A Hybrid Model for Detecting Phishing Attack Using Recommedation Decision Trees Article Swipe
 YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.1051/itmconf/20235701018
YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.1051/itmconf/20235701018
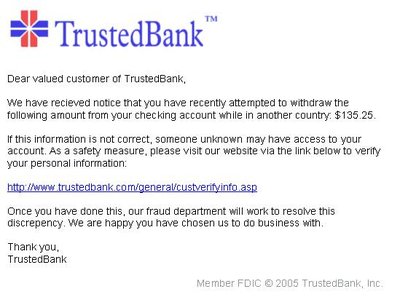
Phishing performs by trying to trick the victim into accessing any computing information which looks original, then instructing them to send important data to unrestricted/unwanted privacy resource. For prevention, it is essential to develop a phishing detection system. Recent phishing detection systems are based on data mining and machine learning techniques. Most of the related work literature require collection of previous phishing attack logs, analyze them and create a list of such activities and block traffic from such sources. But this is a cumbersome task because the data size is very large, continue changing and dynamic nature. [1]. Instead of using single algorithm approach it would be better to use a hybrid approach. A hybrid approach would be better at mitigating phishing attacks because classification of different format of data is handled; whether the intruder want to use images or textural input to gain into another user system for phishing. Hybrid recommendation decision tress enhances any of machine learning and deep learning algorithms performance. The decision path of the model followed a series of if/else/then statements that connect the predicted class from the root of the tree through the branches of the tree to detect true positive and false negatives of phishing attempts. 10 decision trees were considered and used the features to train the recommendation decision regression model. The developed hybrid recommendation decision tree approach provided an overall true positive rate of the model of 92.28 % and false negative rate is 7.4%.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.1051/itmconf/20235701018
- https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdf
- OA Status
- diamond
- References
- 10
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4388578736
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4388578736Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1051/itmconf/20235701018Digital Object Identifier
- Title
-
A Hybrid Model for Detecting Phishing Attack Using Recommedation Decision TreesWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2023Year of publication
- Publication date
-
2023-01-01Full publication date if available
- Authors
-
Duncan Eric O. Ogonji, Wilson Cheruiyot, Waweru MwangiList of authors in order
- Landing page
-
https://doi.org/10.1051/itmconf/20235701018Publisher landing page
- PDF URL
-
https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdfDirect link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
diamondOpen access status per OpenAlex
- OA URL
-
https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdfDirect OA link when available
- Concepts
-
Phishing, Computer science, Decision tree, Machine learning, Artificial intelligence, Data mining, Tree (set theory), Decision tree learning, The Internet, World Wide Web, Mathematical analysis, MathematicsTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
0Total citation count in OpenAlex
- References (count)
-
10Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4388578736 |
|---|---|
| doi | https://doi.org/10.1051/itmconf/20235701018 |
| ids.doi | https://doi.org/10.1051/itmconf/20235701018 |
| ids.openalex | https://openalex.org/W4388578736 |
| fwci | 0.0 |
| type | article |
| title | A Hybrid Model for Detecting Phishing Attack Using Recommedation Decision Trees |
| biblio.issue | |
| biblio.volume | 57 |
| biblio.last_page | 01018 |
| biblio.first_page | 01018 |
| topics[0].id | https://openalex.org/T11644 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9991000294685364 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1710 |
| topics[0].subfield.display_name | Information Systems |
| topics[0].display_name | Spam and Phishing Detection |
| topics[1].id | https://openalex.org/T10400 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9886000156402588 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1705 |
| topics[1].subfield.display_name | Computer Networks and Communications |
| topics[1].display_name | Network Security and Intrusion Detection |
| topics[2].id | https://openalex.org/T11448 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9857000112533569 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1707 |
| topics[2].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[2].display_name | Face recognition and analysis |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C83860907 |
| concepts[0].level | 3 |
| concepts[0].score | 0.8234357237815857 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q135005 |
| concepts[0].display_name | Phishing |
| concepts[1].id | https://openalex.org/C41008148 |
| concepts[1].level | 0 |
| concepts[1].score | 0.7872915267944336 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[1].display_name | Computer science |
| concepts[2].id | https://openalex.org/C84525736 |
| concepts[2].level | 2 |
| concepts[2].score | 0.7842658162117004 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q831366 |
| concepts[2].display_name | Decision tree |
| concepts[3].id | https://openalex.org/C119857082 |
| concepts[3].level | 1 |
| concepts[3].score | 0.6407691240310669 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q2539 |
| concepts[3].display_name | Machine learning |
| concepts[4].id | https://openalex.org/C154945302 |
| concepts[4].level | 1 |
| concepts[4].score | 0.5542508959770203 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[4].display_name | Artificial intelligence |
| concepts[5].id | https://openalex.org/C124101348 |
| concepts[5].level | 1 |
| concepts[5].score | 0.5004010200500488 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q172491 |
| concepts[5].display_name | Data mining |
| concepts[6].id | https://openalex.org/C113174947 |
| concepts[6].level | 2 |
| concepts[6].score | 0.4978935718536377 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q2859736 |
| concepts[6].display_name | Tree (set theory) |
| concepts[7].id | https://openalex.org/C5481197 |
| concepts[7].level | 3 |
| concepts[7].score | 0.46841898560523987 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q16766476 |
| concepts[7].display_name | Decision tree learning |
| concepts[8].id | https://openalex.org/C110875604 |
| concepts[8].level | 2 |
| concepts[8].score | 0.15105998516082764 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q75 |
| concepts[8].display_name | The Internet |
| concepts[9].id | https://openalex.org/C136764020 |
| concepts[9].level | 1 |
| concepts[9].score | 0.14010319113731384 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q466 |
| concepts[9].display_name | World Wide Web |
| concepts[10].id | https://openalex.org/C134306372 |
| concepts[10].level | 1 |
| concepts[10].score | 0.0 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q7754 |
| concepts[10].display_name | Mathematical analysis |
| concepts[11].id | https://openalex.org/C33923547 |
| concepts[11].level | 0 |
| concepts[11].score | 0.0 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q395 |
| concepts[11].display_name | Mathematics |
| keywords[0].id | https://openalex.org/keywords/phishing |
| keywords[0].score | 0.8234357237815857 |
| keywords[0].display_name | Phishing |
| keywords[1].id | https://openalex.org/keywords/computer-science |
| keywords[1].score | 0.7872915267944336 |
| keywords[1].display_name | Computer science |
| keywords[2].id | https://openalex.org/keywords/decision-tree |
| keywords[2].score | 0.7842658162117004 |
| keywords[2].display_name | Decision tree |
| keywords[3].id | https://openalex.org/keywords/machine-learning |
| keywords[3].score | 0.6407691240310669 |
| keywords[3].display_name | Machine learning |
| keywords[4].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[4].score | 0.5542508959770203 |
| keywords[4].display_name | Artificial intelligence |
| keywords[5].id | https://openalex.org/keywords/data-mining |
| keywords[5].score | 0.5004010200500488 |
| keywords[5].display_name | Data mining |
| keywords[6].id | https://openalex.org/keywords/tree |
| keywords[6].score | 0.4978935718536377 |
| keywords[6].display_name | Tree (set theory) |
| keywords[7].id | https://openalex.org/keywords/decision-tree-learning |
| keywords[7].score | 0.46841898560523987 |
| keywords[7].display_name | Decision tree learning |
| keywords[8].id | https://openalex.org/keywords/the-internet |
| keywords[8].score | 0.15105998516082764 |
| keywords[8].display_name | The Internet |
| keywords[9].id | https://openalex.org/keywords/world-wide-web |
| keywords[9].score | 0.14010319113731384 |
| keywords[9].display_name | World Wide Web |
| language | en |
| locations[0].id | doi:10.1051/itmconf/20235701018 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210171711 |
| locations[0].source.issn | 2271-2097, 2431-7578 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2271-2097 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | ITM Web of Conferences |
| locations[0].source.host_organization | https://openalex.org/P4310319748 |
| locations[0].source.host_organization_name | EDP Sciences |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310319748 |
| locations[0].source.host_organization_lineage_names | EDP Sciences |
| locations[0].license | cc-by |
| locations[0].pdf_url | https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdf |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | ITM Web of Conferences |
| locations[0].landing_page_url | https://doi.org/10.1051/itmconf/20235701018 |
| locations[1].id | pmh:oai:doaj.org/article:3c4c1216f6d246c3870d04b418806f41 |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306401280 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[1].source.host_organization | |
| locations[1].source.host_organization_name | |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | submittedVersion |
| locations[1].raw_type | article |
| locations[1].license_id | |
| locations[1].is_accepted | False |
| locations[1].is_published | False |
| locations[1].raw_source_name | ITM Web of Conferences, Vol 57, p 01018 (2023) |
| locations[1].landing_page_url | https://doaj.org/article/3c4c1216f6d246c3870d04b418806f41 |
| locations[2].id | pmh:oai:edpsciences.org:dkey/10.1051/itmconf/20235701018 |
| locations[2].is_oa | False |
| locations[2].source.id | https://openalex.org/S4306400744 |
| locations[2].source.issn | |
| locations[2].source.type | repository |
| locations[2].source.is_oa | False |
| locations[2].source.issn_l | |
| locations[2].source.is_core | False |
| locations[2].source.is_in_doaj | False |
| locations[2].source.display_name | Springer Link (Chiba Institute of Technology) |
| locations[2].source.host_organization | https://openalex.org/I8488066 |
| locations[2].source.host_organization_name | Chiba Institute of Technology |
| locations[2].source.host_organization_lineage | https://openalex.org/I8488066 |
| locations[2].license | |
| locations[2].pdf_url | |
| locations[2].version | submittedVersion |
| locations[2].raw_type | Text |
| locations[2].license_id | |
| locations[2].is_accepted | False |
| locations[2].is_published | False |
| locations[2].raw_source_name | https://doi.org/10.1051/itmconf/20235701018 |
| locations[2].landing_page_url | |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5093240143 |
| authorships[0].author.orcid | |
| authorships[0].author.display_name | Duncan Eric O. Ogonji |
| authorships[0].countries | KE |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I26805570 |
| authorships[0].affiliations[0].raw_affiliation_string | School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and technology, Nairobi, Kenya |
| authorships[0].institutions[0].id | https://openalex.org/I26805570 |
| authorships[0].institutions[0].ror | https://ror.org/015h5sy57 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I26805570 |
| authorships[0].institutions[0].country_code | KE |
| authorships[0].institutions[0].display_name | Jomo Kenyatta University of Agriculture and Technology |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Duncan Eric O. Ogonji |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and technology, Nairobi, Kenya |
| authorships[1].author.id | https://openalex.org/A5109280801 |
| authorships[1].author.orcid | |
| authorships[1].author.display_name | Wilson Cheruiyot |
| authorships[1].countries | KE |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I26805570 |
| authorships[1].affiliations[0].raw_affiliation_string | School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and technology, Nairobi, Kenya |
| authorships[1].institutions[0].id | https://openalex.org/I26805570 |
| authorships[1].institutions[0].ror | https://ror.org/015h5sy57 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I26805570 |
| authorships[1].institutions[0].country_code | KE |
| authorships[1].institutions[0].display_name | Jomo Kenyatta University of Agriculture and Technology |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Cheruiyot Wilson |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and technology, Nairobi, Kenya |
| authorships[2].author.id | https://openalex.org/A5065332583 |
| authorships[2].author.orcid | https://orcid.org/0000-0002-0278-0851 |
| authorships[2].author.display_name | Waweru Mwangi |
| authorships[2].countries | KE |
| authorships[2].affiliations[0].institution_ids | https://openalex.org/I26805570 |
| authorships[2].affiliations[0].raw_affiliation_string | School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and technology, Nairobi, Kenya |
| authorships[2].institutions[0].id | https://openalex.org/I26805570 |
| authorships[2].institutions[0].ror | https://ror.org/015h5sy57 |
| authorships[2].institutions[0].type | education |
| authorships[2].institutions[0].lineage | https://openalex.org/I26805570 |
| authorships[2].institutions[0].country_code | KE |
| authorships[2].institutions[0].display_name | Jomo Kenyatta University of Agriculture and Technology |
| authorships[2].author_position | last |
| authorships[2].raw_author_name | Waweru Mwangi |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and technology, Nairobi, Kenya |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdf |
| open_access.oa_status | diamond |
| open_access.any_repository_has_fulltext | False |
| created_date | 2023-11-11T00:00:00 |
| display_name | A Hybrid Model for Detecting Phishing Attack Using Recommedation Decision Trees |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T11644 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9991000294685364 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1710 |
| primary_topic.subfield.display_name | Information Systems |
| primary_topic.display_name | Spam and Phishing Detection |
| related_works | https://openalex.org/W4316657892, https://openalex.org/W3134840015, https://openalex.org/W2591672004, https://openalex.org/W4366979180, https://openalex.org/W1982169401, https://openalex.org/W2356463514, https://openalex.org/W3036095178, https://openalex.org/W4319437832, https://openalex.org/W4243803609, https://openalex.org/W4384470695 |
| cited_by_count | 0 |
| locations_count | 3 |
| best_oa_location.id | doi:10.1051/itmconf/20235701018 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210171711 |
| best_oa_location.source.issn | 2271-2097, 2431-7578 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2271-2097 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | ITM Web of Conferences |
| best_oa_location.source.host_organization | https://openalex.org/P4310319748 |
| best_oa_location.source.host_organization_name | EDP Sciences |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310319748 |
| best_oa_location.source.host_organization_lineage_names | EDP Sciences |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdf |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | ITM Web of Conferences |
| best_oa_location.landing_page_url | https://doi.org/10.1051/itmconf/20235701018 |
| primary_location.id | doi:10.1051/itmconf/20235701018 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210171711 |
| primary_location.source.issn | 2271-2097, 2431-7578 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2271-2097 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | ITM Web of Conferences |
| primary_location.source.host_organization | https://openalex.org/P4310319748 |
| primary_location.source.host_organization_name | EDP Sciences |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310319748 |
| primary_location.source.host_organization_lineage_names | EDP Sciences |
| primary_location.license | cc-by |
| primary_location.pdf_url | https://www.itm-conferences.org/articles/itmconf/pdf/2023/07/itmconf_icaect2023_01018.pdf |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | ITM Web of Conferences |
| primary_location.landing_page_url | https://doi.org/10.1051/itmconf/20235701018 |
| publication_date | 2023-01-01 |
| publication_year | 2023 |
| referenced_works | https://openalex.org/W3121722212, https://openalex.org/W4239466514, https://openalex.org/W2808055790, https://openalex.org/W2972470732, https://openalex.org/W4285445495, https://openalex.org/W2971633718, https://openalex.org/W4240209237, https://openalex.org/W2883045838, https://openalex.org/W4285381745, https://openalex.org/W4285381666 |
| referenced_works_count | 10 |
| abstract_inverted_index.% | 237 |
| abstract_inverted_index.A | 113 |
| abstract_inverted_index.a | 34, 68, 82, 110, 171 |
| abstract_inverted_index.10 | 203 |
| abstract_inverted_index.an | 227 |
| abstract_inverted_index.at | 119 |
| abstract_inverted_index.be | 106, 117 |
| abstract_inverted_index.by | 2 |
| abstract_inverted_index.is | 30, 81, 89, 130, 242 |
| abstract_inverted_index.it | 29, 104 |
| abstract_inverted_index.of | 52, 59, 70, 99, 125, 128, 156, 167, 173, 184, 190, 200, 232, 235 |
| abstract_inverted_index.on | 44 |
| abstract_inverted_index.or | 139 |
| abstract_inverted_index.to | 4, 19, 23, 32, 108, 136, 142, 193, 212 |
| abstract_inverted_index.But | 79 |
| abstract_inverted_index.For | 27 |
| abstract_inverted_index.The | 164, 219 |
| abstract_inverted_index.and | 47, 66, 73, 94, 159, 197, 208, 238 |
| abstract_inverted_index.any | 10, 155 |
| abstract_inverted_index.are | 42 |
| abstract_inverted_index.for | 148 |
| abstract_inverted_index.the | 6, 53, 86, 133, 168, 178, 182, 185, 188, 191, 210, 214, 233 |
| abstract_inverted_index.use | 109, 137 |
| abstract_inverted_index.Most | 51 |
| abstract_inverted_index.[1]. | 97 |
| abstract_inverted_index.data | 22, 45, 87, 129 |
| abstract_inverted_index.deep | 160 |
| abstract_inverted_index.from | 76, 181 |
| abstract_inverted_index.gain | 143 |
| abstract_inverted_index.into | 8, 144 |
| abstract_inverted_index.list | 69 |
| abstract_inverted_index.path | 166 |
| abstract_inverted_index.rate | 231, 241 |
| abstract_inverted_index.root | 183 |
| abstract_inverted_index.send | 20 |
| abstract_inverted_index.size | 88 |
| abstract_inverted_index.such | 71, 77 |
| abstract_inverted_index.task | 84 |
| abstract_inverted_index.that | 176 |
| abstract_inverted_index.them | 18, 65 |
| abstract_inverted_index.then | 16 |
| abstract_inverted_index.this | 80 |
| abstract_inverted_index.tree | 186, 192, 224 |
| abstract_inverted_index.true | 195, 229 |
| abstract_inverted_index.used | 209 |
| abstract_inverted_index.user | 146 |
| abstract_inverted_index.very | 90 |
| abstract_inverted_index.want | 135 |
| abstract_inverted_index.were | 206 |
| abstract_inverted_index.work | 55 |
| abstract_inverted_index.7.4%. | 243 |
| abstract_inverted_index.92.28 | 236 |
| abstract_inverted_index.based | 43 |
| abstract_inverted_index.block | 74 |
| abstract_inverted_index.class | 180 |
| abstract_inverted_index.false | 198, 239 |
| abstract_inverted_index.input | 141 |
| abstract_inverted_index.logs, | 63 |
| abstract_inverted_index.looks | 14 |
| abstract_inverted_index.model | 169, 234 |
| abstract_inverted_index.train | 213 |
| abstract_inverted_index.trees | 205 |
| abstract_inverted_index.tress | 153 |
| abstract_inverted_index.trick | 5 |
| abstract_inverted_index.using | 100 |
| abstract_inverted_index.which | 13 |
| abstract_inverted_index.would | 105, 116 |
| abstract_inverted_index.Hybrid | 150 |
| abstract_inverted_index.Recent | 38 |
| abstract_inverted_index.attack | 62 |
| abstract_inverted_index.better | 107, 118 |
| abstract_inverted_index.create | 67 |
| abstract_inverted_index.detect | 194 |
| abstract_inverted_index.format | 127 |
| abstract_inverted_index.hybrid | 111, 114, 221 |
| abstract_inverted_index.images | 138 |
| abstract_inverted_index.large, | 91 |
| abstract_inverted_index.mining | 46 |
| abstract_inverted_index.model. | 218 |
| abstract_inverted_index.series | 172 |
| abstract_inverted_index.single | 101 |
| abstract_inverted_index.system | 147 |
| abstract_inverted_index.trying | 3 |
| abstract_inverted_index.victim | 7 |
| abstract_inverted_index.Instead | 98 |
| abstract_inverted_index.analyze | 64 |
| abstract_inverted_index.another | 145 |
| abstract_inverted_index.attacks | 122 |
| abstract_inverted_index.because | 85, 123 |
| abstract_inverted_index.connect | 177 |
| abstract_inverted_index.develop | 33 |
| abstract_inverted_index.dynamic | 95 |
| abstract_inverted_index.machine | 48, 157 |
| abstract_inverted_index.nature. | 96 |
| abstract_inverted_index.overall | 228 |
| abstract_inverted_index.privacy | 25 |
| abstract_inverted_index.related | 54 |
| abstract_inverted_index.require | 57 |
| abstract_inverted_index.system. | 37 |
| abstract_inverted_index.systems | 41 |
| abstract_inverted_index.through | 187 |
| abstract_inverted_index.traffic | 75 |
| abstract_inverted_index.whether | 132 |
| abstract_inverted_index.Phishing | 0 |
| abstract_inverted_index.approach | 103, 115, 225 |
| abstract_inverted_index.branches | 189 |
| abstract_inverted_index.changing | 93 |
| abstract_inverted_index.continue | 92 |
| abstract_inverted_index.decision | 152, 165, 204, 216, 223 |
| abstract_inverted_index.enhances | 154 |
| abstract_inverted_index.features | 211 |
| abstract_inverted_index.followed | 170 |
| abstract_inverted_index.handled; | 131 |
| abstract_inverted_index.intruder | 134 |
| abstract_inverted_index.learning | 49, 158, 161 |
| abstract_inverted_index.negative | 240 |
| abstract_inverted_index.performs | 1 |
| abstract_inverted_index.phishing | 35, 39, 61, 121, 201 |
| abstract_inverted_index.positive | 196, 230 |
| abstract_inverted_index.previous | 60 |
| abstract_inverted_index.provided | 226 |
| abstract_inverted_index.sources. | 78 |
| abstract_inverted_index.textural | 140 |
| abstract_inverted_index.accessing | 9 |
| abstract_inverted_index.algorithm | 102 |
| abstract_inverted_index.approach. | 112 |
| abstract_inverted_index.attempts. | 202 |
| abstract_inverted_index.computing | 11 |
| abstract_inverted_index.detection | 36, 40 |
| abstract_inverted_index.developed | 220 |
| abstract_inverted_index.different | 126 |
| abstract_inverted_index.essential | 31 |
| abstract_inverted_index.important | 21 |
| abstract_inverted_index.negatives | 199 |
| abstract_inverted_index.original, | 15 |
| abstract_inverted_index.phishing. | 149 |
| abstract_inverted_index.predicted | 179 |
| abstract_inverted_index.resource. | 26 |
| abstract_inverted_index.activities | 72 |
| abstract_inverted_index.algorithms | 162 |
| abstract_inverted_index.collection | 58 |
| abstract_inverted_index.considered | 207 |
| abstract_inverted_index.cumbersome | 83 |
| abstract_inverted_index.literature | 56 |
| abstract_inverted_index.mitigating | 120 |
| abstract_inverted_index.regression | 217 |
| abstract_inverted_index.statements | 175 |
| abstract_inverted_index.information | 12 |
| abstract_inverted_index.instructing | 17 |
| abstract_inverted_index.prevention, | 28 |
| abstract_inverted_index.techniques. | 50 |
| abstract_inverted_index.if/else/then | 174 |
| abstract_inverted_index.performance. | 163 |
| abstract_inverted_index.classification | 124 |
| abstract_inverted_index.recommendation | 151, 215, 222 |
| abstract_inverted_index.unrestricted/unwanted | 24 |
| cited_by_percentile_year | |
| countries_distinct_count | 1 |
| institutions_distinct_count | 3 |
| sustainable_development_goals[0].id | https://metadata.un.org/sdg/16 |
| sustainable_development_goals[0].score | 0.8100000023841858 |
| sustainable_development_goals[0].display_name | Peace, Justice and strong institutions |
| citation_normalized_percentile.value | 0.27104298 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |