Encryption Algorithm for TCP Session Hijacking Article Swipe
Related Concepts
Computer science
Computer network
Zeta-TCP
Encryption
TCP global synchronization
TCP Friendly Rate Control
TCP tuning
TCP acceleration
Cryptography
Algorithm
Computer security
Transmission Control Protocol
Network packet
Minghan Chen
,
Fangyan Dai
,
Bingjie Yan
,
Jieren Cheng
,
Longjuan Wang
·
 YOU?
·
· 2020
· Open Access
·
· DOI: https://doi.org/10.48550/arxiv.2002.01391
· OA: W3005255627
YOU?
·
· 2020
· Open Access
·
· DOI: https://doi.org/10.48550/arxiv.2002.01391
· OA: W3005255627
 YOU?
·
· 2020
· Open Access
·
· DOI: https://doi.org/10.48550/arxiv.2002.01391
· OA: W3005255627
YOU?
·
· 2020
· Open Access
·
· DOI: https://doi.org/10.48550/arxiv.2002.01391
· OA: W3005255627
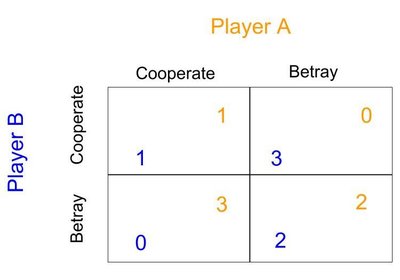
Distributed network of the computer and the design defects of the TCP protocol are given to the network attack to be multiplicative. Based on the simple and open assumptions of the TCP protocol in academic and collaborative communication environments, the protocol lacks secure authentication. In this paper, by adding RSA-based cryptography technology, RSA-based signature technology, DH key exchange algorithm, and HAMC-SHA1 integrity verification technology to the TCP protocol, and propose a security strategy which can effectively defend against TCP session hijacking.
Related Topics
Finding more related topics…