EdgeGuard: Machine Learning for Proactive Intrusion Detection on Edge Networks Article Swipe
 YOU?
·
· 2024
· Open Access
·
· DOI: https://doi.org/10.61356/j.aics.2024.1297
YOU?
·
· 2024
· Open Access
·
· DOI: https://doi.org/10.61356/j.aics.2024.1297
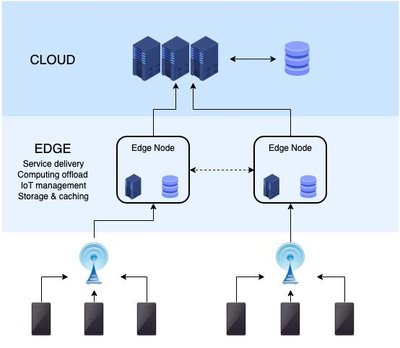
Edge computing has emerged as a promising paradigm to address the challenges of latency-sensitive applications and the exponential growth of Internet of Things (IoT) devices. However, the distributed nature of edge networks introduces new security vulnerabilities, necessitating robust intrusion detection mechanisms. In this paper, we propose EdgeGuard, a machine learning based framework for proactive intrusion detection on edge networks. Leveraging convolutional neural networks (CNNs) arranged in a residual fashion, EdgeGuard effectively captures complex patterns in network traffic data, enhancing the system's ability to detect intrusions with high accuracy. We conduct experiments using the Edge-IIoTset Cyber Security Dataset, containing a diverse range of normal and attack traffic samples. The proposed method achieves promising results, as evidenced by the receiver operating characteristic area under the curve (ROCAUC) and confusion matrix analysis. EdgeGuard offers a robust solution to safeguard edge computing environments against cyber threats, contributing to the security and integrity of IoT systems in real-world deployment scenarios.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.61356/j.aics.2024.1297
- OA Status
- hybrid
- Cited By
- 3
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4401725359
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4401725359Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.61356/j.aics.2024.1297Digital Object Identifier
- Title
-
EdgeGuard: Machine Learning for Proactive Intrusion Detection on Edge NetworksWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2024Year of publication
- Publication date
-
2024-06-14Full publication date if available
- Authors
-
Zakaria Ahmed, Sameh AskarList of authors in order
- Landing page
-
https://doi.org/10.61356/j.aics.2024.1297Publisher landing page
- Open access
-
YesWhether a free full text is available
- OA status
-
hybridOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.61356/j.aics.2024.1297Direct OA link when available
- Concepts
-
Computer science, Edge computing, Enhanced Data Rates for GSM Evolution, Intrusion detection system, Edge device, Software deployment, Computer security, Convolutional neural network, Confusion matrix, Distributed computing, Anomaly detection, Artificial intelligence, Cloud computing, Operating systemTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
3Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 2, 2024: 1Per-year citation counts (last 5 years)
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4401725359 |
|---|---|
| doi | https://doi.org/10.61356/j.aics.2024.1297 |
| ids.doi | https://doi.org/10.61356/j.aics.2024.1297 |
| ids.openalex | https://openalex.org/W4401725359 |
| fwci | 2.5105983 |
| type | article |
| title | EdgeGuard: Machine Learning for Proactive Intrusion Detection on Edge Networks |
| biblio.issue | |
| biblio.volume | 1 |
| biblio.last_page | 43 |
| biblio.first_page | 37 |
| topics[0].id | https://openalex.org/T10400 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9998000264167786 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1705 |
| topics[0].subfield.display_name | Computer Networks and Communications |
| topics[0].display_name | Network Security and Intrusion Detection |
| topics[1].id | https://openalex.org/T11512 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9947999715805054 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1702 |
| topics[1].subfield.display_name | Artificial Intelligence |
| topics[1].display_name | Anomaly Detection Techniques and Applications |
| topics[2].id | https://openalex.org/T11598 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9850000143051147 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1702 |
| topics[2].subfield.display_name | Artificial Intelligence |
| topics[2].display_name | Internet Traffic Analysis and Secure E-voting |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C41008148 |
| concepts[0].level | 0 |
| concepts[0].score | 0.806119441986084 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[0].display_name | Computer science |
| concepts[1].id | https://openalex.org/C2778456923 |
| concepts[1].level | 3 |
| concepts[1].score | 0.6727533936500549 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q5337692 |
| concepts[1].display_name | Edge computing |
| concepts[2].id | https://openalex.org/C162307627 |
| concepts[2].level | 2 |
| concepts[2].score | 0.6386050581932068 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q204833 |
| concepts[2].display_name | Enhanced Data Rates for GSM Evolution |
| concepts[3].id | https://openalex.org/C35525427 |
| concepts[3].level | 2 |
| concepts[3].score | 0.5903364419937134 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q745881 |
| concepts[3].display_name | Intrusion detection system |
| concepts[4].id | https://openalex.org/C138236772 |
| concepts[4].level | 3 |
| concepts[4].score | 0.5884270668029785 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q25098575 |
| concepts[4].display_name | Edge device |
| concepts[5].id | https://openalex.org/C105339364 |
| concepts[5].level | 2 |
| concepts[5].score | 0.4935194253921509 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q2297740 |
| concepts[5].display_name | Software deployment |
| concepts[6].id | https://openalex.org/C38652104 |
| concepts[6].level | 1 |
| concepts[6].score | 0.4779118001461029 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[6].display_name | Computer security |
| concepts[7].id | https://openalex.org/C81363708 |
| concepts[7].level | 2 |
| concepts[7].score | 0.47410470247268677 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q17084460 |
| concepts[7].display_name | Convolutional neural network |
| concepts[8].id | https://openalex.org/C138602881 |
| concepts[8].level | 2 |
| concepts[8].score | 0.4574354290962219 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q2709591 |
| concepts[8].display_name | Confusion matrix |
| concepts[9].id | https://openalex.org/C120314980 |
| concepts[9].level | 1 |
| concepts[9].score | 0.4524100124835968 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q180634 |
| concepts[9].display_name | Distributed computing |
| concepts[10].id | https://openalex.org/C739882 |
| concepts[10].level | 2 |
| concepts[10].score | 0.4293232858181 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q3560506 |
| concepts[10].display_name | Anomaly detection |
| concepts[11].id | https://openalex.org/C154945302 |
| concepts[11].level | 1 |
| concepts[11].score | 0.3364049196243286 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[11].display_name | Artificial intelligence |
| concepts[12].id | https://openalex.org/C79974875 |
| concepts[12].level | 2 |
| concepts[12].score | 0.16489973664283752 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q483639 |
| concepts[12].display_name | Cloud computing |
| concepts[13].id | https://openalex.org/C111919701 |
| concepts[13].level | 1 |
| concepts[13].score | 0.09551051259040833 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q9135 |
| concepts[13].display_name | Operating system |
| keywords[0].id | https://openalex.org/keywords/computer-science |
| keywords[0].score | 0.806119441986084 |
| keywords[0].display_name | Computer science |
| keywords[1].id | https://openalex.org/keywords/edge-computing |
| keywords[1].score | 0.6727533936500549 |
| keywords[1].display_name | Edge computing |
| keywords[2].id | https://openalex.org/keywords/enhanced-data-rates-for-gsm-evolution |
| keywords[2].score | 0.6386050581932068 |
| keywords[2].display_name | Enhanced Data Rates for GSM Evolution |
| keywords[3].id | https://openalex.org/keywords/intrusion-detection-system |
| keywords[3].score | 0.5903364419937134 |
| keywords[3].display_name | Intrusion detection system |
| keywords[4].id | https://openalex.org/keywords/edge-device |
| keywords[4].score | 0.5884270668029785 |
| keywords[4].display_name | Edge device |
| keywords[5].id | https://openalex.org/keywords/software-deployment |
| keywords[5].score | 0.4935194253921509 |
| keywords[5].display_name | Software deployment |
| keywords[6].id | https://openalex.org/keywords/computer-security |
| keywords[6].score | 0.4779118001461029 |
| keywords[6].display_name | Computer security |
| keywords[7].id | https://openalex.org/keywords/convolutional-neural-network |
| keywords[7].score | 0.47410470247268677 |
| keywords[7].display_name | Convolutional neural network |
| keywords[8].id | https://openalex.org/keywords/confusion-matrix |
| keywords[8].score | 0.4574354290962219 |
| keywords[8].display_name | Confusion matrix |
| keywords[9].id | https://openalex.org/keywords/distributed-computing |
| keywords[9].score | 0.4524100124835968 |
| keywords[9].display_name | Distributed computing |
| keywords[10].id | https://openalex.org/keywords/anomaly-detection |
| keywords[10].score | 0.4293232858181 |
| keywords[10].display_name | Anomaly detection |
| keywords[11].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[11].score | 0.3364049196243286 |
| keywords[11].display_name | Artificial intelligence |
| keywords[12].id | https://openalex.org/keywords/cloud-computing |
| keywords[12].score | 0.16489973664283752 |
| keywords[12].display_name | Cloud computing |
| keywords[13].id | https://openalex.org/keywords/operating-system |
| keywords[13].score | 0.09551051259040833 |
| keywords[13].display_name | Operating system |
| language | en |
| locations[0].id | doi:10.61356/j.aics.2024.1297 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4404663831 |
| locations[0].source.issn | 2998-8098, 2998-8101 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | False |
| locations[0].source.issn_l | 2998-8098 |
| locations[0].source.is_core | False |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | Artificial intelligence in cybersecurity. |
| locations[0].source.host_organization | |
| locations[0].source.host_organization_name | |
| locations[0].license | cc-by |
| locations[0].pdf_url | |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Artificial Intelligence in Cybersecurity |
| locations[0].landing_page_url | https://doi.org/10.61356/j.aics.2024.1297 |
| indexed_in | crossref |
| authorships[0].author.id | https://openalex.org/A5106622382 |
| authorships[0].author.orcid | |
| authorships[0].author.display_name | Zakaria Ahmed |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Zakaria Ahmed |
| authorships[0].is_corresponding | False |
| authorships[1].author.id | https://openalex.org/A5088545047 |
| authorships[1].author.orcid | https://orcid.org/0000-0002-1167-2430 |
| authorships[1].author.display_name | Sameh Askar |
| authorships[1].author_position | last |
| authorships[1].raw_author_name | Sameh S. Askar |
| authorships[1].is_corresponding | False |
| has_content.pdf | False |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.61356/j.aics.2024.1297 |
| open_access.oa_status | hybrid |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | EdgeGuard: Machine Learning for Proactive Intrusion Detection on Edge Networks |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10400 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9998000264167786 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1705 |
| primary_topic.subfield.display_name | Computer Networks and Communications |
| primary_topic.display_name | Network Security and Intrusion Detection |
| related_works | https://openalex.org/W4322761281, https://openalex.org/W4238233472, https://openalex.org/W4313526662, https://openalex.org/W3111395152, https://openalex.org/W4312996489, https://openalex.org/W3106131444, https://openalex.org/W3216099748, https://openalex.org/W4205963435, https://openalex.org/W4313463379, https://openalex.org/W3214037210 |
| cited_by_count | 3 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 2 |
| counts_by_year[1].year | 2024 |
| counts_by_year[1].cited_by_count | 1 |
| locations_count | 1 |
| best_oa_location.id | doi:10.61356/j.aics.2024.1297 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4404663831 |
| best_oa_location.source.issn | 2998-8098, 2998-8101 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | False |
| best_oa_location.source.issn_l | 2998-8098 |
| best_oa_location.source.is_core | False |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | Artificial intelligence in cybersecurity. |
| best_oa_location.source.host_organization | |
| best_oa_location.source.host_organization_name | |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Artificial Intelligence in Cybersecurity |
| best_oa_location.landing_page_url | https://doi.org/10.61356/j.aics.2024.1297 |
| primary_location.id | doi:10.61356/j.aics.2024.1297 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4404663831 |
| primary_location.source.issn | 2998-8098, 2998-8101 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | False |
| primary_location.source.issn_l | 2998-8098 |
| primary_location.source.is_core | False |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | Artificial intelligence in cybersecurity. |
| primary_location.source.host_organization | |
| primary_location.source.host_organization_name | |
| primary_location.license | cc-by |
| primary_location.pdf_url | |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Artificial Intelligence in Cybersecurity |
| primary_location.landing_page_url | https://doi.org/10.61356/j.aics.2024.1297 |
| publication_date | 2024-06-14 |
| publication_year | 2024 |
| referenced_works_count | 0 |
| abstract_inverted_index.a | 5, 47, 66, 98, 131 |
| abstract_inverted_index.In | 41 |
| abstract_inverted_index.We | 88 |
| abstract_inverted_index.as | 4, 113 |
| abstract_inverted_index.by | 115 |
| abstract_inverted_index.in | 65, 74, 151 |
| abstract_inverted_index.of | 12, 19, 21, 29, 101, 148 |
| abstract_inverted_index.on | 56 |
| abstract_inverted_index.to | 8, 82, 134, 143 |
| abstract_inverted_index.we | 44 |
| abstract_inverted_index.IoT | 149 |
| abstract_inverted_index.The | 107 |
| abstract_inverted_index.and | 15, 103, 125, 146 |
| abstract_inverted_index.for | 52 |
| abstract_inverted_index.has | 2 |
| abstract_inverted_index.new | 33 |
| abstract_inverted_index.the | 10, 16, 26, 79, 92, 116, 122, 144 |
| abstract_inverted_index.Edge | 0 |
| abstract_inverted_index.area | 120 |
| abstract_inverted_index.edge | 30, 57, 136 |
| abstract_inverted_index.high | 86 |
| abstract_inverted_index.this | 42 |
| abstract_inverted_index.with | 85 |
| abstract_inverted_index.(IoT) | 23 |
| abstract_inverted_index.Cyber | 94 |
| abstract_inverted_index.based | 50 |
| abstract_inverted_index.curve | 123 |
| abstract_inverted_index.cyber | 140 |
| abstract_inverted_index.data, | 77 |
| abstract_inverted_index.range | 100 |
| abstract_inverted_index.under | 121 |
| abstract_inverted_index.using | 91 |
| abstract_inverted_index.(CNNs) | 63 |
| abstract_inverted_index.Things | 22 |
| abstract_inverted_index.attack | 104 |
| abstract_inverted_index.detect | 83 |
| abstract_inverted_index.growth | 18 |
| abstract_inverted_index.matrix | 127 |
| abstract_inverted_index.method | 109 |
| abstract_inverted_index.nature | 28 |
| abstract_inverted_index.neural | 61 |
| abstract_inverted_index.normal | 102 |
| abstract_inverted_index.offers | 130 |
| abstract_inverted_index.paper, | 43 |
| abstract_inverted_index.robust | 37, 132 |
| abstract_inverted_index.ability | 81 |
| abstract_inverted_index.address | 9 |
| abstract_inverted_index.against | 139 |
| abstract_inverted_index.complex | 72 |
| abstract_inverted_index.conduct | 89 |
| abstract_inverted_index.diverse | 99 |
| abstract_inverted_index.emerged | 3 |
| abstract_inverted_index.machine | 48 |
| abstract_inverted_index.network | 75 |
| abstract_inverted_index.propose | 45 |
| abstract_inverted_index.systems | 150 |
| abstract_inverted_index.traffic | 76, 105 |
| abstract_inverted_index.(ROCAUC) | 124 |
| abstract_inverted_index.Dataset, | 96 |
| abstract_inverted_index.However, | 25 |
| abstract_inverted_index.Internet | 20 |
| abstract_inverted_index.Security | 95 |
| abstract_inverted_index.achieves | 110 |
| abstract_inverted_index.arranged | 64 |
| abstract_inverted_index.captures | 71 |
| abstract_inverted_index.devices. | 24 |
| abstract_inverted_index.fashion, | 68 |
| abstract_inverted_index.learning | 49 |
| abstract_inverted_index.networks | 31, 62 |
| abstract_inverted_index.paradigm | 7 |
| abstract_inverted_index.patterns | 73 |
| abstract_inverted_index.proposed | 108 |
| abstract_inverted_index.receiver | 117 |
| abstract_inverted_index.residual | 67 |
| abstract_inverted_index.results, | 112 |
| abstract_inverted_index.samples. | 106 |
| abstract_inverted_index.security | 34, 145 |
| abstract_inverted_index.solution | 133 |
| abstract_inverted_index.system's | 80 |
| abstract_inverted_index.threats, | 141 |
| abstract_inverted_index.EdgeGuard | 69, 129 |
| abstract_inverted_index.accuracy. | 87 |
| abstract_inverted_index.analysis. | 128 |
| abstract_inverted_index.computing | 1, 137 |
| abstract_inverted_index.confusion | 126 |
| abstract_inverted_index.detection | 39, 55 |
| abstract_inverted_index.enhancing | 78 |
| abstract_inverted_index.evidenced | 114 |
| abstract_inverted_index.framework | 51 |
| abstract_inverted_index.integrity | 147 |
| abstract_inverted_index.intrusion | 38, 54 |
| abstract_inverted_index.networks. | 58 |
| abstract_inverted_index.operating | 118 |
| abstract_inverted_index.proactive | 53 |
| abstract_inverted_index.promising | 6, 111 |
| abstract_inverted_index.safeguard | 135 |
| abstract_inverted_index.EdgeGuard, | 46 |
| abstract_inverted_index.Leveraging | 59 |
| abstract_inverted_index.challenges | 11 |
| abstract_inverted_index.containing | 97 |
| abstract_inverted_index.deployment | 153 |
| abstract_inverted_index.introduces | 32 |
| abstract_inverted_index.intrusions | 84 |
| abstract_inverted_index.real-world | 152 |
| abstract_inverted_index.scenarios. | 154 |
| abstract_inverted_index.distributed | 27 |
| abstract_inverted_index.effectively | 70 |
| abstract_inverted_index.experiments | 90 |
| abstract_inverted_index.exponential | 17 |
| abstract_inverted_index.mechanisms. | 40 |
| abstract_inverted_index.Edge-IIoTset | 93 |
| abstract_inverted_index.applications | 14 |
| abstract_inverted_index.contributing | 142 |
| abstract_inverted_index.environments | 138 |
| abstract_inverted_index.convolutional | 60 |
| abstract_inverted_index.necessitating | 36 |
| abstract_inverted_index.characteristic | 119 |
| abstract_inverted_index.vulnerabilities, | 35 |
| abstract_inverted_index.latency-sensitive | 13 |
| cited_by_percentile_year.max | 97 |
| cited_by_percentile_year.min | 90 |
| countries_distinct_count | 0 |
| institutions_distinct_count | 2 |
| citation_normalized_percentile.value | 0.83271583 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |