Adaptive Steganalysis Based on Selection Region and Combined Convolutional Neural Networks Article Swipe
 YOU?
·
· 2017
· Open Access
·
· DOI: https://doi.org/10.1155/2017/2314860
YOU?
·
· 2017
· Open Access
·
· DOI: https://doi.org/10.1155/2017/2314860
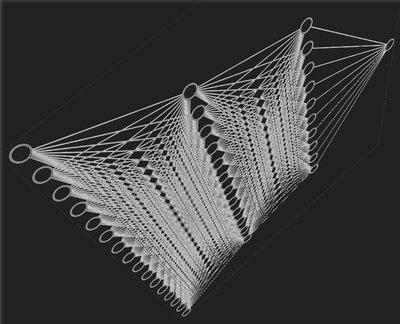
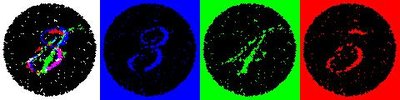
Digital image steganalysis is the art of detecting the presence of information hiding in carrier images. When detecting recently developed adaptive image steganography methods, state-of-art steganalysis methods cannot achieve satisfactory detection accuracy, because the adaptive steganography methods can adaptively embed information into regions with rich textures via the guidance of distortion function and thus make the effective steganalysis features hard to be extracted. Inspired by the promising success which convolutional neural network (CNN) has achieved in the fields of digital image analysis, increasing researchers are devoted to designing CNN based steganalysis methods. But as for detecting adaptive steganography methods, the results achieved by CNN based methods are still far from expected. In this paper, we propose a hybrid approach by designing a region selection method and a new CNN framework. In order to make the CNN focus on the regions with complex textures, we design a region selection method by finding a region with the maximal sum of the embedding probabilities. To evolve more diverse and effective steganalysis features, we design a new CNN framework consisting of three separate subnets with independent structure and configuration parameters and then merge and split the three subnets repeatedly. Experimental results indicate that our approach can lead to performance improvement in detecting adaptive steganography.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.1155/2017/2314860
- http://downloads.hindawi.com/journals/scn/2017/2314860.pdf
- OA Status
- hybrid
- Cited By
- 13
- References
- 11
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W2768061508
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W2768061508Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1155/2017/2314860Digital Object Identifier
- Title
-
Adaptive Steganalysis Based on Selection Region and Combined Convolutional Neural NetworksWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2017Year of publication
- Publication date
-
2017-01-01Full publication date if available
- Authors
-
Donghui Hu, Qiang Shen, Shengnan Zhou, Xueliang Liu, Yuqi Fan, Lina WangList of authors in order
- Landing page
-
https://doi.org/10.1155/2017/2314860Publisher landing page
- PDF URL
-
https://downloads.hindawi.com/journals/scn/2017/2314860.pdfDirect link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
hybridOpen access status per OpenAlex
- OA URL
-
https://downloads.hindawi.com/journals/scn/2017/2314860.pdfDirect OA link when available
- Concepts
-
Steganalysis, Computer science, Convolutional neural network, Steganography, Artificial intelligence, Pattern recognition (psychology), Embedding, Feature selection, Data miningTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
13Total citation count in OpenAlex
- Citations by year (recent)
-
2023: 4, 2022: 2, 2021: 2, 2020: 1, 2019: 2Per-year citation counts (last 5 years)
- References (count)
-
11Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W2768061508 |
|---|---|
| doi | https://doi.org/10.1155/2017/2314860 |
| ids.doi | https://doi.org/10.1155/2017/2314860 |
| ids.mag | 2768061508 |
| ids.openalex | https://openalex.org/W2768061508 |
| fwci | 0.63555111 |
| type | article |
| title | Adaptive Steganalysis Based on Selection Region and Combined Convolutional Neural Networks |
| awards[0].id | https://openalex.org/G3422571525 |
| awards[0].funder_id | https://openalex.org/F4320321001 |
| awards[0].display_name | |
| awards[0].funder_award_id | KJ2017A734 |
| awards[0].funder_display_name | National Natural Science Foundation of China |
| awards[1].id | https://openalex.org/G8895439857 |
| awards[1].funder_id | https://openalex.org/F4320321001 |
| awards[1].display_name | |
| awards[1].funder_award_id | U1536204 |
| awards[1].funder_display_name | National Natural Science Foundation of China |
| awards[2].id | https://openalex.org/G3248075049 |
| awards[2].funder_id | https://openalex.org/F4320321001 |
| awards[2].display_name | |
| awards[2].funder_award_id | 61672386 |
| awards[2].funder_display_name | National Natural Science Foundation of China |
| biblio.issue | |
| biblio.volume | 2017 |
| biblio.last_page | 9 |
| biblio.first_page | 1 |
| topics[0].id | https://openalex.org/T10388 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 1.0 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1707 |
| topics[0].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[0].display_name | Advanced Steganography and Watermarking Techniques |
| topics[1].id | https://openalex.org/T12357 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9991999864578247 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1707 |
| topics[1].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[1].display_name | Digital Media Forensic Detection |
| topics[2].id | https://openalex.org/T10775 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9898999929428101 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1707 |
| topics[2].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[2].display_name | Generative Adversarial Networks and Image Synthesis |
| funders[0].id | https://openalex.org/F4320321001 |
| funders[0].ror | https://ror.org/01h0zpd94 |
| funders[0].display_name | National Natural Science Foundation of China |
| is_xpac | False |
| apc_list.value | 2100 |
| apc_list.currency | USD |
| apc_list.value_usd | 2100 |
| apc_paid.value | 2100 |
| apc_paid.currency | USD |
| apc_paid.value_usd | 2100 |
| concepts[0].id | https://openalex.org/C107368093 |
| concepts[0].level | 4 |
| concepts[0].score | 0.9796055555343628 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q448176 |
| concepts[0].display_name | Steganalysis |
| concepts[1].id | https://openalex.org/C41008148 |
| concepts[1].level | 0 |
| concepts[1].score | 0.8838291168212891 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[1].display_name | Computer science |
| concepts[2].id | https://openalex.org/C81363708 |
| concepts[2].level | 2 |
| concepts[2].score | 0.7686382532119751 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q17084460 |
| concepts[2].display_name | Convolutional neural network |
| concepts[3].id | https://openalex.org/C108801101 |
| concepts[3].level | 3 |
| concepts[3].score | 0.7567471265792847 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q15032 |
| concepts[3].display_name | Steganography |
| concepts[4].id | https://openalex.org/C154945302 |
| concepts[4].level | 1 |
| concepts[4].score | 0.6777442097663879 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[4].display_name | Artificial intelligence |
| concepts[5].id | https://openalex.org/C153180895 |
| concepts[5].level | 2 |
| concepts[5].score | 0.6605603694915771 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q7148389 |
| concepts[5].display_name | Pattern recognition (psychology) |
| concepts[6].id | https://openalex.org/C41608201 |
| concepts[6].level | 2 |
| concepts[6].score | 0.5556516051292419 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q980509 |
| concepts[6].display_name | Embedding |
| concepts[7].id | https://openalex.org/C148483581 |
| concepts[7].level | 2 |
| concepts[7].score | 0.4529529809951782 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q446488 |
| concepts[7].display_name | Feature selection |
| concepts[8].id | https://openalex.org/C124101348 |
| concepts[8].level | 1 |
| concepts[8].score | 0.36343878507614136 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q172491 |
| concepts[8].display_name | Data mining |
| keywords[0].id | https://openalex.org/keywords/steganalysis |
| keywords[0].score | 0.9796055555343628 |
| keywords[0].display_name | Steganalysis |
| keywords[1].id | https://openalex.org/keywords/computer-science |
| keywords[1].score | 0.8838291168212891 |
| keywords[1].display_name | Computer science |
| keywords[2].id | https://openalex.org/keywords/convolutional-neural-network |
| keywords[2].score | 0.7686382532119751 |
| keywords[2].display_name | Convolutional neural network |
| keywords[3].id | https://openalex.org/keywords/steganography |
| keywords[3].score | 0.7567471265792847 |
| keywords[3].display_name | Steganography |
| keywords[4].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[4].score | 0.6777442097663879 |
| keywords[4].display_name | Artificial intelligence |
| keywords[5].id | https://openalex.org/keywords/pattern-recognition |
| keywords[5].score | 0.6605603694915771 |
| keywords[5].display_name | Pattern recognition (psychology) |
| keywords[6].id | https://openalex.org/keywords/embedding |
| keywords[6].score | 0.5556516051292419 |
| keywords[6].display_name | Embedding |
| keywords[7].id | https://openalex.org/keywords/feature-selection |
| keywords[7].score | 0.4529529809951782 |
| keywords[7].display_name | Feature selection |
| keywords[8].id | https://openalex.org/keywords/data-mining |
| keywords[8].score | 0.36343878507614136 |
| keywords[8].display_name | Data mining |
| language | en |
| locations[0].id | doi:10.1155/2017/2314860 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S120683614 |
| locations[0].source.issn | 1939-0114, 1939-0122 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | False |
| locations[0].source.issn_l | 1939-0114 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | Security and Communication Networks |
| locations[0].source.host_organization | https://openalex.org/P4310319869 |
| locations[0].source.host_organization_name | Hindawi Publishing Corporation |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310319869 |
| locations[0].source.host_organization_lineage_names | Hindawi Publishing Corporation |
| locations[0].license | cc-by |
| locations[0].pdf_url | http://downloads.hindawi.com/journals/scn/2017/2314860.pdf |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Security and Communication Networks |
| locations[0].landing_page_url | https://doi.org/10.1155/2017/2314860 |
| locations[1].id | pmh:oai:doaj.org/article:5682396c3132466381d6eb14a789c4df |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306401280 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[1].source.host_organization | |
| locations[1].source.host_organization_name | |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | submittedVersion |
| locations[1].raw_type | article |
| locations[1].license_id | |
| locations[1].is_accepted | False |
| locations[1].is_published | False |
| locations[1].raw_source_name | Security and Communication Networks, Vol 2017 (2017) |
| locations[1].landing_page_url | https://doaj.org/article/5682396c3132466381d6eb14a789c4df |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5010997479 |
| authorships[0].author.orcid | https://orcid.org/0000-0001-9517-9688 |
| authorships[0].author.display_name | Donghui Hu |
| authorships[0].countries | CN |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I16365422 |
| authorships[0].affiliations[0].raw_affiliation_string | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[0].institutions[0].id | https://openalex.org/I16365422 |
| authorships[0].institutions[0].ror | https://ror.org/02czkny70 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I16365422 |
| authorships[0].institutions[0].country_code | CN |
| authorships[0].institutions[0].display_name | Hefei University of Technology |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Donghui Hu |
| authorships[0].is_corresponding | True |
| authorships[0].raw_affiliation_strings | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[1].author.id | https://openalex.org/A5036010787 |
| authorships[1].author.orcid | https://orcid.org/0000-0001-9333-4605 |
| authorships[1].author.display_name | Qiang Shen |
| authorships[1].countries | CN |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I16365422 |
| authorships[1].affiliations[0].raw_affiliation_string | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[1].institutions[0].id | https://openalex.org/I16365422 |
| authorships[1].institutions[0].ror | https://ror.org/02czkny70 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I16365422 |
| authorships[1].institutions[0].country_code | CN |
| authorships[1].institutions[0].display_name | Hefei University of Technology |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Qiang Shen |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[2].author.id | https://openalex.org/A5080532571 |
| authorships[2].author.orcid | |
| authorships[2].author.display_name | Shengnan Zhou |
| authorships[2].countries | CN |
| authorships[2].affiliations[0].institution_ids | https://openalex.org/I16365422 |
| authorships[2].affiliations[0].raw_affiliation_string | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[2].institutions[0].id | https://openalex.org/I16365422 |
| authorships[2].institutions[0].ror | https://ror.org/02czkny70 |
| authorships[2].institutions[0].type | education |
| authorships[2].institutions[0].lineage | https://openalex.org/I16365422 |
| authorships[2].institutions[0].country_code | CN |
| authorships[2].institutions[0].display_name | Hefei University of Technology |
| authorships[2].author_position | middle |
| authorships[2].raw_author_name | Shengnan Zhou |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[3].author.id | https://openalex.org/A5101993173 |
| authorships[3].author.orcid | https://orcid.org/0000-0003-0077-9715 |
| authorships[3].author.display_name | Xueliang Liu |
| authorships[3].countries | CN |
| authorships[3].affiliations[0].institution_ids | https://openalex.org/I16365422 |
| authorships[3].affiliations[0].raw_affiliation_string | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[3].institutions[0].id | https://openalex.org/I16365422 |
| authorships[3].institutions[0].ror | https://ror.org/02czkny70 |
| authorships[3].institutions[0].type | education |
| authorships[3].institutions[0].lineage | https://openalex.org/I16365422 |
| authorships[3].institutions[0].country_code | CN |
| authorships[3].institutions[0].display_name | Hefei University of Technology |
| authorships[3].author_position | middle |
| authorships[3].raw_author_name | Xueliang Liu |
| authorships[3].is_corresponding | False |
| authorships[3].raw_affiliation_strings | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[4].author.id | https://openalex.org/A5084923117 |
| authorships[4].author.orcid | https://orcid.org/0000-0003-0270-6261 |
| authorships[4].author.display_name | Yuqi Fan |
| authorships[4].countries | CN |
| authorships[4].affiliations[0].institution_ids | https://openalex.org/I16365422 |
| authorships[4].affiliations[0].raw_affiliation_string | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[4].institutions[0].id | https://openalex.org/I16365422 |
| authorships[4].institutions[0].ror | https://ror.org/02czkny70 |
| authorships[4].institutions[0].type | education |
| authorships[4].institutions[0].lineage | https://openalex.org/I16365422 |
| authorships[4].institutions[0].country_code | CN |
| authorships[4].institutions[0].display_name | Hefei University of Technology |
| authorships[4].author_position | middle |
| authorships[4].raw_author_name | Yuqi Fan |
| authorships[4].is_corresponding | False |
| authorships[4].raw_affiliation_strings | School of Computer and Information, Hefei University of Technology, Hefei 230009, China |
| authorships[5].author.id | https://openalex.org/A5107906291 |
| authorships[5].author.orcid | https://orcid.org/0009-0003-2811-5731 |
| authorships[5].author.display_name | Lina Wang |
| authorships[5].countries | CN |
| authorships[5].affiliations[0].institution_ids | https://openalex.org/I37461747 |
| authorships[5].affiliations[0].raw_affiliation_string | School of Computer and Information, Wuhan University, Wuhan 430072, China |
| authorships[5].institutions[0].id | https://openalex.org/I37461747 |
| authorships[5].institutions[0].ror | https://ror.org/033vjfk17 |
| authorships[5].institutions[0].type | education |
| authorships[5].institutions[0].lineage | https://openalex.org/I37461747 |
| authorships[5].institutions[0].country_code | CN |
| authorships[5].institutions[0].display_name | Wuhan University |
| authorships[5].author_position | last |
| authorships[5].raw_author_name | Lina Wang |
| authorships[5].is_corresponding | False |
| authorships[5].raw_affiliation_strings | School of Computer and Information, Wuhan University, Wuhan 430072, China |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | http://downloads.hindawi.com/journals/scn/2017/2314860.pdf |
| open_access.oa_status | hybrid |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Adaptive Steganalysis Based on Selection Region and Combined Convolutional Neural Networks |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10388 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 1.0 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1707 |
| primary_topic.subfield.display_name | Computer Vision and Pattern Recognition |
| primary_topic.display_name | Advanced Steganography and Watermarking Techniques |
| related_works | https://openalex.org/W2148973528, https://openalex.org/W2939392096, https://openalex.org/W4243922849, https://openalex.org/W2106726851, https://openalex.org/W4309385482, https://openalex.org/W2792878404, https://openalex.org/W2068740952, https://openalex.org/W1583147569, https://openalex.org/W2182496537, https://openalex.org/W3154843532 |
| cited_by_count | 13 |
| counts_by_year[0].year | 2023 |
| counts_by_year[0].cited_by_count | 4 |
| counts_by_year[1].year | 2022 |
| counts_by_year[1].cited_by_count | 2 |
| counts_by_year[2].year | 2021 |
| counts_by_year[2].cited_by_count | 2 |
| counts_by_year[3].year | 2020 |
| counts_by_year[3].cited_by_count | 1 |
| counts_by_year[4].year | 2019 |
| counts_by_year[4].cited_by_count | 2 |
| counts_by_year[5].year | 2018 |
| counts_by_year[5].cited_by_count | 2 |
| locations_count | 2 |
| best_oa_location.id | doi:10.1155/2017/2314860 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S120683614 |
| best_oa_location.source.issn | 1939-0114, 1939-0122 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | False |
| best_oa_location.source.issn_l | 1939-0114 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | Security and Communication Networks |
| best_oa_location.source.host_organization | https://openalex.org/P4310319869 |
| best_oa_location.source.host_organization_name | Hindawi Publishing Corporation |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310319869 |
| best_oa_location.source.host_organization_lineage_names | Hindawi Publishing Corporation |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | http://downloads.hindawi.com/journals/scn/2017/2314860.pdf |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Security and Communication Networks |
| best_oa_location.landing_page_url | https://doi.org/10.1155/2017/2314860 |
| primary_location.id | doi:10.1155/2017/2314860 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S120683614 |
| primary_location.source.issn | 1939-0114, 1939-0122 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | False |
| primary_location.source.issn_l | 1939-0114 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | Security and Communication Networks |
| primary_location.source.host_organization | https://openalex.org/P4310319869 |
| primary_location.source.host_organization_name | Hindawi Publishing Corporation |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310319869 |
| primary_location.source.host_organization_lineage_names | Hindawi Publishing Corporation |
| primary_location.license | cc-by |
| primary_location.pdf_url | http://downloads.hindawi.com/journals/scn/2017/2314860.pdf |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Security and Communication Networks |
| primary_location.landing_page_url | https://doi.org/10.1155/2017/2314860 |
| publication_date | 2017-01-01 |
| publication_year | 2017 |
| referenced_works | https://openalex.org/W2124890704, https://openalex.org/W2154026545, https://openalex.org/W2170598445, https://openalex.org/W2134527668, https://openalex.org/W2009130368, https://openalex.org/W2277839806, https://openalex.org/W2112796928, https://openalex.org/W2322622188, https://openalex.org/W2739185626, https://openalex.org/W22271197, https://openalex.org/W2124664712 |
| referenced_works_count | 11 |
| abstract_inverted_index.a | 116, 121, 126, 145, 151, 171 |
| abstract_inverted_index.In | 111, 130 |
| abstract_inverted_index.To | 161 |
| abstract_inverted_index.as | 93 |
| abstract_inverted_index.be | 61 |
| abstract_inverted_index.by | 64, 102, 119, 149 |
| abstract_inverted_index.in | 13, 75, 206 |
| abstract_inverted_index.is | 3 |
| abstract_inverted_index.of | 6, 10, 49, 78, 157, 176 |
| abstract_inverted_index.on | 137 |
| abstract_inverted_index.to | 60, 86, 132, 203 |
| abstract_inverted_index.we | 114, 143, 169 |
| abstract_inverted_index.But | 92 |
| abstract_inverted_index.CNN | 88, 103, 128, 135, 173 |
| abstract_inverted_index.and | 52, 125, 165, 183, 186, 189 |
| abstract_inverted_index.are | 84, 106 |
| abstract_inverted_index.art | 5 |
| abstract_inverted_index.can | 37, 201 |
| abstract_inverted_index.far | 108 |
| abstract_inverted_index.for | 94 |
| abstract_inverted_index.has | 73 |
| abstract_inverted_index.new | 127, 172 |
| abstract_inverted_index.our | 199 |
| abstract_inverted_index.sum | 156 |
| abstract_inverted_index.the | 4, 8, 33, 47, 55, 65, 76, 99, 134, 138, 154, 158, 191 |
| abstract_inverted_index.via | 46 |
| abstract_inverted_index.When | 16 |
| abstract_inverted_index.from | 109 |
| abstract_inverted_index.hard | 59 |
| abstract_inverted_index.into | 41 |
| abstract_inverted_index.lead | 202 |
| abstract_inverted_index.make | 54, 133 |
| abstract_inverted_index.more | 163 |
| abstract_inverted_index.rich | 44 |
| abstract_inverted_index.that | 198 |
| abstract_inverted_index.then | 187 |
| abstract_inverted_index.this | 112 |
| abstract_inverted_index.thus | 53 |
| abstract_inverted_index.with | 43, 140, 153, 180 |
| abstract_inverted_index.(CNN) | 72 |
| abstract_inverted_index.based | 89, 104 |
| abstract_inverted_index.embed | 39 |
| abstract_inverted_index.focus | 136 |
| abstract_inverted_index.image | 1, 21, 80 |
| abstract_inverted_index.merge | 188 |
| abstract_inverted_index.order | 131 |
| abstract_inverted_index.split | 190 |
| abstract_inverted_index.still | 107 |
| abstract_inverted_index.three | 177, 192 |
| abstract_inverted_index.which | 68 |
| abstract_inverted_index.cannot | 27 |
| abstract_inverted_index.design | 144, 170 |
| abstract_inverted_index.evolve | 162 |
| abstract_inverted_index.fields | 77 |
| abstract_inverted_index.hiding | 12 |
| abstract_inverted_index.hybrid | 117 |
| abstract_inverted_index.method | 124, 148 |
| abstract_inverted_index.neural | 70 |
| abstract_inverted_index.paper, | 113 |
| abstract_inverted_index.region | 122, 146, 152 |
| abstract_inverted_index.Digital | 0 |
| abstract_inverted_index.achieve | 28 |
| abstract_inverted_index.because | 32 |
| abstract_inverted_index.carrier | 14 |
| abstract_inverted_index.complex | 141 |
| abstract_inverted_index.devoted | 85 |
| abstract_inverted_index.digital | 79 |
| abstract_inverted_index.diverse | 164 |
| abstract_inverted_index.finding | 150 |
| abstract_inverted_index.images. | 15 |
| abstract_inverted_index.maximal | 155 |
| abstract_inverted_index.methods | 26, 36, 105 |
| abstract_inverted_index.network | 71 |
| abstract_inverted_index.propose | 115 |
| abstract_inverted_index.regions | 42, 139 |
| abstract_inverted_index.results | 100, 196 |
| abstract_inverted_index.subnets | 179, 193 |
| abstract_inverted_index.success | 67 |
| abstract_inverted_index.Inspired | 63 |
| abstract_inverted_index.achieved | 74, 101 |
| abstract_inverted_index.adaptive | 20, 34, 96, 208 |
| abstract_inverted_index.approach | 118, 200 |
| abstract_inverted_index.features | 58 |
| abstract_inverted_index.function | 51 |
| abstract_inverted_index.guidance | 48 |
| abstract_inverted_index.indicate | 197 |
| abstract_inverted_index.methods, | 23, 98 |
| abstract_inverted_index.methods. | 91 |
| abstract_inverted_index.presence | 9 |
| abstract_inverted_index.recently | 18 |
| abstract_inverted_index.separate | 178 |
| abstract_inverted_index.textures | 45 |
| abstract_inverted_index.accuracy, | 31 |
| abstract_inverted_index.analysis, | 81 |
| abstract_inverted_index.designing | 87, 120 |
| abstract_inverted_index.detecting | 7, 17, 95, 207 |
| abstract_inverted_index.detection | 30 |
| abstract_inverted_index.developed | 19 |
| abstract_inverted_index.effective | 56, 166 |
| abstract_inverted_index.embedding | 159 |
| abstract_inverted_index.expected. | 110 |
| abstract_inverted_index.features, | 168 |
| abstract_inverted_index.framework | 174 |
| abstract_inverted_index.promising | 66 |
| abstract_inverted_index.selection | 123, 147 |
| abstract_inverted_index.structure | 182 |
| abstract_inverted_index.textures, | 142 |
| abstract_inverted_index.adaptively | 38 |
| abstract_inverted_index.consisting | 175 |
| abstract_inverted_index.distortion | 50 |
| abstract_inverted_index.extracted. | 62 |
| abstract_inverted_index.framework. | 129 |
| abstract_inverted_index.increasing | 82 |
| abstract_inverted_index.parameters | 185 |
| abstract_inverted_index.improvement | 205 |
| abstract_inverted_index.independent | 181 |
| abstract_inverted_index.information | 11, 40 |
| abstract_inverted_index.performance | 204 |
| abstract_inverted_index.repeatedly. | 194 |
| abstract_inverted_index.researchers | 83 |
| abstract_inverted_index.Experimental | 195 |
| abstract_inverted_index.satisfactory | 29 |
| abstract_inverted_index.state-of-art | 24 |
| abstract_inverted_index.steganalysis | 2, 25, 57, 90, 167 |
| abstract_inverted_index.configuration | 184 |
| abstract_inverted_index.convolutional | 69 |
| abstract_inverted_index.steganography | 22, 35, 97 |
| abstract_inverted_index.probabilities. | 160 |
| abstract_inverted_index.steganography. | 209 |
| cited_by_percentile_year.max | 97 |
| cited_by_percentile_year.min | 89 |
| corresponding_author_ids | https://openalex.org/A5010997479 |
| countries_distinct_count | 1 |
| institutions_distinct_count | 6 |
| corresponding_institution_ids | https://openalex.org/I16365422 |
| citation_normalized_percentile.value | 0.73904069 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |