DynBlock: dynamic data encryption with Toffoli gate for IoT Article Swipe
 YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.1038/s41598-025-02437-6
YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.1038/s41598-025-02437-6
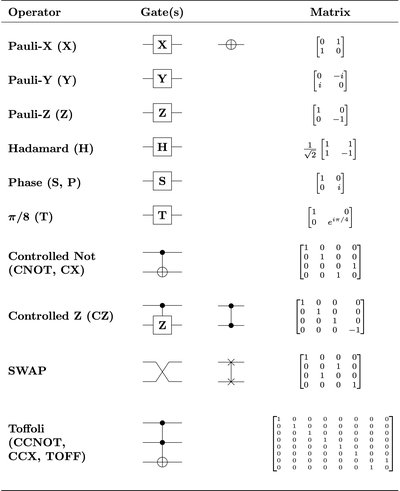
The emergence of 6G networks, coupled with the expansion of smart devices, necessitates robust and efficient cryptography solutions to ensure secure communication. However, the existing resource-constrained cryptography solutions that rely on static permutation, substitution methods, variable key sizes, and fixed block size are vulnerable to quantum computing-based cryptanalysis and side-channel attacks. To address these challenges, this paper proposes a lightweight dynamic block cipher (DynBlock) algorithm. DynBlock is specifically suitable for resource-limited devices, and features a dynamic block size (64-128 bits), which is adaptable to symmetric encryption key sizes. Additionally, DynBlock includes dynamic permutation and substitution layers that enhance confusion and diffusion properties, along with a novel substitution-permutation network (SPN) algorithm that eliminates conventional substitution- and permutation-boxes. DynBlock leverages Tofoli gates and XOR operations to reduce the number of computation operations required to achieve optimal throughput and energy efficiency. Security validation of DynBlock is performed considering various metrics, including an average key avalanche effect of 53.85%, average plain-text avalanche effect of 57.82%, differential cryptanalysis ([Formula: see text]), and cryptanalysis ([Formula: see text]). Performance is compared against various state-of-the-art schemes. We evaluate DynBlock with both 3 and 5 rounds to assess its security and computational efficiency. While the 5-round configuration offers stronger resistance to cryptanalytic attacks, the 3-round setup already delivers robust security, featuring high entropy and a strong avalanche effect, making it well-suited for resource-constrained environments. It is found that DynBlock significantly improves energy efficiency and throughput compared to its predecessors. Additionally, DynBlock demonstrates resistance to quantum computing-based attacks, improved side-channel attack resilience, and enhanced randomness and entropy.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.1038/s41598-025-02437-6
- https://www.nature.com/articles/s41598-025-02437-6.pdf
- OA Status
- gold
- Cited By
- 2
- References
- 30
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4410613100
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4410613100Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1038/s41598-025-02437-6Digital Object Identifier
- Title
-
DynBlock: dynamic data encryption with Toffoli gate for IoTWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2025Year of publication
- Publication date
-
2025-05-22Full publication date if available
- Authors
-
Muhammad Aziz Ul Haq, Ijaz Ali Shoukat, Alamgir Naushad, Mohsin Raza Jafri, Muhammad Moid Sandhu, Abd Ullah Khan, Hyundong ShinList of authors in order
- Landing page
-
https://doi.org/10.1038/s41598-025-02437-6Publisher landing page
- PDF URL
-
https://www.nature.com/articles/s41598-025-02437-6.pdfDirect link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
goldOpen access status per OpenAlex
- OA URL
-
https://www.nature.com/articles/s41598-025-02437-6.pdfDirect OA link when available
- Concepts
-
Toffoli gate, Computer science, Encryption, Embedded system, Computer security, Quantum gate, Quantum algorithm, Quantum mechanics, Quantum, PhysicsTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
2Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 2Per-year citation counts (last 5 years)
- References (count)
-
30Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4410613100 |
|---|---|
| doi | https://doi.org/10.1038/s41598-025-02437-6 |
| ids.doi | https://doi.org/10.1038/s41598-025-02437-6 |
| ids.pmid | https://pubmed.ncbi.nlm.nih.gov/40404679 |
| ids.openalex | https://openalex.org/W4410613100 |
| fwci | 9.54681462 |
| type | article |
| title | DynBlock: dynamic data encryption with Toffoli gate for IoT |
| biblio.issue | 1 |
| biblio.volume | 15 |
| biblio.last_page | 17864 |
| biblio.first_page | 17864 |
| topics[0].id | https://openalex.org/T11017 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9998999834060669 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1707 |
| topics[0].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[0].display_name | Chaos-based Image/Signal Encryption |
| topics[1].id | https://openalex.org/T10951 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9998999834060669 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1702 |
| topics[1].subfield.display_name | Artificial Intelligence |
| topics[1].display_name | Cryptographic Implementations and Security |
| topics[2].id | https://openalex.org/T10237 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9973999857902527 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1702 |
| topics[2].subfield.display_name | Artificial Intelligence |
| topics[2].display_name | Cryptography and Data Security |
| is_xpac | False |
| apc_list.value | 1890 |
| apc_list.currency | EUR |
| apc_list.value_usd | 2190 |
| apc_paid.value | 1890 |
| apc_paid.currency | EUR |
| apc_paid.value_usd | 2190 |
| concepts[0].id | https://openalex.org/C142465778 |
| concepts[0].level | 5 |
| concepts[0].score | 0.9428161382675171 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q2502619 |
| concepts[0].display_name | Toffoli gate |
| concepts[1].id | https://openalex.org/C41008148 |
| concepts[1].level | 0 |
| concepts[1].score | 0.7053426504135132 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[1].display_name | Computer science |
| concepts[2].id | https://openalex.org/C148730421 |
| concepts[2].level | 2 |
| concepts[2].score | 0.6877673864364624 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q141090 |
| concepts[2].display_name | Encryption |
| concepts[3].id | https://openalex.org/C149635348 |
| concepts[3].level | 1 |
| concepts[3].score | 0.32633036375045776 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q193040 |
| concepts[3].display_name | Embedded system |
| concepts[4].id | https://openalex.org/C38652104 |
| concepts[4].level | 1 |
| concepts[4].score | 0.28278017044067383 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[4].display_name | Computer security |
| concepts[5].id | https://openalex.org/C58849907 |
| concepts[5].level | 4 |
| concepts[5].score | 0.049505263566970825 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q2118982 |
| concepts[5].display_name | Quantum gate |
| concepts[6].id | https://openalex.org/C137019171 |
| concepts[6].level | 3 |
| concepts[6].score | 0.0 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q2623817 |
| concepts[6].display_name | Quantum algorithm |
| concepts[7].id | https://openalex.org/C62520636 |
| concepts[7].level | 1 |
| concepts[7].score | 0.0 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q944 |
| concepts[7].display_name | Quantum mechanics |
| concepts[8].id | https://openalex.org/C84114770 |
| concepts[8].level | 2 |
| concepts[8].score | 0.0 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q46344 |
| concepts[8].display_name | Quantum |
| concepts[9].id | https://openalex.org/C121332964 |
| concepts[9].level | 0 |
| concepts[9].score | 0.0 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q413 |
| concepts[9].display_name | Physics |
| keywords[0].id | https://openalex.org/keywords/toffoli-gate |
| keywords[0].score | 0.9428161382675171 |
| keywords[0].display_name | Toffoli gate |
| keywords[1].id | https://openalex.org/keywords/computer-science |
| keywords[1].score | 0.7053426504135132 |
| keywords[1].display_name | Computer science |
| keywords[2].id | https://openalex.org/keywords/encryption |
| keywords[2].score | 0.6877673864364624 |
| keywords[2].display_name | Encryption |
| keywords[3].id | https://openalex.org/keywords/embedded-system |
| keywords[3].score | 0.32633036375045776 |
| keywords[3].display_name | Embedded system |
| keywords[4].id | https://openalex.org/keywords/computer-security |
| keywords[4].score | 0.28278017044067383 |
| keywords[4].display_name | Computer security |
| keywords[5].id | https://openalex.org/keywords/quantum-gate |
| keywords[5].score | 0.049505263566970825 |
| keywords[5].display_name | Quantum gate |
| language | en |
| locations[0].id | doi:10.1038/s41598-025-02437-6 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S196734849 |
| locations[0].source.issn | 2045-2322 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2045-2322 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | Scientific Reports |
| locations[0].source.host_organization | https://openalex.org/P4310319908 |
| locations[0].source.host_organization_name | Nature Portfolio |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310319908, https://openalex.org/P4310319965 |
| locations[0].source.host_organization_lineage_names | Nature Portfolio, Springer Nature |
| locations[0].license | cc-by-nc-nd |
| locations[0].pdf_url | https://www.nature.com/articles/s41598-025-02437-6.pdf |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by-nc-nd |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Scientific Reports |
| locations[0].landing_page_url | https://doi.org/10.1038/s41598-025-02437-6 |
| locations[1].id | pmid:40404679 |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306525036 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | PubMed |
| locations[1].source.host_organization | https://openalex.org/I1299303238 |
| locations[1].source.host_organization_name | National Institutes of Health |
| locations[1].source.host_organization_lineage | https://openalex.org/I1299303238 |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | publishedVersion |
| locations[1].raw_type | |
| locations[1].license_id | |
| locations[1].is_accepted | True |
| locations[1].is_published | True |
| locations[1].raw_source_name | Scientific reports |
| locations[1].landing_page_url | https://pubmed.ncbi.nlm.nih.gov/40404679 |
| locations[2].id | pmh:oai:doaj.org/article:24d523d82a0344a7a922ef450606b4b8 |
| locations[2].is_oa | False |
| locations[2].source.id | https://openalex.org/S4306401280 |
| locations[2].source.issn | |
| locations[2].source.type | repository |
| locations[2].source.is_oa | False |
| locations[2].source.issn_l | |
| locations[2].source.is_core | False |
| locations[2].source.is_in_doaj | False |
| locations[2].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[2].source.host_organization | |
| locations[2].source.host_organization_name | |
| locations[2].license | |
| locations[2].pdf_url | |
| locations[2].version | submittedVersion |
| locations[2].raw_type | article |
| locations[2].license_id | |
| locations[2].is_accepted | False |
| locations[2].is_published | False |
| locations[2].raw_source_name | Scientific Reports, Vol 15, Iss 1, Pp 1-28 (2025) |
| locations[2].landing_page_url | https://doaj.org/article/24d523d82a0344a7a922ef450606b4b8 |
| indexed_in | crossref, doaj, pubmed |
| authorships[0].author.id | https://openalex.org/A5050181825 |
| authorships[0].author.orcid | |
| authorships[0].author.display_name | Muhammad Aziz Ul Haq |
| authorships[0].countries | PK |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I195024194 |
| authorships[0].affiliations[0].raw_affiliation_string | Department of Computing, Riphah International University, Faisalabad, 38000, Pakistan. |
| authorships[0].institutions[0].id | https://openalex.org/I195024194 |
| authorships[0].institutions[0].ror | https://ror.org/02kdm5630 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I195024194 |
| authorships[0].institutions[0].country_code | PK |
| authorships[0].institutions[0].display_name | Riphah International University |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Mubasher Haq |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Department of Computing, Riphah International University, Faisalabad, 38000, Pakistan. |
| authorships[1].author.id | https://openalex.org/A5040256864 |
| authorships[1].author.orcid | https://orcid.org/0000-0002-2456-6952 |
| authorships[1].author.display_name | Ijaz Ali Shoukat |
| authorships[1].countries | PK |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I195024194 |
| authorships[1].affiliations[0].raw_affiliation_string | Department of Computing, Riphah International University, Faisalabad, 38000, Pakistan. |
| authorships[1].institutions[0].id | https://openalex.org/I195024194 |
| authorships[1].institutions[0].ror | https://ror.org/02kdm5630 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I195024194 |
| authorships[1].institutions[0].country_code | PK |
| authorships[1].institutions[0].display_name | Riphah International University |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Ijaz Ali Shoukat |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Department of Computing, Riphah International University, Faisalabad, 38000, Pakistan. |
| authorships[2].author.id | https://openalex.org/A5017750499 |
| authorships[2].author.orcid | https://orcid.org/0000-0001-7009-1751 |
| authorships[2].author.display_name | Alamgir Naushad |
| authorships[2].countries | PK |
| authorships[2].affiliations[0].institution_ids | https://openalex.org/I20561161, https://openalex.org/I929597975 |
| authorships[2].affiliations[0].raw_affiliation_string | Department of Computer Science, National University of Sciences and Technology Balochistan Campus, Quetta, Pakistan. |
| authorships[2].institutions[0].id | https://openalex.org/I929597975 |
| authorships[2].institutions[0].ror | https://ror.org/03w2j5y17 |
| authorships[2].institutions[0].type | education |
| authorships[2].institutions[0].lineage | https://openalex.org/I929597975 |
| authorships[2].institutions[0].country_code | PK |
| authorships[2].institutions[0].display_name | National University of Sciences and Technology |
| authorships[2].institutions[1].id | https://openalex.org/I20561161 |
| authorships[2].institutions[1].ror | https://ror.org/04bf33n91 |
| authorships[2].institutions[1].type | education |
| authorships[2].institutions[1].lineage | https://openalex.org/I20561161 |
| authorships[2].institutions[1].country_code | PK |
| authorships[2].institutions[1].display_name | University of Balochistan |
| authorships[2].author_position | middle |
| authorships[2].raw_author_name | Alamgir Naushad |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | Department of Computer Science, National University of Sciences and Technology Balochistan Campus, Quetta, Pakistan. |
| authorships[3].author.id | https://openalex.org/A5090244754 |
| authorships[3].author.orcid | https://orcid.org/0000-0001-5197-4399 |
| authorships[3].author.display_name | Mohsin Raza Jafri |
| authorships[3].countries | PK |
| authorships[3].affiliations[0].institution_ids | https://openalex.org/I20561161, https://openalex.org/I929597975 |
| authorships[3].affiliations[0].raw_affiliation_string | Department of Computer Science, National University of Sciences and Technology Balochistan Campus, Quetta, Pakistan. |
| authorships[3].institutions[0].id | https://openalex.org/I929597975 |
| authorships[3].institutions[0].ror | https://ror.org/03w2j5y17 |
| authorships[3].institutions[0].type | education |
| authorships[3].institutions[0].lineage | https://openalex.org/I929597975 |
| authorships[3].institutions[0].country_code | PK |
| authorships[3].institutions[0].display_name | National University of Sciences and Technology |
| authorships[3].institutions[1].id | https://openalex.org/I20561161 |
| authorships[3].institutions[1].ror | https://ror.org/04bf33n91 |
| authorships[3].institutions[1].type | education |
| authorships[3].institutions[1].lineage | https://openalex.org/I20561161 |
| authorships[3].institutions[1].country_code | PK |
| authorships[3].institutions[1].display_name | University of Balochistan |
| authorships[3].author_position | middle |
| authorships[3].raw_author_name | Mohsin Raza Jafri |
| authorships[3].is_corresponding | False |
| authorships[3].raw_affiliation_strings | Department of Computer Science, National University of Sciences and Technology Balochistan Campus, Quetta, Pakistan. |
| authorships[4].author.id | https://openalex.org/A5036123093 |
| authorships[4].author.orcid | https://orcid.org/0000-0001-6444-0900 |
| authorships[4].author.display_name | Muhammad Moid Sandhu |
| authorships[4].countries | AU |
| authorships[4].affiliations[0].institution_ids | https://openalex.org/I1292875679, https://openalex.org/I4210141844 |
| authorships[4].affiliations[0].raw_affiliation_string | Australian e-Health Research Centre (AEHRC), CSIRO, Brisbane, Australia. |
| authorships[4].affiliations[1].institution_ids | https://openalex.org/I160993911 |
| authorships[4].affiliations[1].raw_affiliation_string | Queensland University of Technology, Brisbane, Australia. |
| authorships[4].institutions[0].id | https://openalex.org/I4210141844 |
| authorships[4].institutions[0].ror | https://ror.org/04ywhbc61 |
| authorships[4].institutions[0].type | facility |
| authorships[4].institutions[0].lineage | https://openalex.org/I1292875679, https://openalex.org/I2801244131, https://openalex.org/I2801453606, https://openalex.org/I4210141844, https://openalex.org/I4387156119 |
| authorships[4].institutions[0].country_code | AU |
| authorships[4].institutions[0].display_name | Australian e-Health Research Centre |
| authorships[4].institutions[1].id | https://openalex.org/I1292875679 |
| authorships[4].institutions[1].ror | https://ror.org/03qn8fb07 |
| authorships[4].institutions[1].type | government |
| authorships[4].institutions[1].lineage | https://openalex.org/I1292875679, https://openalex.org/I2801453606, https://openalex.org/I4387156119 |
| authorships[4].institutions[1].country_code | AU |
| authorships[4].institutions[1].display_name | Commonwealth Scientific and Industrial Research Organisation |
| authorships[4].institutions[2].id | https://openalex.org/I160993911 |
| authorships[4].institutions[2].ror | https://ror.org/03pnv4752 |
| authorships[4].institutions[2].type | education |
| authorships[4].institutions[2].lineage | https://openalex.org/I160993911 |
| authorships[4].institutions[2].country_code | AU |
| authorships[4].institutions[2].display_name | Queensland University of Technology |
| authorships[4].author_position | middle |
| authorships[4].raw_author_name | Moid Sandhu |
| authorships[4].is_corresponding | False |
| authorships[4].raw_affiliation_strings | Australian e-Health Research Centre (AEHRC), CSIRO, Brisbane, Australia., Queensland University of Technology, Brisbane, Australia. |
| authorships[5].author.id | https://openalex.org/A5000151549 |
| authorships[5].author.orcid | https://orcid.org/0000-0001-8523-9931 |
| authorships[5].author.display_name | Abd Ullah Khan |
| authorships[5].countries | KR, PK |
| authorships[5].affiliations[0].institution_ids | https://openalex.org/I35928602 |
| authorships[5].affiliations[0].raw_affiliation_string | CQI Lab, Department of Information and Electronics Convergence Engineering, Kyung Hee University, Yongin 17104, Gyeonggi, South Korea. |
| authorships[5].affiliations[1].institution_ids | https://openalex.org/I20561161, https://openalex.org/I929597975 |
| authorships[5].affiliations[1].raw_affiliation_string | Department of Computer Science, National University of Sciences and Technology Balochistan Campus, Quetta, Pakistan. |
| authorships[5].institutions[0].id | https://openalex.org/I35928602 |
| authorships[5].institutions[0].ror | https://ror.org/01zqcg218 |
| authorships[5].institutions[0].type | education |
| authorships[5].institutions[0].lineage | https://openalex.org/I35928602 |
| authorships[5].institutions[0].country_code | KR |
| authorships[5].institutions[0].display_name | Kyung Hee University |
| authorships[5].institutions[1].id | https://openalex.org/I929597975 |
| authorships[5].institutions[1].ror | https://ror.org/03w2j5y17 |
| authorships[5].institutions[1].type | education |
| authorships[5].institutions[1].lineage | https://openalex.org/I929597975 |
| authorships[5].institutions[1].country_code | PK |
| authorships[5].institutions[1].display_name | National University of Sciences and Technology |
| authorships[5].institutions[2].id | https://openalex.org/I20561161 |
| authorships[5].institutions[2].ror | https://ror.org/04bf33n91 |
| authorships[5].institutions[2].type | education |
| authorships[5].institutions[2].lineage | https://openalex.org/I20561161 |
| authorships[5].institutions[2].country_code | PK |
| authorships[5].institutions[2].display_name | University of Balochistan |
| authorships[5].author_position | middle |
| authorships[5].raw_author_name | Abd Ullah Khan |
| authorships[5].is_corresponding | False |
| authorships[5].raw_affiliation_strings | CQI Lab, Department of Information and Electronics Convergence Engineering, Kyung Hee University, Yongin 17104, Gyeonggi, South Korea., Department of Computer Science, National University of Sciences and Technology Balochistan Campus, Quetta, Pakistan. |
| authorships[6].author.id | https://openalex.org/A5007557286 |
| authorships[6].author.orcid | https://orcid.org/0000-0003-3364-8084 |
| authorships[6].author.display_name | Hyundong Shin |
| authorships[6].countries | KR |
| authorships[6].affiliations[0].institution_ids | https://openalex.org/I35928602 |
| authorships[6].affiliations[0].raw_affiliation_string | CQI Lab, Department of Information and Electronics Convergence Engineering, Kyung Hee University, Yongin 17104, Gyeonggi, South Korea. [email protected]. |
| authorships[6].institutions[0].id | https://openalex.org/I35928602 |
| authorships[6].institutions[0].ror | https://ror.org/01zqcg218 |
| authorships[6].institutions[0].type | education |
| authorships[6].institutions[0].lineage | https://openalex.org/I35928602 |
| authorships[6].institutions[0].country_code | KR |
| authorships[6].institutions[0].display_name | Kyung Hee University |
| authorships[6].author_position | last |
| authorships[6].raw_author_name | Hyundong Shin |
| authorships[6].is_corresponding | False |
| authorships[6].raw_affiliation_strings | CQI Lab, Department of Information and Electronics Convergence Engineering, Kyung Hee University, Yongin 17104, Gyeonggi, South Korea. [email protected]. |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://www.nature.com/articles/s41598-025-02437-6.pdf |
| open_access.oa_status | gold |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | DynBlock: dynamic data encryption with Toffoli gate for IoT |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T11017 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9998999834060669 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1707 |
| primary_topic.subfield.display_name | Computer Vision and Pattern Recognition |
| primary_topic.display_name | Chaos-based Image/Signal Encryption |
| related_works | https://openalex.org/W4391375266, https://openalex.org/W2899084033, https://openalex.org/W2748952813, https://openalex.org/W2529811130, https://openalex.org/W2772794421, https://openalex.org/W2888416745, https://openalex.org/W2065951251, https://openalex.org/W4378942754, https://openalex.org/W3094850919, https://openalex.org/W2609567360 |
| cited_by_count | 2 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 2 |
| locations_count | 3 |
| best_oa_location.id | doi:10.1038/s41598-025-02437-6 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S196734849 |
| best_oa_location.source.issn | 2045-2322 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2045-2322 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | Scientific Reports |
| best_oa_location.source.host_organization | https://openalex.org/P4310319908 |
| best_oa_location.source.host_organization_name | Nature Portfolio |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310319908, https://openalex.org/P4310319965 |
| best_oa_location.source.host_organization_lineage_names | Nature Portfolio, Springer Nature |
| best_oa_location.license | cc-by-nc-nd |
| best_oa_location.pdf_url | https://www.nature.com/articles/s41598-025-02437-6.pdf |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by-nc-nd |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Scientific Reports |
| best_oa_location.landing_page_url | https://doi.org/10.1038/s41598-025-02437-6 |
| primary_location.id | doi:10.1038/s41598-025-02437-6 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S196734849 |
| primary_location.source.issn | 2045-2322 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2045-2322 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | Scientific Reports |
| primary_location.source.host_organization | https://openalex.org/P4310319908 |
| primary_location.source.host_organization_name | Nature Portfolio |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310319908, https://openalex.org/P4310319965 |
| primary_location.source.host_organization_lineage_names | Nature Portfolio, Springer Nature |
| primary_location.license | cc-by-nc-nd |
| primary_location.pdf_url | https://www.nature.com/articles/s41598-025-02437-6.pdf |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by-nc-nd |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Scientific Reports |
| primary_location.landing_page_url | https://doi.org/10.1038/s41598-025-02437-6 |
| publication_date | 2025-05-22 |
| publication_year | 2025 |
| referenced_works | https://openalex.org/W4386999093, https://openalex.org/W4391092662, https://openalex.org/W4296186755, https://openalex.org/W4385686669, https://openalex.org/W3109885655, https://openalex.org/W3144608547, https://openalex.org/W4295854922, https://openalex.org/W4213251754, https://openalex.org/W4286374875, https://openalex.org/W4316038625, https://openalex.org/W4389267612, https://openalex.org/W1572300106, https://openalex.org/W2087928947, https://openalex.org/W2483773531, https://openalex.org/W4252387494, https://openalex.org/W4294915434, https://openalex.org/W4210861543, https://openalex.org/W3211241118, https://openalex.org/W3133710726, https://openalex.org/W3123199486, https://openalex.org/W4290724734, https://openalex.org/W3206102117, https://openalex.org/W3036147309, https://openalex.org/W3087738966, https://openalex.org/W4362472673, https://openalex.org/W1522919234, https://openalex.org/W1904723009, https://openalex.org/W2027467269, https://openalex.org/W2595168141, https://openalex.org/W3127657877 |
| referenced_works_count | 30 |
| abstract_inverted_index.3 | 183 |
| abstract_inverted_index.5 | 185 |
| abstract_inverted_index.a | 58, 74, 104, 215 |
| abstract_inverted_index.6G | 3 |
| abstract_inverted_index.It | 225 |
| abstract_inverted_index.To | 51 |
| abstract_inverted_index.We | 178 |
| abstract_inverted_index.an | 148 |
| abstract_inverted_index.is | 66, 81, 142, 172, 226 |
| abstract_inverted_index.it | 220 |
| abstract_inverted_index.of | 2, 9, 127, 140, 153, 159 |
| abstract_inverted_index.on | 30 |
| abstract_inverted_index.to | 18, 44, 83, 123, 131, 187, 201, 237, 244 |
| abstract_inverted_index.The | 0 |
| abstract_inverted_index.XOR | 121 |
| abstract_inverted_index.and | 14, 38, 48, 72, 93, 99, 114, 120, 135, 166, 184, 191, 214, 234, 252, 255 |
| abstract_inverted_index.are | 42 |
| abstract_inverted_index.for | 69, 222 |
| abstract_inverted_index.its | 189, 238 |
| abstract_inverted_index.key | 36, 86, 150 |
| abstract_inverted_index.see | 164, 169 |
| abstract_inverted_index.the | 7, 23, 125, 195, 204 |
| abstract_inverted_index.both | 182 |
| abstract_inverted_index.high | 212 |
| abstract_inverted_index.rely | 29 |
| abstract_inverted_index.size | 41, 77 |
| abstract_inverted_index.that | 28, 96, 110, 228 |
| abstract_inverted_index.this | 55 |
| abstract_inverted_index.with | 6, 103, 181 |
| abstract_inverted_index.(SPN) | 108 |
| abstract_inverted_index.While | 194 |
| abstract_inverted_index.along | 102 |
| abstract_inverted_index.block | 40, 61, 76 |
| abstract_inverted_index.fixed | 39 |
| abstract_inverted_index.found | 227 |
| abstract_inverted_index.gates | 119 |
| abstract_inverted_index.novel | 105 |
| abstract_inverted_index.paper | 56 |
| abstract_inverted_index.setup | 206 |
| abstract_inverted_index.smart | 10 |
| abstract_inverted_index.these | 53 |
| abstract_inverted_index.which | 80 |
| abstract_inverted_index.Tofoli | 118 |
| abstract_inverted_index.assess | 188 |
| abstract_inverted_index.attack | 250 |
| abstract_inverted_index.bits), | 79 |
| abstract_inverted_index.cipher | 62 |
| abstract_inverted_index.effect | 152, 158 |
| abstract_inverted_index.energy | 136, 232 |
| abstract_inverted_index.ensure | 19 |
| abstract_inverted_index.layers | 95 |
| abstract_inverted_index.making | 219 |
| abstract_inverted_index.number | 126 |
| abstract_inverted_index.offers | 198 |
| abstract_inverted_index.reduce | 124 |
| abstract_inverted_index.robust | 13, 209 |
| abstract_inverted_index.rounds | 186 |
| abstract_inverted_index.secure | 20 |
| abstract_inverted_index.sizes, | 37 |
| abstract_inverted_index.sizes. | 87 |
| abstract_inverted_index.static | 31 |
| abstract_inverted_index.strong | 216 |
| abstract_inverted_index.(64-128 | 78 |
| abstract_inverted_index.3-round | 205 |
| abstract_inverted_index.5-round | 196 |
| abstract_inverted_index.53.85%, | 154 |
| abstract_inverted_index.57.82%, | 160 |
| abstract_inverted_index.achieve | 132 |
| abstract_inverted_index.address | 52 |
| abstract_inverted_index.against | 174 |
| abstract_inverted_index.already | 207 |
| abstract_inverted_index.average | 149, 155 |
| abstract_inverted_index.coupled | 5 |
| abstract_inverted_index.dynamic | 60, 75, 91 |
| abstract_inverted_index.effect, | 218 |
| abstract_inverted_index.enhance | 97 |
| abstract_inverted_index.entropy | 213 |
| abstract_inverted_index.network | 107 |
| abstract_inverted_index.optimal | 133 |
| abstract_inverted_index.quantum | 45, 245 |
| abstract_inverted_index.text]), | 165 |
| abstract_inverted_index.text]). | 170 |
| abstract_inverted_index.various | 145, 175 |
| abstract_inverted_index.DynBlock | 65, 89, 116, 141, 180, 229, 241 |
| abstract_inverted_index.However, | 22 |
| abstract_inverted_index.Security | 138 |
| abstract_inverted_index.attacks, | 203, 247 |
| abstract_inverted_index.attacks. | 50 |
| abstract_inverted_index.compared | 173, 236 |
| abstract_inverted_index.delivers | 208 |
| abstract_inverted_index.devices, | 11, 71 |
| abstract_inverted_index.enhanced | 253 |
| abstract_inverted_index.entropy. | 256 |
| abstract_inverted_index.evaluate | 179 |
| abstract_inverted_index.existing | 24 |
| abstract_inverted_index.features | 73 |
| abstract_inverted_index.improved | 248 |
| abstract_inverted_index.improves | 231 |
| abstract_inverted_index.includes | 90 |
| abstract_inverted_index.methods, | 34 |
| abstract_inverted_index.metrics, | 146 |
| abstract_inverted_index.proposes | 57 |
| abstract_inverted_index.required | 130 |
| abstract_inverted_index.schemes. | 177 |
| abstract_inverted_index.security | 190 |
| abstract_inverted_index.stronger | 199 |
| abstract_inverted_index.suitable | 68 |
| abstract_inverted_index.variable | 35 |
| abstract_inverted_index.adaptable | 82 |
| abstract_inverted_index.algorithm | 109 |
| abstract_inverted_index.avalanche | 151, 157, 217 |
| abstract_inverted_index.confusion | 98 |
| abstract_inverted_index.diffusion | 100 |
| abstract_inverted_index.efficient | 15 |
| abstract_inverted_index.emergence | 1 |
| abstract_inverted_index.expansion | 8 |
| abstract_inverted_index.featuring | 211 |
| abstract_inverted_index.including | 147 |
| abstract_inverted_index.leverages | 117 |
| abstract_inverted_index.networks, | 4 |
| abstract_inverted_index.performed | 143 |
| abstract_inverted_index.security, | 210 |
| abstract_inverted_index.solutions | 17, 27 |
| abstract_inverted_index.symmetric | 84 |
| abstract_inverted_index.(DynBlock) | 63 |
| abstract_inverted_index.([Formula: | 163, 168 |
| abstract_inverted_index.algorithm. | 64 |
| abstract_inverted_index.efficiency | 233 |
| abstract_inverted_index.eliminates | 111 |
| abstract_inverted_index.encryption | 85 |
| abstract_inverted_index.operations | 122, 129 |
| abstract_inverted_index.plain-text | 156 |
| abstract_inverted_index.randomness | 254 |
| abstract_inverted_index.resistance | 200, 243 |
| abstract_inverted_index.throughput | 134, 235 |
| abstract_inverted_index.validation | 139 |
| abstract_inverted_index.vulnerable | 43 |
| abstract_inverted_index.Performance | 171 |
| abstract_inverted_index.challenges, | 54 |
| abstract_inverted_index.computation | 128 |
| abstract_inverted_index.considering | 144 |
| abstract_inverted_index.efficiency. | 137, 193 |
| abstract_inverted_index.lightweight | 59 |
| abstract_inverted_index.permutation | 92 |
| abstract_inverted_index.properties, | 101 |
| abstract_inverted_index.resilience, | 251 |
| abstract_inverted_index.well-suited | 221 |
| abstract_inverted_index.conventional | 112 |
| abstract_inverted_index.cryptography | 16, 26 |
| abstract_inverted_index.demonstrates | 242 |
| abstract_inverted_index.differential | 161 |
| abstract_inverted_index.necessitates | 12 |
| abstract_inverted_index.permutation, | 32 |
| abstract_inverted_index.side-channel | 49, 249 |
| abstract_inverted_index.specifically | 67 |
| abstract_inverted_index.substitution | 33, 94 |
| abstract_inverted_index.Additionally, | 88, 240 |
| abstract_inverted_index.computational | 192 |
| abstract_inverted_index.configuration | 197 |
| abstract_inverted_index.cryptanalysis | 47, 162, 167 |
| abstract_inverted_index.cryptanalytic | 202 |
| abstract_inverted_index.environments. | 224 |
| abstract_inverted_index.predecessors. | 239 |
| abstract_inverted_index.significantly | 230 |
| abstract_inverted_index.substitution- | 113 |
| abstract_inverted_index.communication. | 21 |
| abstract_inverted_index.computing-based | 46, 246 |
| abstract_inverted_index.resource-limited | 70 |
| abstract_inverted_index.state-of-the-art | 176 |
| abstract_inverted_index.permutation-boxes. | 115 |
| abstract_inverted_index.resource-constrained | 25, 223 |
| abstract_inverted_index.substitution-permutation | 106 |
| cited_by_percentile_year.max | 97 |
| cited_by_percentile_year.min | 95 |
| countries_distinct_count | 3 |
| institutions_distinct_count | 7 |
| citation_normalized_percentile.value | 0.94221859 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |