Enhancing Intrusion Detection and Mitigation in Ad Hoc Networks Using an AI-Driven Deep Learning Approach Article Swipe
 YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.5755/j02.eie.40003
YOU?
·
· 2025
· Open Access
·
· DOI: https://doi.org/10.5755/j02.eie.40003
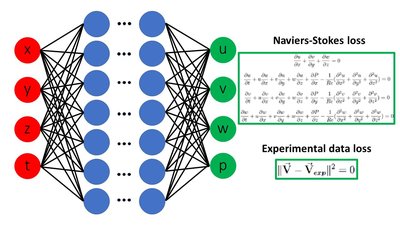
Ad hoc networks are increasingly deployed in critical applications due to their flexibility and scalability. However, their decentralised and dynamic nature makes them highly vulnerable to a range of sophisticated security threats. This paper aims to improve the efficiency of intrusion detection and mitigation in ad hoc networks using an AI-driven deep learning approach. A hybrid deep learning model is proposed, integrating convolutional neural networks (CNNs) for feature extraction and long short-term memory networks (LSTMs) for temporal analysis to effectively detect malicious activities. Reinforcement learning, particularly using a deep Q-network (DQN), is applied to dynamically select optimal mitigation strategies. Federated learning is also used to train the model in a distributed manner, ensuring privacy while allowing scalability across network nodes. The proposed approach shows significant improvements in intrusion detection accuracy, exceeding 90 %, and offers effective real-time mitigation strategies. These results provide a comprehensive and adaptive framework for securing ad hoc networks against evolving threats.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.5755/j02.eie.40003
- https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135
- OA Status
- gold
- OpenAlex ID
- https://openalex.org/W4415052806
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4415052806Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.5755/j02.eie.40003Digital Object Identifier
- Title
-
Enhancing Intrusion Detection and Mitigation in Ad Hoc Networks Using an AI-Driven Deep Learning ApproachWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2025Year of publication
- Publication date
-
2025-06-27Full publication date if available
- Authors
-
Mohamed Abbas, Mohammed I. Al‐RayifList of authors in order
- Landing page
-
https://doi.org/10.5755/j02.eie.40003Publisher landing page
- PDF URL
-
https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135Direct link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
goldOpen access status per OpenAlex
- OA URL
-
https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135Direct OA link when available
- Cited by
-
0Total citation count in OpenAlex
Full payload
| id | https://openalex.org/W4415052806 |
|---|---|
| doi | https://doi.org/10.5755/j02.eie.40003 |
| ids.doi | https://doi.org/10.5755/j02.eie.40003 |
| ids.openalex | https://openalex.org/W4415052806 |
| fwci | 0.0 |
| type | article |
| title | Enhancing Intrusion Detection and Mitigation in Ad Hoc Networks Using an AI-Driven Deep Learning Approach |
| biblio.issue | 3 |
| biblio.volume | 31 |
| biblio.last_page | 67 |
| biblio.first_page | 56 |
| topics[0].id | https://openalex.org/T10400 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9922999739646912 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1705 |
| topics[0].subfield.display_name | Computer Networks and Communications |
| topics[0].display_name | Network Security and Intrusion Detection |
| topics[1].id | https://openalex.org/T10246 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9682999849319458 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1705 |
| topics[1].subfield.display_name | Computer Networks and Communications |
| topics[1].display_name | Mobile Ad Hoc Networks |
| topics[2].id | https://openalex.org/T10917 |
| topics[2].field.id | https://openalex.org/fields/22 |
| topics[2].field.display_name | Engineering |
| topics[2].score | 0.9053000211715698 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/2207 |
| topics[2].subfield.display_name | Control and Systems Engineering |
| topics[2].display_name | Smart Grid Security and Resilience |
| is_xpac | False |
| apc_list.value | 70 |
| apc_list.currency | EUR |
| apc_list.value_usd | 75 |
| apc_paid.value | 70 |
| apc_paid.currency | EUR |
| apc_paid.value_usd | 75 |
| language | en |
| locations[0].id | doi:10.5755/j02.eie.40003 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S30479993 |
| locations[0].source.issn | 1392-1215, 2029-5731 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 1392-1215 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | Elektronika ir Elektrotechnika |
| locations[0].source.host_organization | https://openalex.org/P4310317509 |
| locations[0].source.host_organization_name | Kaunas University of Technology |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310317509 |
| locations[0].source.host_organization_lineage_names | Kaunas University of Technology |
| locations[0].license | cc-by |
| locations[0].pdf_url | https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135 |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Elektronika ir Elektrotechnika |
| locations[0].landing_page_url | https://doi.org/10.5755/j02.eie.40003 |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5100645455 |
| authorships[0].author.orcid | https://orcid.org/0000-0002-3141-2900 |
| authorships[0].author.display_name | Mohamed Abbas |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Mohamed Abbas |
| authorships[0].is_corresponding | False |
| authorships[1].author.id | https://openalex.org/A5064473941 |
| authorships[1].author.orcid | https://orcid.org/0000-0003-0437-5523 |
| authorships[1].author.display_name | Mohammed I. Al‐Rayif |
| authorships[1].author_position | last |
| authorships[1].raw_author_name | Mohammed I. Al-Rayif |
| authorships[1].is_corresponding | False |
| has_content.pdf | True |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135 |
| open_access.oa_status | gold |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-11T00:00:00 |
| display_name | Enhancing Intrusion Detection and Mitigation in Ad Hoc Networks Using an AI-Driven Deep Learning Approach |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10400 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9922999739646912 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1705 |
| primary_topic.subfield.display_name | Computer Networks and Communications |
| primary_topic.display_name | Network Security and Intrusion Detection |
| cited_by_count | 0 |
| locations_count | 1 |
| best_oa_location.id | doi:10.5755/j02.eie.40003 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S30479993 |
| best_oa_location.source.issn | 1392-1215, 2029-5731 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 1392-1215 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | Elektronika ir Elektrotechnika |
| best_oa_location.source.host_organization | https://openalex.org/P4310317509 |
| best_oa_location.source.host_organization_name | Kaunas University of Technology |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310317509 |
| best_oa_location.source.host_organization_lineage_names | Kaunas University of Technology |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135 |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Elektronika ir Elektrotechnika |
| best_oa_location.landing_page_url | https://doi.org/10.5755/j02.eie.40003 |
| primary_location.id | doi:10.5755/j02.eie.40003 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S30479993 |
| primary_location.source.issn | 1392-1215, 2029-5731 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 1392-1215 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | Elektronika ir Elektrotechnika |
| primary_location.source.host_organization | https://openalex.org/P4310317509 |
| primary_location.source.host_organization_name | Kaunas University of Technology |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310317509 |
| primary_location.source.host_organization_lineage_names | Kaunas University of Technology |
| primary_location.license | cc-by |
| primary_location.pdf_url | https://eejournal.ktu.lt/index.php/elt/article/download/40003/17135 |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Elektronika ir Elektrotechnika |
| primary_location.landing_page_url | https://doi.org/10.5755/j02.eie.40003 |
| publication_date | 2025-06-27 |
| publication_year | 2025 |
| referenced_works_count | 0 |
| abstract_inverted_index.A | 54 |
| abstract_inverted_index.a | 26, 87, 109, 142 |
| abstract_inverted_index.%, | 132 |
| abstract_inverted_index.90 | 131 |
| abstract_inverted_index.Ad | 0 |
| abstract_inverted_index.ad | 45, 149 |
| abstract_inverted_index.an | 49 |
| abstract_inverted_index.in | 6, 44, 108, 126 |
| abstract_inverted_index.is | 59, 91, 101 |
| abstract_inverted_index.of | 28, 39 |
| abstract_inverted_index.to | 10, 25, 35, 78, 93, 104 |
| abstract_inverted_index.The | 120 |
| abstract_inverted_index.and | 13, 18, 42, 69, 133, 144 |
| abstract_inverted_index.are | 3 |
| abstract_inverted_index.due | 9 |
| abstract_inverted_index.for | 66, 75, 147 |
| abstract_inverted_index.hoc | 1, 46, 150 |
| abstract_inverted_index.the | 37, 106 |
| abstract_inverted_index.This | 32 |
| abstract_inverted_index.aims | 34 |
| abstract_inverted_index.also | 102 |
| abstract_inverted_index.deep | 51, 56, 88 |
| abstract_inverted_index.long | 70 |
| abstract_inverted_index.them | 22 |
| abstract_inverted_index.used | 103 |
| abstract_inverted_index.These | 139 |
| abstract_inverted_index.makes | 21 |
| abstract_inverted_index.model | 58, 107 |
| abstract_inverted_index.paper | 33 |
| abstract_inverted_index.range | 27 |
| abstract_inverted_index.shows | 123 |
| abstract_inverted_index.their | 11, 16 |
| abstract_inverted_index.train | 105 |
| abstract_inverted_index.using | 48, 86 |
| abstract_inverted_index.while | 114 |
| abstract_inverted_index.(CNNs) | 65 |
| abstract_inverted_index.(DQN), | 90 |
| abstract_inverted_index.across | 117 |
| abstract_inverted_index.detect | 80 |
| abstract_inverted_index.highly | 23 |
| abstract_inverted_index.hybrid | 55 |
| abstract_inverted_index.memory | 72 |
| abstract_inverted_index.nature | 20 |
| abstract_inverted_index.neural | 63 |
| abstract_inverted_index.nodes. | 119 |
| abstract_inverted_index.offers | 134 |
| abstract_inverted_index.select | 95 |
| abstract_inverted_index.(LSTMs) | 74 |
| abstract_inverted_index.against | 152 |
| abstract_inverted_index.applied | 92 |
| abstract_inverted_index.dynamic | 19 |
| abstract_inverted_index.feature | 67 |
| abstract_inverted_index.improve | 36 |
| abstract_inverted_index.manner, | 111 |
| abstract_inverted_index.network | 118 |
| abstract_inverted_index.optimal | 96 |
| abstract_inverted_index.privacy | 113 |
| abstract_inverted_index.provide | 141 |
| abstract_inverted_index.results | 140 |
| abstract_inverted_index.However, | 15 |
| abstract_inverted_index.adaptive | 145 |
| abstract_inverted_index.allowing | 115 |
| abstract_inverted_index.analysis | 77 |
| abstract_inverted_index.approach | 122 |
| abstract_inverted_index.critical | 7 |
| abstract_inverted_index.deployed | 5 |
| abstract_inverted_index.ensuring | 112 |
| abstract_inverted_index.evolving | 153 |
| abstract_inverted_index.learning | 52, 57, 100 |
| abstract_inverted_index.networks | 2, 47, 64, 73, 151 |
| abstract_inverted_index.proposed | 121 |
| abstract_inverted_index.securing | 148 |
| abstract_inverted_index.security | 30 |
| abstract_inverted_index.temporal | 76 |
| abstract_inverted_index.threats. | 31, 154 |
| abstract_inverted_index.AI-driven | 50 |
| abstract_inverted_index.Federated | 99 |
| abstract_inverted_index.Q-network | 89 |
| abstract_inverted_index.accuracy, | 129 |
| abstract_inverted_index.approach. | 53 |
| abstract_inverted_index.detection | 41, 128 |
| abstract_inverted_index.effective | 135 |
| abstract_inverted_index.exceeding | 130 |
| abstract_inverted_index.framework | 146 |
| abstract_inverted_index.intrusion | 40, 127 |
| abstract_inverted_index.learning, | 84 |
| abstract_inverted_index.malicious | 81 |
| abstract_inverted_index.proposed, | 60 |
| abstract_inverted_index.real-time | 136 |
| abstract_inverted_index.efficiency | 38 |
| abstract_inverted_index.extraction | 68 |
| abstract_inverted_index.mitigation | 43, 97, 137 |
| abstract_inverted_index.short-term | 71 |
| abstract_inverted_index.vulnerable | 24 |
| abstract_inverted_index.activities. | 82 |
| abstract_inverted_index.distributed | 110 |
| abstract_inverted_index.dynamically | 94 |
| abstract_inverted_index.effectively | 79 |
| abstract_inverted_index.flexibility | 12 |
| abstract_inverted_index.integrating | 61 |
| abstract_inverted_index.scalability | 116 |
| abstract_inverted_index.significant | 124 |
| abstract_inverted_index.strategies. | 98, 138 |
| abstract_inverted_index.applications | 8 |
| abstract_inverted_index.improvements | 125 |
| abstract_inverted_index.increasingly | 4 |
| abstract_inverted_index.particularly | 85 |
| abstract_inverted_index.scalability. | 14 |
| abstract_inverted_index.Reinforcement | 83 |
| abstract_inverted_index.comprehensive | 143 |
| abstract_inverted_index.convolutional | 62 |
| abstract_inverted_index.decentralised | 17 |
| abstract_inverted_index.sophisticated | 29 |
| cited_by_percentile_year | |
| countries_distinct_count | 0 |
| institutions_distinct_count | 2 |
| citation_normalized_percentile.value | 0.57854158 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |