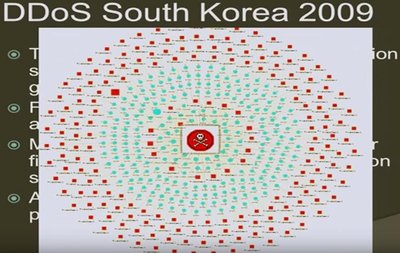
Cyber Security: Threats, Challenges, and Modern Protection Mechanisms Article Swipe
This research paper provides a comprehensive analysis of modern cybersecurity threats and the evolving landscape of digital risks at both global and national levels. It examines how cyberattacks—such as malware, phishing, ransomware, identity theft, social engineering, and distributed denial-of-service (DDoS) attacks—have become increasingly sophisticated due to rapid technological advancement, digitalization, and widespread internet usage. With a particular focus on Bangladesh, the study highlights the challenges faced by emerging digital economies, including outdated infrastructure, low cybersecurity awareness, limited skilled professionals, and rising incidents targeting financial and governmental sectors. Drawing on recent threat reports and academic literature, this work outlines how cybercrime has shifted from isolated attacks to well-organized, automated, and data-driven operations. The paper further explores modern defense mechanisms such as artificial intelligence, machine learning, encryption, ethical hacking, intrusion detection systems, and policy frameworks. These tools, combined with public awareness, institutional readiness, and strong legal foundations, are essential for building a sustainable and secure digital ecosystem. Overall, the study emphasizes that cybersecurity is not merely a technical issue—it is a strategic, economic, and national priority. A coordinated approach involving technology, skilled professionals, policies, and global cooperation is crucial for safeguarding digital infrastructures and ensuring long-term resilience against evolving cyber threats.
Related Topics
- Type
- preprint
- Landing Page
- https://doi.org/10.5281/zenodo.17763782
- OA Status
- green
- OpenAlex ID
- https://openalex.org/W7107955909
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W7107955909Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.5281/zenodo.17763782Digital Object Identifier
- Title
-
Cyber Security: Threats, Challenges, and Modern Protection MechanismsWork title
- Type
-
preprintOpenAlex work type
- Publication year
-
2025Year of publication
- Publication date
-
2025-11-29Full publication date if available
- Authors
-
Sabbir Mahmud AdorList of authors in order
- Landing page
-
https://doi.org/10.5281/zenodo.17763782Publisher landing page
- Open access
-
YesWhether a free full text is available
- OA status
-
greenOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.5281/zenodo.17763782Direct OA link when available
- Concepts
-
Safeguarding, Cybercrime, Computer security, Resilience (materials science), Identity theft, The Internet, Internet privacy, Data Protection Act 1998, Cyber threats, Malware, Work (physics), Business, Emerging technologies, Intrusion detection system, Key (lock), Digital transformation, Cyberwarfare, Digital forensics, Cyberspace, Engineering, Authentication (law), Confidentiality, National security, Public key infrastructure, Digital Revolution, Information privacy, Political science, Cyber crime, Warning system, Cyber-attack, Focus (optics)Top concepts (fields/topics) attached by OpenAlex
- Cited by
-
0Total citation count in OpenAlex
Full payload
| id | https://openalex.org/W7107955909 |
|---|---|
| doi | https://doi.org/10.5281/zenodo.17763782 |
| ids.doi | https://doi.org/10.5281/zenodo.17763782 |
| ids.openalex | https://openalex.org/W7107955909 |
| fwci | |
| type | preprint |
| title | Cyber Security: Threats, Challenges, and Modern Protection Mechanisms |
| biblio.issue | |
| biblio.volume | |
| biblio.last_page | |
| biblio.first_page | |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C2776743756 |
| concepts[0].level | 2 |
| concepts[0].score | 0.7310619354248047 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q5097921 |
| concepts[0].display_name | Safeguarding |
| concepts[1].id | https://openalex.org/C2779390178 |
| concepts[1].level | 3 |
| concepts[1].score | 0.699102520942688 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q29137 |
| concepts[1].display_name | Cybercrime |
| concepts[2].id | https://openalex.org/C38652104 |
| concepts[2].level | 1 |
| concepts[2].score | 0.6500992178916931 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[2].display_name | Computer security |
| concepts[3].id | https://openalex.org/C2779585090 |
| concepts[3].level | 2 |
| concepts[3].score | 0.6144340634346008 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q3457762 |
| concepts[3].display_name | Resilience (materials science) |
| concepts[4].id | https://openalex.org/C522325796 |
| concepts[4].level | 2 |
| concepts[4].score | 0.5309712886810303 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q471880 |
| concepts[4].display_name | Identity theft |
| concepts[5].id | https://openalex.org/C110875604 |
| concepts[5].level | 2 |
| concepts[5].score | 0.4677245318889618 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q75 |
| concepts[5].display_name | The Internet |
| concepts[6].id | https://openalex.org/C108827166 |
| concepts[6].level | 1 |
| concepts[6].score | 0.42777755856513977 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q175975 |
| concepts[6].display_name | Internet privacy |
| concepts[7].id | https://openalex.org/C69360830 |
| concepts[7].level | 2 |
| concepts[7].score | 0.42648905515670776 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q1172237 |
| concepts[7].display_name | Data Protection Act 1998 |
| concepts[8].id | https://openalex.org/C3018725008 |
| concepts[8].level | 2 |
| concepts[8].score | 0.37611886858940125 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q4071928 |
| concepts[8].display_name | Cyber threats |
| concepts[9].id | https://openalex.org/C541664917 |
| concepts[9].level | 2 |
| concepts[9].score | 0.3737090528011322 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q14001 |
| concepts[9].display_name | Malware |
| concepts[10].id | https://openalex.org/C18762648 |
| concepts[10].level | 2 |
| concepts[10].score | 0.35435110330581665 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q42213 |
| concepts[10].display_name | Work (physics) |
| concepts[11].id | https://openalex.org/C144133560 |
| concepts[11].level | 0 |
| concepts[11].score | 0.3525604009628296 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q4830453 |
| concepts[11].display_name | Business |
| concepts[12].id | https://openalex.org/C207267971 |
| concepts[12].level | 2 |
| concepts[12].score | 0.3505157232284546 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q120208 |
| concepts[12].display_name | Emerging technologies |
| concepts[13].id | https://openalex.org/C35525427 |
| concepts[13].level | 2 |
| concepts[13].score | 0.34437987208366394 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q745881 |
| concepts[13].display_name | Intrusion detection system |
| concepts[14].id | https://openalex.org/C26517878 |
| concepts[14].level | 2 |
| concepts[14].score | 0.33059942722320557 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q228039 |
| concepts[14].display_name | Key (lock) |
| concepts[15].id | https://openalex.org/C126082660 |
| concepts[15].level | 2 |
| concepts[15].score | 0.32392755150794983 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q4252370 |
| concepts[15].display_name | Digital transformation |
| concepts[16].id | https://openalex.org/C171769113 |
| concepts[16].level | 2 |
| concepts[16].score | 0.3208852708339691 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q849340 |
| concepts[16].display_name | Cyberwarfare |
| concepts[17].id | https://openalex.org/C84418412 |
| concepts[17].level | 2 |
| concepts[17].score | 0.3036865293979645 |
| concepts[17].wikidata | https://www.wikidata.org/wiki/Q3246940 |
| concepts[17].display_name | Digital forensics |
| concepts[18].id | https://openalex.org/C2781241145 |
| concepts[18].level | 3 |
| concepts[18].score | 0.2998618483543396 |
| concepts[18].wikidata | https://www.wikidata.org/wiki/Q204606 |
| concepts[18].display_name | Cyberspace |
| concepts[19].id | https://openalex.org/C127413603 |
| concepts[19].level | 0 |
| concepts[19].score | 0.29749399423599243 |
| concepts[19].wikidata | https://www.wikidata.org/wiki/Q11023 |
| concepts[19].display_name | Engineering |
| concepts[20].id | https://openalex.org/C148417208 |
| concepts[20].level | 2 |
| concepts[20].score | 0.2948421239852905 |
| concepts[20].wikidata | https://www.wikidata.org/wiki/Q4825882 |
| concepts[20].display_name | Authentication (law) |
| concepts[21].id | https://openalex.org/C71745522 |
| concepts[21].level | 2 |
| concepts[21].score | 0.29121145606040955 |
| concepts[21].wikidata | https://www.wikidata.org/wiki/Q2476929 |
| concepts[21].display_name | Confidentiality |
| concepts[22].id | https://openalex.org/C528167355 |
| concepts[22].level | 2 |
| concepts[22].score | 0.29052960872650146 |
| concepts[22].wikidata | https://www.wikidata.org/wiki/Q258307 |
| concepts[22].display_name | National security |
| concepts[23].id | https://openalex.org/C72648740 |
| concepts[23].level | 4 |
| concepts[23].score | 0.2857474088668823 |
| concepts[23].wikidata | https://www.wikidata.org/wiki/Q658476 |
| concepts[23].display_name | Public key infrastructure |
| concepts[24].id | https://openalex.org/C2778132726 |
| concepts[24].level | 2 |
| concepts[24].score | 0.2839828133583069 |
| concepts[24].wikidata | https://www.wikidata.org/wiki/Q1096872 |
| concepts[24].display_name | Digital Revolution |
| concepts[25].id | https://openalex.org/C123201435 |
| concepts[25].level | 2 |
| concepts[25].score | 0.27878180146217346 |
| concepts[25].wikidata | https://www.wikidata.org/wiki/Q456632 |
| concepts[25].display_name | Information privacy |
| concepts[26].id | https://openalex.org/C17744445 |
| concepts[26].level | 0 |
| concepts[26].score | 0.2715741991996765 |
| concepts[26].wikidata | https://www.wikidata.org/wiki/Q36442 |
| concepts[26].display_name | Political science |
| concepts[27].id | https://openalex.org/C2989129637 |
| concepts[27].level | 3 |
| concepts[27].score | 0.27046191692352295 |
| concepts[27].wikidata | https://www.wikidata.org/wiki/Q29137 |
| concepts[27].display_name | Cyber crime |
| concepts[28].id | https://openalex.org/C29825287 |
| concepts[28].level | 2 |
| concepts[28].score | 0.270185649394989 |
| concepts[28].wikidata | https://www.wikidata.org/wiki/Q1427940 |
| concepts[28].display_name | Warning system |
| concepts[29].id | https://openalex.org/C201307755 |
| concepts[29].level | 2 |
| concepts[29].score | 0.2690171003341675 |
| concepts[29].wikidata | https://www.wikidata.org/wiki/Q4071928 |
| concepts[29].display_name | Cyber-attack |
| concepts[30].id | https://openalex.org/C192209626 |
| concepts[30].level | 2 |
| concepts[30].score | 0.25538361072540283 |
| concepts[30].wikidata | https://www.wikidata.org/wiki/Q190909 |
| concepts[30].display_name | Focus (optics) |
| keywords[0].id | https://openalex.org/keywords/safeguarding |
| keywords[0].score | 0.7310619354248047 |
| keywords[0].display_name | Safeguarding |
| keywords[1].id | https://openalex.org/keywords/cybercrime |
| keywords[1].score | 0.699102520942688 |
| keywords[1].display_name | Cybercrime |
| keywords[2].id | https://openalex.org/keywords/resilience |
| keywords[2].score | 0.6144340634346008 |
| keywords[2].display_name | Resilience (materials science) |
| keywords[3].id | https://openalex.org/keywords/identity-theft |
| keywords[3].score | 0.5309712886810303 |
| keywords[3].display_name | Identity theft |
| keywords[4].id | https://openalex.org/keywords/the-internet |
| keywords[4].score | 0.4677245318889618 |
| keywords[4].display_name | The Internet |
| keywords[5].id | https://openalex.org/keywords/data-protection-act-1998 |
| keywords[5].score | 0.42648905515670776 |
| keywords[5].display_name | Data Protection Act 1998 |
| keywords[6].id | https://openalex.org/keywords/cyber-threats |
| keywords[6].score | 0.37611886858940125 |
| keywords[6].display_name | Cyber threats |
| keywords[7].id | https://openalex.org/keywords/malware |
| keywords[7].score | 0.3737090528011322 |
| keywords[7].display_name | Malware |
| keywords[8].id | https://openalex.org/keywords/work |
| keywords[8].score | 0.35435110330581665 |
| keywords[8].display_name | Work (physics) |
| language | |
| locations[0].id | doi:10.5281/zenodo.17763782 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4306400562 |
| locations[0].source.issn | |
| locations[0].source.type | repository |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | |
| locations[0].source.is_core | False |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | Zenodo (CERN European Organization for Nuclear Research) |
| locations[0].source.host_organization | https://openalex.org/I67311998 |
| locations[0].source.host_organization_name | European Organization for Nuclear Research |
| locations[0].source.host_organization_lineage | https://openalex.org/I67311998 |
| locations[0].license | cc-by |
| locations[0].pdf_url | |
| locations[0].version | |
| locations[0].raw_type | article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | False |
| locations[0].is_published | |
| locations[0].raw_source_name | |
| locations[0].landing_page_url | https://doi.org/10.5281/zenodo.17763782 |
| indexed_in | datacite |
| authorships[0].author.id | |
| authorships[0].author.orcid | |
| authorships[0].author.display_name | Sabbir Mahmud Ador |
| authorships[0].countries | BD |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I2800368670 |
| authorships[0].affiliations[0].raw_affiliation_string | National University Bangladesh |
| authorships[0].institutions[0].id | https://openalex.org/I2800368670 |
| authorships[0].institutions[0].ror | https://ror.org/https://ror.org/045p37n96 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I2800368670 |
| authorships[0].institutions[0].country_code | BD |
| authorships[0].institutions[0].display_name | National University Bangladesh |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Sabbir Mahmud Ador |
| authorships[0].is_corresponding | True |
| authorships[0].raw_affiliation_strings | National University Bangladesh |
| has_content.pdf | False |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.5281/zenodo.17763782 |
| open_access.oa_status | green |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-12-01T00:00:00 |
| display_name | Cyber Security: Threats, Challenges, and Modern Protection Mechanisms |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-12-01T00:07:19.613710 |
| primary_topic | |
| cited_by_count | 0 |
| locations_count | 1 |
| best_oa_location.id | doi:10.5281/zenodo.17763782 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4306400562 |
| best_oa_location.source.issn | |
| best_oa_location.source.type | repository |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | |
| best_oa_location.source.is_core | False |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | Zenodo (CERN European Organization for Nuclear Research) |
| best_oa_location.source.host_organization | https://openalex.org/I67311998 |
| best_oa_location.source.host_organization_name | European Organization for Nuclear Research |
| best_oa_location.source.host_organization_lineage | https://openalex.org/I67311998 |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | |
| best_oa_location.version | |
| best_oa_location.raw_type | article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | False |
| best_oa_location.is_published | False |
| best_oa_location.raw_source_name | |
| best_oa_location.landing_page_url | https://doi.org/10.5281/zenodo.17763782 |
| primary_location.id | doi:10.5281/zenodo.17763782 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4306400562 |
| primary_location.source.issn | |
| primary_location.source.type | repository |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | |
| primary_location.source.is_core | False |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | Zenodo (CERN European Organization for Nuclear Research) |
| primary_location.source.host_organization | https://openalex.org/I67311998 |
| primary_location.source.host_organization_name | European Organization for Nuclear Research |
| primary_location.source.host_organization_lineage | https://openalex.org/I67311998 |
| primary_location.license | cc-by |
| primary_location.pdf_url | |
| primary_location.version | |
| primary_location.raw_type | article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | False |
| primary_location.is_published | False |
| primary_location.raw_source_name | |
| primary_location.landing_page_url | https://doi.org/10.5281/zenodo.17763782 |
| publication_date | 2025-11-29 |
| publication_year | 2025 |
| referenced_works_count | 0 |
| abstract_inverted_index.A | 174 |
| abstract_inverted_index.a | 4, 55, 149, 164, 168 |
| abstract_inverted_index.It | 24 |
| abstract_inverted_index.as | 28, 119 |
| abstract_inverted_index.at | 18 |
| abstract_inverted_index.by | 66 |
| abstract_inverted_index.is | 161, 167, 185 |
| abstract_inverted_index.of | 7, 15 |
| abstract_inverted_index.on | 58, 88 |
| abstract_inverted_index.to | 45, 105 |
| abstract_inverted_index.The | 111 |
| abstract_inverted_index.and | 11, 21, 36, 50, 79, 84, 92, 108, 130, 141, 151, 171, 182, 191 |
| abstract_inverted_index.are | 145 |
| abstract_inverted_index.due | 44 |
| abstract_inverted_index.for | 147, 187 |
| abstract_inverted_index.has | 100 |
| abstract_inverted_index.how | 26, 98 |
| abstract_inverted_index.low | 73 |
| abstract_inverted_index.not | 162 |
| abstract_inverted_index.the | 12, 60, 63, 156 |
| abstract_inverted_index.This | 0 |
| abstract_inverted_index.With | 54 |
| abstract_inverted_index.both | 19 |
| abstract_inverted_index.from | 102 |
| abstract_inverted_index.such | 118 |
| abstract_inverted_index.that | 159 |
| abstract_inverted_index.this | 95 |
| abstract_inverted_index.with | 136 |
| abstract_inverted_index.work | 96 |
| abstract_inverted_index.These | 133 |
| abstract_inverted_index.cyber | 197 |
| abstract_inverted_index.faced | 65 |
| abstract_inverted_index.focus | 57 |
| abstract_inverted_index.legal | 143 |
| abstract_inverted_index.paper | 2, 112 |
| abstract_inverted_index.rapid | 46 |
| abstract_inverted_index.risks | 17 |
| abstract_inverted_index.study | 61, 157 |
| abstract_inverted_index.(DDoS) | 39 |
| abstract_inverted_index.become | 41 |
| abstract_inverted_index.global | 20, 183 |
| abstract_inverted_index.merely | 163 |
| abstract_inverted_index.modern | 8, 115 |
| abstract_inverted_index.policy | 131 |
| abstract_inverted_index.public | 137 |
| abstract_inverted_index.recent | 89 |
| abstract_inverted_index.rising | 80 |
| abstract_inverted_index.secure | 152 |
| abstract_inverted_index.social | 34 |
| abstract_inverted_index.strong | 142 |
| abstract_inverted_index.theft, | 33 |
| abstract_inverted_index.threat | 90 |
| abstract_inverted_index.tools, | 134 |
| abstract_inverted_index.usage. | 53 |
| abstract_inverted_index.Drawing | 87 |
| abstract_inverted_index.against | 195 |
| abstract_inverted_index.attacks | 104 |
| abstract_inverted_index.crucial | 186 |
| abstract_inverted_index.defense | 116 |
| abstract_inverted_index.digital | 16, 68, 153, 189 |
| abstract_inverted_index.ethical | 125 |
| abstract_inverted_index.further | 113 |
| abstract_inverted_index.levels. | 23 |
| abstract_inverted_index.limited | 76 |
| abstract_inverted_index.machine | 122 |
| abstract_inverted_index.reports | 91 |
| abstract_inverted_index.shifted | 101 |
| abstract_inverted_index.skilled | 77, 179 |
| abstract_inverted_index.threats | 10 |
| abstract_inverted_index.Overall, | 155 |
| abstract_inverted_index.academic | 93 |
| abstract_inverted_index.analysis | 6 |
| abstract_inverted_index.approach | 176 |
| abstract_inverted_index.building | 148 |
| abstract_inverted_index.combined | 135 |
| abstract_inverted_index.emerging | 67 |
| abstract_inverted_index.ensuring | 192 |
| abstract_inverted_index.evolving | 13, 196 |
| abstract_inverted_index.examines | 25 |
| abstract_inverted_index.explores | 114 |
| abstract_inverted_index.hacking, | 126 |
| abstract_inverted_index.identity | 32 |
| abstract_inverted_index.internet | 52 |
| abstract_inverted_index.isolated | 103 |
| abstract_inverted_index.malware, | 29 |
| abstract_inverted_index.national | 22, 172 |
| abstract_inverted_index.outdated | 71 |
| abstract_inverted_index.outlines | 97 |
| abstract_inverted_index.provides | 3 |
| abstract_inverted_index.research | 1 |
| abstract_inverted_index.sectors. | 86 |
| abstract_inverted_index.systems, | 129 |
| abstract_inverted_index.threats. | 198 |
| abstract_inverted_index.detection | 128 |
| abstract_inverted_index.economic, | 170 |
| abstract_inverted_index.essential | 146 |
| abstract_inverted_index.financial | 83 |
| abstract_inverted_index.incidents | 81 |
| abstract_inverted_index.including | 70 |
| abstract_inverted_index.intrusion | 127 |
| abstract_inverted_index.involving | 177 |
| abstract_inverted_index.landscape | 14 |
| abstract_inverted_index.learning, | 123 |
| abstract_inverted_index.long-term | 193 |
| abstract_inverted_index.phishing, | 30 |
| abstract_inverted_index.policies, | 181 |
| abstract_inverted_index.priority. | 173 |
| abstract_inverted_index.targeting | 82 |
| abstract_inverted_index.technical | 165 |
| abstract_inverted_index.artificial | 120 |
| abstract_inverted_index.automated, | 107 |
| abstract_inverted_index.awareness, | 75, 138 |
| abstract_inverted_index.challenges | 64 |
| abstract_inverted_index.cybercrime | 99 |
| abstract_inverted_index.economies, | 69 |
| abstract_inverted_index.ecosystem. | 154 |
| abstract_inverted_index.emphasizes | 158 |
| abstract_inverted_index.highlights | 62 |
| abstract_inverted_index.issue—it | 166 |
| abstract_inverted_index.mechanisms | 117 |
| abstract_inverted_index.particular | 56 |
| abstract_inverted_index.readiness, | 140 |
| abstract_inverted_index.resilience | 194 |
| abstract_inverted_index.strategic, | 169 |
| abstract_inverted_index.widespread | 51 |
| abstract_inverted_index.Bangladesh, | 59 |
| abstract_inverted_index.cooperation | 184 |
| abstract_inverted_index.coordinated | 175 |
| abstract_inverted_index.data-driven | 109 |
| abstract_inverted_index.distributed | 37 |
| abstract_inverted_index.encryption, | 124 |
| abstract_inverted_index.frameworks. | 132 |
| abstract_inverted_index.literature, | 94 |
| abstract_inverted_index.operations. | 110 |
| abstract_inverted_index.ransomware, | 31 |
| abstract_inverted_index.sustainable | 150 |
| abstract_inverted_index.technology, | 178 |
| abstract_inverted_index.advancement, | 48 |
| abstract_inverted_index.engineering, | 35 |
| abstract_inverted_index.foundations, | 144 |
| abstract_inverted_index.governmental | 85 |
| abstract_inverted_index.increasingly | 42 |
| abstract_inverted_index.safeguarding | 188 |
| abstract_inverted_index.comprehensive | 5 |
| abstract_inverted_index.cybersecurity | 9, 74, 160 |
| abstract_inverted_index.institutional | 139 |
| abstract_inverted_index.intelligence, | 121 |
| abstract_inverted_index.sophisticated | 43 |
| abstract_inverted_index.technological | 47 |
| abstract_inverted_index.attacks—have | 40 |
| abstract_inverted_index.professionals, | 78, 180 |
| abstract_inverted_index.digitalization, | 49 |
| abstract_inverted_index.infrastructure, | 72 |
| abstract_inverted_index.infrastructures | 190 |
| abstract_inverted_index.well-organized, | 106 |
| abstract_inverted_index.denial-of-service | 38 |
| abstract_inverted_index.cyberattacks—such | 27 |
| cited_by_percentile_year | |
| countries_distinct_count | 1 |
| institutions_distinct_count | 1 |
| citation_normalized_percentile |