, https://openalex.org/W2956163139 |
| cited_by_count | 4 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 2 |
| counts_by_year[1].year | 2023 |
| counts_by_year[1].cited_by_count | 1 |
| counts_by_year[2].year | 2022 |
| counts_by_year[2].cited_by_count | 1 |
| locations_count | 1 |
| best_oa_location.id | doi:10.11591/ijece.v12i3.pp3309-3319 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210235676 |
| best_oa_location.source.issn | 2722-256X, 2722-2578 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2722-256X |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | International Journal of Power Electronics and Drive Systems/International Journal of Electrical and Computer Engineering |
| best_oa_location.source.host_organization | https://openalex.org/P4310315009 |
| best_oa_location.source.host_organization_name | Institute of Advanced Engineering and Science (IAES) |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310315009 |
| best_oa_location.source.host_organization_lineage_names | Institute of Advanced Engineering and Science (IAES) |
| best_oa_location.license | |
| best_oa_location.pdf_url | https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718 |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | International Journal of Electrical and Computer Engineering (IJECE) |
| best_oa_location.landing_page_url | https://doi.org/10.11591/ijece.v12i3.pp3309-3319 |
| primary_location.id | doi:10.11591/ijece.v12i3.pp3309-3319 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210235676 |
| primary_location.source.issn | 2722-256X, 2722-2578 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2722-256X |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | International Journal of Power Electronics and Drive Systems/International Journal of Electrical and Computer Engineering |
| primary_location.source.host_organization | https://openalex.org/P4310315009 |
| primary_location.source.host_organization_name | Institute of Advanced Engineering and Science (IAES) |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310315009 |
| primary_location.source.host_organization_lineage_names | Institute of Advanced Engineering and Science (IAES) |
| primary_location.license | |
| primary_location.pdf_url | https://ijece.iaescore.com/index.php/IJECE/article/download/26383/15718 |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | International Journal of Electrical and Computer Engineering (IJECE) |
| primary_location.landing_page_url | https://doi.org/10.11591/ijece.v12i3.pp3309-3319 |
| publication_date | 2022-03-14 |
| publication_year | 2022 |
| referenced_works | https://openalex.org/W3109171007, https://openalex.org/W3009005210, https://openalex.org/W2753672491, https://openalex.org/W2747548784, https://openalex.org/W2144114227, https://openalex.org/W6757716706, https://openalex.org/W2971110943, https://openalex.org/W2906631955, https://openalex.org/W3008428105, https://openalex.org/W2751045880, https://openalex.org/W3095933406, https://openalex.org/W2794596638, https://openalex.org/W3126409715, https://openalex.org/W1985719683, https://openalex.org/W2912230279, https://openalex.org/W2787594205, https://openalex.org/W3039598638, https://openalex.org/W2982626544, https://openalex.org/W3009406405, https://openalex.org/W3004476180, https://openalex.org/W2969579839, https://openalex.org/W3015392420, https://openalex.org/W3019580018, https://openalex.org/W3022260003, https://openalex.org/W2956755329, https://openalex.org/W2906918936 |
| referenced_works_count | 26 |
| abstract_inverted_index.a | 14, 74, 152 |
| abstract_inverted_index.As | 151 |
| abstract_inverted_index.In | 189 |
| abstract_inverted_index.an | 3, 158 |
| abstract_inverted_index.be | 30, 193 |
| abstract_inverted_index.by | 86 |
| abstract_inverted_index.in | 93, 106, 173 |
| abstract_inverted_index.is | 183 |
| abstract_inverted_index.it | 61, 105 |
| abstract_inverted_index.of | 57, 77 |
| abstract_inverted_index.to | 33, 47, 63, 81, 135, 147 |
| abstract_inverted_index.0.9 | 178 |
| abstract_inverted_index.LDA | 171 |
| abstract_inverted_index.The | 89, 109, 170 |
| abstract_inverted_index.all | 119 |
| abstract_inverted_index.and | 10, 17, 36, 50, 65, 97, 117, 142, 177, 195 |
| abstract_inverted_index.can | 29, 45 |
| abstract_inverted_index.due | 32 |
| abstract_inverted_index.for | 8, 167 |
| abstract_inverted_index.new | 75 |
| abstract_inverted_index.the | 26, 58, 67, 115, 120, 128, 132, 137 |
| abstract_inverted_index.data | 5, 42, 49, 53, 78, 83, 110, 146, 149 |
| abstract_inverted_index.edge | 20, 27, 52, 107, 112 |
| abstract_inverted_index.have | 102 |
| abstract_inverted_index.lead | 46 |
| abstract_inverted_index.over | 25 |
| abstract_inverted_index.root | 68 |
| abstract_inverted_index.than | 185 |
| abstract_inverted_index.this | 71, 155, 191 |
| abstract_inverted_index.with | 197 |
| abstract_inverted_index.work | 156 |
| abstract_inverted_index.Among | 38 |
| abstract_inverted_index.agile | 4 |
| abstract_inverted_index.cloud | 16 |
| abstract_inverted_index.makes | 60 |
| abstract_inverted_index.model | 80 |
| abstract_inverted_index.nodes | 28, 113 |
| abstract_inverted_index.other | 186 |
| abstract_inverted_index.paper | 72 |
| abstract_inverted_index.their | 144 |
| abstract_inverted_index.time, | 181 |
| abstract_inverted_index.truth | 199 |
| abstract_inverted_index.using | 100 |
| abstract_inverted_index.which | 182 |
| abstract_inverted_index.would | 192 |
| abstract_inverted_index.(LDA), | 166 |
| abstract_inverted_index.72.83% | 174 |
| abstract_inverted_index.During | 126 |
| abstract_inverted_index.ad-hoc | 95 |
| abstract_inverted_index.attack | 59 |
| abstract_inverted_index.builds | 131 |
| abstract_inverted_index.cause. | 69 |
| abstract_inverted_index.cloud, | 94 |
| abstract_inverted_index.ground | 198 |
| abstract_inverted_index.issues | 35 |
| abstract_inverted_index.linear | 163 |
| abstract_inverted_index.nodes. | 21 |
| abstract_inverted_index.regain | 148 |
| abstract_inverted_index.scores | 134 |
| abstract_inverted_index.Further | 55 |
| abstract_inverted_index.Gaining | 22 |
| abstract_inverted_index.attacks | 44, 85 |
| abstract_inverted_index.concept | 76, 130 |
| abstract_inverted_index.control | 24 |
| abstract_inverted_index.devices | 122, 141 |
| abstract_inverted_index.falsely | 138 |
| abstract_inverted_index.future, | 190 |
| abstract_inverted_index.intrude | 51 |
| abstract_inverted_index.issues, | 41 |
| abstract_inverted_index.machine | 160 |
| abstract_inverted_index.method, | 162 |
| abstract_inverted_index.results | 172 |
| abstract_inverted_index.seconds | 179 |
| abstract_inverted_index.several | 39 |
| abstract_inverted_index.systems | 99 |
| abstract_inverted_index.through | 13, 123 |
| abstract_inverted_index.accuracy | 176 |
| abstract_inverted_index.adopting | 104 |
| abstract_inverted_index.affected | 145 |
| abstract_inverted_index.analysis | 165 |
| abstract_inverted_index.computer | 98 |
| abstract_inverted_index.identify | 66, 114 |
| abstract_inverted_index.learning | 161 |
| abstract_inverted_index.methods. | 188 |
| abstract_inverted_index.mitigate | 64, 82 |
| abstract_inverted_index.platform | 7 |
| abstract_inverted_index.proposed | 129 |
| abstract_inverted_index.proposes | 73 |
| abstract_inverted_index.provides | 2 |
| abstract_inverted_index.sanitize | 143 |
| abstract_inverted_index.security | 34, 40, 91 |
| abstract_inverted_index.threats. | 37 |
| abstract_inverted_index.training | 180 |
| abstract_inverted_index.computing | 1 |
| abstract_inverted_index.determine | 136 |
| abstract_inverted_index.efficient | 90, 184 |
| abstract_inverted_index.integrity | 43, 84 |
| abstract_inverted_index.intruders | 116 |
| abstract_inverted_index.motivated | 103 |
| abstract_inverted_index.networks, | 96 |
| abstract_inverted_index.solutions | 92 |
| abstract_inverted_index.suspected | 121 |
| abstract_inverted_index.validated | 196 |
| abstract_inverted_index.Therefore, | 70 |
| abstract_inverted_index.analytics. | 54 |
| abstract_inverted_index.computing. | 108 |
| abstract_inverted_index.identified | 139 |
| abstract_inverted_index.identifies | 157 |
| abstract_inverted_index.integrity. | 150 |
| abstract_inverted_index.intruders. | 88 |
| abstract_inverted_index.legitimate | 140 |
| abstract_inverted_index.processing | 6 |
| abstract_inverted_index.quarantine | 79, 101, 118, 175 |
| abstract_inverted_index.reduction. | 125, 169 |
| abstract_inverted_index.reputation | 133 |
| abstract_inverted_index.acquisition | 111 |
| abstract_inverted_index.appropriate | 159 |
| abstract_inverted_index.centralized | 23 |
| abstract_inverted_index.challenging | 31, 62 |
| abstract_inverted_index.distributed | 19 |
| abstract_inverted_index.implemented | 194 |
| abstract_inverted_index.preliminary | 153 |
| abstract_inverted_index.quarantine, | 127 |
| abstract_inverted_index.applications | 12 |
| abstract_inverted_index.discriminant | 164 |
| abstract_inverted_index.inconsistent | 48 |
| abstract_inverted_index.quarantining | 87 |
| abstract_inverted_index.<p>Edge | 0 |
| abstract_inverted_index.decentralized | 15 |
| abstract_inverted_index.dimensionality | 124, 168 |
| abstract_inverted_index.geographically | 18 |
| abstract_inverted_index.investigation, | 154 |
| abstract_inverted_index.data.</p> | 200 |
| abstract_inverted_index.intensification | 56 |
| abstract_inverted_index.state-of-the-art | 187 |
| abstract_inverted_index.latency-sensitive | 9 |
| abstract_inverted_index.communication-intensive | 11 |
| cited_by_percentile_year.max | 97 |
| cited_by_percentile_year.min | 89 |
| countries_distinct_count | 1 |
| institutions_distinct_count | 2 |
| sustainable_development_goals[0].id | https://metadata.un.org/sdg/10 |
| sustainable_development_goals[0].score | 0.5299999713897705 |
| sustainable_development_goals[0].display_name | Reduced inequalities |
| sustainable_development_goals[1].id | https://metadata.un.org/sdg/16 |
| sustainable_development_goals[1].score | 0.41999998688697815 |
| sustainable_development_goals[1].display_name | Peace, Justice and strong institutions |
| citation_normalized_percentile.value | 0.7066038 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |