Design and Modeling of a Corporate Network Using VLAN and ACL to Enhance Network Security Article Swipe
Podskrebkin, Sergey
,
Serik, Darkan
·
 YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.5281/zenodo.17589177
YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.5281/zenodo.17589177
 YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.5281/zenodo.17589177
YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.5281/zenodo.17589177
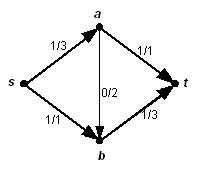
This paper presents the design and modeling of a secure corporate network architecture using VLAN segmentation and Access Control Lists (ACLs). The main objective of the study is to enhance network security, improve traffic management, and minimize unauthorized access. The proposed model demonstrates how VLANs can be effectively used to separate departments logically while maintaining efficient inter-VLAN communication through Layer 3 devices. ACLs are implemented to restrict sensitive data flow and enforce network policies. The results show that the designed network provides improved security, scalability, and performance suitable for modern enterprise environments.
Related Topics
Concepts
Virtual LAN
Computer network
Computer science
Network security
Computer security
Network Access Control
Network architecture
Layer (electronics)
Access control
Access network
Control (management)
Network planning and design
Data security
Enterprise private network
Architecture
Network information system
Flow network
Telecommunications network
Data modeling
Network management station
Enterprise information security architecture
Firewall (physics)
Local area network
Application layer
Server
Network layer
Security controls
Network model
Data access layer
Metadata
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.5281/zenodo.17589177
- OA Status
- green
- OpenAlex ID
- https://openalex.org/W7105539505
All OpenAlex metadata
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W7105539505Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.5281/zenodo.17589177Digital Object Identifier
- Title
-
Design and Modeling of a Corporate Network Using VLAN and ACL to Enhance Network SecurityWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2025Year of publication
- Publication date
-
2025-11-12Full publication date if available
- Authors
-
Podskrebkin, Sergey, Serik, DarkanList of authors in order
- Landing page
-
https://doi.org/10.5281/zenodo.17589177Publisher landing page
- Open access
-
YesWhether a free full text is available
- OA status
-
greenOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.5281/zenodo.17589177Direct OA link when available
- Concepts
-
Virtual LAN, Computer network, Computer science, Network security, Computer security, Network Access Control, Network architecture, Layer (electronics), Access control, Access network, Control (management), Network planning and design, Data security, Enterprise private network, Architecture, Network information system, Flow network, Telecommunications network, Data modeling, Network management station, Enterprise information security architecture, Firewall (physics), Local area network, Application layer, Server, Network layer, Security controls, Network model, Data access layerTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
0Total citation count in OpenAlex
Full payload
| id | https://openalex.org/W7105539505 |
|---|---|
| doi | https://doi.org/10.5281/zenodo.17589177 |
| ids.doi | https://doi.org/10.5281/zenodo.17589177 |
| ids.openalex | https://openalex.org/W7105539505 |
| fwci | 0.0 |
| type | article |
| title | Design and Modeling of a Corporate Network Using VLAN and ACL to Enhance Network Security |
| biblio.issue | |
| biblio.volume | |
| biblio.last_page | |
| biblio.first_page | |
| topics[0].id | https://openalex.org/T12326 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.280842125415802 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1708 |
| topics[0].subfield.display_name | Hardware and Architecture |
| topics[0].display_name | Network Packet Processing and Optimization |
| topics[1].id | https://openalex.org/T10714 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.2330884337425232 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1705 |
| topics[1].subfield.display_name | Computer Networks and Communications |
| topics[1].display_name | Software-Defined Networks and 5G |
| topics[2].id | https://openalex.org/T12203 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.08001961559057236 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1705 |
| topics[2].subfield.display_name | Computer Networks and Communications |
| topics[2].display_name | Mobile Agent-Based Network Management |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C206505811 |
| concepts[0].level | 2 |
| concepts[0].score | 0.9081924557685852 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q16452 |
| concepts[0].display_name | Virtual LAN |
| concepts[1].id | https://openalex.org/C31258907 |
| concepts[1].level | 1 |
| concepts[1].score | 0.685390055179596 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q1301371 |
| concepts[1].display_name | Computer network |
| concepts[2].id | https://openalex.org/C41008148 |
| concepts[2].level | 0 |
| concepts[2].score | 0.6154422163963318 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[2].display_name | Computer science |
| concepts[3].id | https://openalex.org/C182590292 |
| concepts[3].level | 2 |
| concepts[3].score | 0.49511706829071045 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q989632 |
| concepts[3].display_name | Network security |
| concepts[4].id | https://openalex.org/C38652104 |
| concepts[4].level | 1 |
| concepts[4].score | 0.45076867938041687 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[4].display_name | Computer security |
| concepts[5].id | https://openalex.org/C14982408 |
| concepts[5].level | 4 |
| concepts[5].score | 0.4488573968410492 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q11006334 |
| concepts[5].display_name | Network Access Control |
| concepts[6].id | https://openalex.org/C193415008 |
| concepts[6].level | 2 |
| concepts[6].score | 0.446895033121109 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q639681 |
| concepts[6].display_name | Network architecture |
| concepts[7].id | https://openalex.org/C2779227376 |
| concepts[7].level | 2 |
| concepts[7].score | 0.3935876190662384 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q6505497 |
| concepts[7].display_name | Layer (electronics) |
| concepts[8].id | https://openalex.org/C527821871 |
| concepts[8].level | 2 |
| concepts[8].score | 0.3365499973297119 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q228502 |
| concepts[8].display_name | Access control |
| concepts[9].id | https://openalex.org/C62793504 |
| concepts[9].level | 2 |
| concepts[9].score | 0.3346395790576935 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q228327 |
| concepts[9].display_name | Access network |
| concepts[10].id | https://openalex.org/C2775924081 |
| concepts[10].level | 2 |
| concepts[10].score | 0.33290302753448486 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q55608371 |
| concepts[10].display_name | Control (management) |
| concepts[11].id | https://openalex.org/C114563136 |
| concepts[11].level | 2 |
| concepts[11].score | 0.32588332891464233 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q19725982 |
| concepts[11].display_name | Network planning and design |
| concepts[12].id | https://openalex.org/C10511746 |
| concepts[12].level | 3 |
| concepts[12].score | 0.31815117597579956 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q899388 |
| concepts[12].display_name | Data security |
| concepts[13].id | https://openalex.org/C149859251 |
| concepts[13].level | 2 |
| concepts[13].score | 0.3095897138118744 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q483426 |
| concepts[13].display_name | Enterprise private network |
| concepts[14].id | https://openalex.org/C123657996 |
| concepts[14].level | 2 |
| concepts[14].score | 0.30799511075019836 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q12271 |
| concepts[14].display_name | Architecture |
| concepts[15].id | https://openalex.org/C25536438 |
| concepts[15].level | 4 |
| concepts[15].score | 0.3076908588409424 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q1549841 |
| concepts[15].display_name | Network information system |
| concepts[16].id | https://openalex.org/C114809511 |
| concepts[16].level | 2 |
| concepts[16].score | 0.30189067125320435 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q1412924 |
| concepts[16].display_name | Flow network |
| concepts[17].id | https://openalex.org/C192126672 |
| concepts[17].level | 2 |
| concepts[17].score | 0.30072611570358276 |
| concepts[17].wikidata | https://www.wikidata.org/wiki/Q1068715 |
| concepts[17].display_name | Telecommunications network |
| concepts[18].id | https://openalex.org/C67186912 |
| concepts[18].level | 2 |
| concepts[18].score | 0.3000902831554413 |
| concepts[18].wikidata | https://www.wikidata.org/wiki/Q367664 |
| concepts[18].display_name | Data modeling |
| concepts[19].id | https://openalex.org/C16986412 |
| concepts[19].level | 3 |
| concepts[19].score | 0.2846873998641968 |
| concepts[19].wikidata | https://www.wikidata.org/wiki/Q918419 |
| concepts[19].display_name | Network management station |
| concepts[20].id | https://openalex.org/C31139447 |
| concepts[20].level | 2 |
| concepts[20].score | 0.27402082085609436 |
| concepts[20].wikidata | https://www.wikidata.org/wiki/Q5380386 |
| concepts[20].display_name | Enterprise information security architecture |
| concepts[21].id | https://openalex.org/C77714075 |
| concepts[21].level | 5 |
| concepts[21].score | 0.2677331268787384 |
| concepts[21].wikidata | https://www.wikidata.org/wiki/Q5452017 |
| concepts[21].display_name | Firewall (physics) |
| concepts[22].id | https://openalex.org/C137471899 |
| concepts[22].level | 2 |
| concepts[22].score | 0.2674126923084259 |
| concepts[22].wikidata | https://www.wikidata.org/wiki/Q11381 |
| concepts[22].display_name | Local area network |
| concepts[23].id | https://openalex.org/C190793597 |
| concepts[23].level | 3 |
| concepts[23].score | 0.262834370136261 |
| concepts[23].wikidata | https://www.wikidata.org/wiki/Q189768 |
| concepts[23].display_name | Application layer |
| concepts[24].id | https://openalex.org/C93996380 |
| concepts[24].level | 2 |
| concepts[24].score | 0.25986823439598083 |
| concepts[24].wikidata | https://www.wikidata.org/wiki/Q44127 |
| concepts[24].display_name | Server |
| concepts[25].id | https://openalex.org/C117468950 |
| concepts[25].level | 3 |
| concepts[25].score | 0.25910523533821106 |
| concepts[25].wikidata | https://www.wikidata.org/wiki/Q208074 |
| concepts[25].display_name | Network layer |
| concepts[26].id | https://openalex.org/C178148461 |
| concepts[26].level | 3 |
| concepts[26].score | 0.25803831219673157 |
| concepts[26].wikidata | https://www.wikidata.org/wiki/Q1632136 |
| concepts[26].display_name | Security controls |
| concepts[27].id | https://openalex.org/C104122410 |
| concepts[27].level | 2 |
| concepts[27].score | 0.25744181871414185 |
| concepts[27].wikidata | https://www.wikidata.org/wiki/Q1416406 |
| concepts[27].display_name | Network model |
| concepts[28].id | https://openalex.org/C20277647 |
| concepts[28].level | 3 |
| concepts[28].score | 0.25403061509132385 |
| concepts[28].wikidata | https://www.wikidata.org/wiki/Q5227234 |
| concepts[28].display_name | Data access layer |
| keywords[0].id | https://openalex.org/keywords/virtual-lan |
| keywords[0].score | 0.9081924557685852 |
| keywords[0].display_name | Virtual LAN |
| keywords[1].id | https://openalex.org/keywords/network-security |
| keywords[1].score | 0.49511706829071045 |
| keywords[1].display_name | Network security |
| keywords[2].id | https://openalex.org/keywords/network-access-control |
| keywords[2].score | 0.4488573968410492 |
| keywords[2].display_name | Network Access Control |
| keywords[3].id | https://openalex.org/keywords/network-architecture |
| keywords[3].score | 0.446895033121109 |
| keywords[3].display_name | Network architecture |
| keywords[4].id | https://openalex.org/keywords/layer |
| keywords[4].score | 0.3935876190662384 |
| keywords[4].display_name | Layer (electronics) |
| keywords[5].id | https://openalex.org/keywords/access-control |
| keywords[5].score | 0.3365499973297119 |
| keywords[5].display_name | Access control |
| keywords[6].id | https://openalex.org/keywords/access-network |
| keywords[6].score | 0.3346395790576935 |
| keywords[6].display_name | Access network |
| keywords[7].id | https://openalex.org/keywords/control |
| keywords[7].score | 0.33290302753448486 |
| keywords[7].display_name | Control (management) |
| keywords[8].id | https://openalex.org/keywords/network-planning-and-design |
| keywords[8].score | 0.32588332891464233 |
| keywords[8].display_name | Network planning and design |
| language | en |
| locations[0].id | doi:10.5281/zenodo.17589177 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4306400562 |
| locations[0].source.issn | |
| locations[0].source.type | repository |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | |
| locations[0].source.is_core | False |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | Zenodo (CERN European Organization for Nuclear Research) |
| locations[0].source.host_organization | https://openalex.org/I67311998 |
| locations[0].source.host_organization_name | European Organization for Nuclear Research |
| locations[0].source.host_organization_lineage | https://openalex.org/I67311998 |
| locations[0].license | cc-by |
| locations[0].pdf_url | |
| locations[0].version | |
| locations[0].raw_type | article-journal |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | False |
| locations[0].is_published | |
| locations[0].raw_source_name | |
| locations[0].landing_page_url | https://doi.org/10.5281/zenodo.17589177 |
| indexed_in | datacite |
| authorships[0].author.id | |
| authorships[0].author.orcid | |
| authorships[0].author.display_name | Podskrebkin, Sergey |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Podskrebkin, Sergey |
| authorships[0].is_corresponding | True |
| authorships[1].author.id | |
| authorships[1].author.orcid | |
| authorships[1].author.display_name | Serik, Darkan |
| authorships[1].author_position | last |
| authorships[1].raw_author_name | Serik, Darkan |
| authorships[1].is_corresponding | False |
| has_content.pdf | False |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.5281/zenodo.17589177 |
| open_access.oa_status | green |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-11-13T00:00:00 |
| display_name | Design and Modeling of a Corporate Network Using VLAN and ACL to Enhance Network Security |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-11-13T11:05:06.444514 |
| primary_topic.id | https://openalex.org/T12326 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.280842125415802 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1708 |
| primary_topic.subfield.display_name | Hardware and Architecture |
| primary_topic.display_name | Network Packet Processing and Optimization |
| cited_by_count | 0 |
| locations_count | 1 |
| best_oa_location.id | doi:10.5281/zenodo.17589177 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4306400562 |
| best_oa_location.source.issn | |
| best_oa_location.source.type | repository |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | |
| best_oa_location.source.is_core | False |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | Zenodo (CERN European Organization for Nuclear Research) |
| best_oa_location.source.host_organization | https://openalex.org/I67311998 |
| best_oa_location.source.host_organization_name | European Organization for Nuclear Research |
| best_oa_location.source.host_organization_lineage | https://openalex.org/I67311998 |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | |
| best_oa_location.version | |
| best_oa_location.raw_type | article-journal |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | False |
| best_oa_location.is_published | False |
| best_oa_location.raw_source_name | |
| best_oa_location.landing_page_url | https://doi.org/10.5281/zenodo.17589177 |
| primary_location.id | doi:10.5281/zenodo.17589177 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4306400562 |
| primary_location.source.issn | |
| primary_location.source.type | repository |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | |
| primary_location.source.is_core | False |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | Zenodo (CERN European Organization for Nuclear Research) |
| primary_location.source.host_organization | https://openalex.org/I67311998 |
| primary_location.source.host_organization_name | European Organization for Nuclear Research |
| primary_location.source.host_organization_lineage | https://openalex.org/I67311998 |
| primary_location.license | cc-by |
| primary_location.pdf_url | |
| primary_location.version | |
| primary_location.raw_type | article-journal |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | False |
| primary_location.is_published | False |
| primary_location.raw_source_name | |
| primary_location.landing_page_url | https://doi.org/10.5281/zenodo.17589177 |
| publication_date | 2025-11-12 |
| publication_year | 2025 |
| referenced_works_count | 0 |
| abstract_inverted_index.3 | 60 |
| abstract_inverted_index.a | 8 |
| abstract_inverted_index.be | 46 |
| abstract_inverted_index.is | 27 |
| abstract_inverted_index.of | 7, 24 |
| abstract_inverted_index.to | 28, 49, 65 |
| abstract_inverted_index.The | 21, 39, 74 |
| abstract_inverted_index.and | 5, 16, 35, 70, 85 |
| abstract_inverted_index.are | 63 |
| abstract_inverted_index.can | 45 |
| abstract_inverted_index.for | 88 |
| abstract_inverted_index.how | 43 |
| abstract_inverted_index.the | 3, 25, 78 |
| abstract_inverted_index.ACLs | 62 |
| abstract_inverted_index.This | 0 |
| abstract_inverted_index.VLAN | 14 |
| abstract_inverted_index.data | 68 |
| abstract_inverted_index.flow | 69 |
| abstract_inverted_index.main | 22 |
| abstract_inverted_index.show | 76 |
| abstract_inverted_index.that | 77 |
| abstract_inverted_index.used | 48 |
| abstract_inverted_index.Layer | 59 |
| abstract_inverted_index.Lists | 19 |
| abstract_inverted_index.VLANs | 44 |
| abstract_inverted_index.model | 41 |
| abstract_inverted_index.paper | 1 |
| abstract_inverted_index.study | 26 |
| abstract_inverted_index.using | 13 |
| abstract_inverted_index.while | 53 |
| abstract_inverted_index.Access | 17 |
| abstract_inverted_index.design | 4 |
| abstract_inverted_index.modern | 89 |
| abstract_inverted_index.secure | 9 |
| abstract_inverted_index.(ACLs). | 20 |
| abstract_inverted_index.Control | 18 |
| abstract_inverted_index.access. | 38 |
| abstract_inverted_index.enforce | 71 |
| abstract_inverted_index.enhance | 29 |
| abstract_inverted_index.improve | 32 |
| abstract_inverted_index.network | 11, 30, 72, 80 |
| abstract_inverted_index.results | 75 |
| abstract_inverted_index.through | 58 |
| abstract_inverted_index.traffic | 33 |
| abstract_inverted_index.designed | 79 |
| abstract_inverted_index.devices. | 61 |
| abstract_inverted_index.improved | 82 |
| abstract_inverted_index.minimize | 36 |
| abstract_inverted_index.modeling | 6 |
| abstract_inverted_index.presents | 2 |
| abstract_inverted_index.proposed | 40 |
| abstract_inverted_index.provides | 81 |
| abstract_inverted_index.restrict | 66 |
| abstract_inverted_index.separate | 50 |
| abstract_inverted_index.suitable | 87 |
| abstract_inverted_index.corporate | 10 |
| abstract_inverted_index.efficient | 55 |
| abstract_inverted_index.logically | 52 |
| abstract_inverted_index.objective | 23 |
| abstract_inverted_index.policies. | 73 |
| abstract_inverted_index.security, | 31, 83 |
| abstract_inverted_index.sensitive | 67 |
| abstract_inverted_index.enterprise | 90 |
| abstract_inverted_index.inter-VLAN | 56 |
| abstract_inverted_index.departments | 51 |
| abstract_inverted_index.effectively | 47 |
| abstract_inverted_index.implemented | 64 |
| abstract_inverted_index.maintaining | 54 |
| abstract_inverted_index.management, | 34 |
| abstract_inverted_index.performance | 86 |
| abstract_inverted_index.architecture | 12 |
| abstract_inverted_index.demonstrates | 42 |
| abstract_inverted_index.scalability, | 84 |
| abstract_inverted_index.segmentation | 15 |
| abstract_inverted_index.unauthorized | 37 |
| abstract_inverted_index.communication | 57 |
| abstract_inverted_index.environments. | 91 |
| cited_by_percentile_year | |
| countries_distinct_count | 0 |
| institutions_distinct_count | 2 |
| citation_normalized_percentile.value | 0.83243558 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |