Explainable artificial intelligence in web phishing classification on secure IoT with cloud-based cyber-physical systems Article Swipe
 YOU?
·
· 2024
· Open Access
·
· DOI: https://doi.org/10.1016/j.aej.2024.09.115
YOU?
·
· 2024
· Open Access
·
· DOI: https://doi.org/10.1016/j.aej.2024.09.115
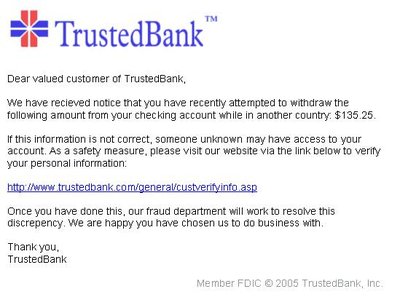
IoT is the technology that aids the interconnection of all kinds of devices over the internet to replace data, monitor devices and enhance actuators to create outcomes. Cyber-physical systems (CPS) contain control and computation components, which are compactly assured with physical procedures. The internet plays a prominent role in modern lives, and the cybersecurity challenge caused by phishing attacks is significant. This research presents a novel approach to address this problem using machine learning (ML) methods for phishing website classification. Leveraging feature extraction and innovative algorithms, the projected method aims to distinguish between malicious and legitimate websites by features of phishing attempts and analyzing inherent patterns. Phishing is a significant threat that causes extensive financial losses for internet users yearly. This fraudulent act includes identity hackers utilizing clever approaches to deceive individuals into revealing sensitive data. Generally, phishers use strategies such as advanced phishing software and fake emails to illegally acquire confidential details like usernames and passwords from financial accounts. This article develops an Explainable Artificial Intelligence with Aquila Optimization Algorithm in Web Phishing Classification (XAIAOA-WPC) approach on secure Cyber-Physical Systems. The developed XAIAOA-WPC approach mainly emphasizes the effectual classification and recognition of web phishing based on CPS. In the first phase, preprocessing is carried out on three levels: data cleaning, text preprocessing, and standardization. Furthermore, the Harris' Hawks optimization-based feature selection (HHO-FS) method is applied to derive feature subsets. The XAIAOA-WPC method utilizes a multi-head attention-based long short-term memory (MHA-LSTM) model for web phishing recognition. Besides, the detection outcomes of the MHA-LSTM approach are enhanced by using the Aquila optimization algorithm (AOA) model. At last, the XAIAOA-WPC method incorporates the XAI model LIME for superior perception and explainability of the black-box process for precise identification of intrusions. The simulation outcome of the XAIAOA-WPC method is examined on a benchmark database. The experimental validation of the XAIAOA-WPC method exhibited a superior accuracy value of 99.29 % over existing techniques.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.1016/j.aej.2024.09.115
- OA Status
- gold
- Cited By
- 12
- References
- 39
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4403426933
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4403426933Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1016/j.aej.2024.09.115Digital Object Identifier
- Title
-
Explainable artificial intelligence in web phishing classification on secure IoT with cloud-based cyber-physical systemsWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2024Year of publication
- Publication date
-
2024-10-15Full publication date if available
- Authors
-
Sultan Alotaibi, Hend Khalid Alkahtani, Mohammed Aljebreen, Asma Alshuhail, Muhammad Kashif Saeed, Shouki A. Ebad, Wafa Almukadi, Moneerah AlotaibiList of authors in order
- Landing page
-
https://doi.org/10.1016/j.aej.2024.09.115Publisher landing page
- Open access
-
YesWhether a free full text is available
- OA status
-
goldOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.1016/j.aej.2024.09.115Direct OA link when available
- Concepts
-
Internet of Things, Cyber-physical system, Cloud computing, Phishing, Computer science, Computer security, World Wide Web, The Internet, Operating systemTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
12Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 12Per-year citation counts (last 5 years)
- References (count)
-
39Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4403426933 |
|---|---|
| doi | https://doi.org/10.1016/j.aej.2024.09.115 |
| ids.doi | https://doi.org/10.1016/j.aej.2024.09.115 |
| ids.openalex | https://openalex.org/W4403426933 |
| fwci | 18.33180316 |
| type | article |
| title | Explainable artificial intelligence in web phishing classification on secure IoT with cloud-based cyber-physical systems |
| biblio.issue | |
| biblio.volume | 110 |
| biblio.last_page | 505 |
| biblio.first_page | 490 |
| topics[0].id | https://openalex.org/T10270 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9951000213623047 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1710 |
| topics[0].subfield.display_name | Information Systems |
| topics[0].display_name | Blockchain Technology Applications and Security |
| topics[1].id | https://openalex.org/T11644 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9922999739646912 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1710 |
| topics[1].subfield.display_name | Information Systems |
| topics[1].display_name | Spam and Phishing Detection |
| topics[2].id | https://openalex.org/T10400 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9898999929428101 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1705 |
| topics[2].subfield.display_name | Computer Networks and Communications |
| topics[2].display_name | Network Security and Intrusion Detection |
| funders[0].id | https://openalex.org/F4320321145 |
| funders[0].ror | https://ror.org/02f81g417 |
| funders[0].display_name | King Saud University |
| funders[1].id | https://openalex.org/F4320322484 |
| funders[1].ror | https://ror.org/05b0cyh02 |
| funders[1].display_name | Princess Nourah Bint Abdulrahman University |
| is_xpac | False |
| apc_list.value | 860 |
| apc_list.currency | USD |
| apc_list.value_usd | 860 |
| apc_paid.value | 860 |
| apc_paid.currency | USD |
| apc_paid.value_usd | 860 |
| concepts[0].id | https://openalex.org/C81860439 |
| concepts[0].level | 2 |
| concepts[0].score | 0.7487186789512634 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q251212 |
| concepts[0].display_name | Internet of Things |
| concepts[1].id | https://openalex.org/C179768478 |
| concepts[1].level | 2 |
| concepts[1].score | 0.7197729349136353 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q1120057 |
| concepts[1].display_name | Cyber-physical system |
| concepts[2].id | https://openalex.org/C79974875 |
| concepts[2].level | 2 |
| concepts[2].score | 0.6943360567092896 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q483639 |
| concepts[2].display_name | Cloud computing |
| concepts[3].id | https://openalex.org/C83860907 |
| concepts[3].level | 3 |
| concepts[3].score | 0.6544331312179565 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q135005 |
| concepts[3].display_name | Phishing |
| concepts[4].id | https://openalex.org/C41008148 |
| concepts[4].level | 0 |
| concepts[4].score | 0.568784236907959 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[4].display_name | Computer science |
| concepts[5].id | https://openalex.org/C38652104 |
| concepts[5].level | 1 |
| concepts[5].score | 0.5331690907478333 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[5].display_name | Computer security |
| concepts[6].id | https://openalex.org/C136764020 |
| concepts[6].level | 1 |
| concepts[6].score | 0.3698919415473938 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q466 |
| concepts[6].display_name | World Wide Web |
| concepts[7].id | https://openalex.org/C110875604 |
| concepts[7].level | 2 |
| concepts[7].score | 0.2543611526489258 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q75 |
| concepts[7].display_name | The Internet |
| concepts[8].id | https://openalex.org/C111919701 |
| concepts[8].level | 1 |
| concepts[8].score | 0.06998735666275024 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q9135 |
| concepts[8].display_name | Operating system |
| keywords[0].id | https://openalex.org/keywords/internet-of-things |
| keywords[0].score | 0.7487186789512634 |
| keywords[0].display_name | Internet of Things |
| keywords[1].id | https://openalex.org/keywords/cyber-physical-system |
| keywords[1].score | 0.7197729349136353 |
| keywords[1].display_name | Cyber-physical system |
| keywords[2].id | https://openalex.org/keywords/cloud-computing |
| keywords[2].score | 0.6943360567092896 |
| keywords[2].display_name | Cloud computing |
| keywords[3].id | https://openalex.org/keywords/phishing |
| keywords[3].score | 0.6544331312179565 |
| keywords[3].display_name | Phishing |
| keywords[4].id | https://openalex.org/keywords/computer-science |
| keywords[4].score | 0.568784236907959 |
| keywords[4].display_name | Computer science |
| keywords[5].id | https://openalex.org/keywords/computer-security |
| keywords[5].score | 0.5331690907478333 |
| keywords[5].display_name | Computer security |
| keywords[6].id | https://openalex.org/keywords/world-wide-web |
| keywords[6].score | 0.3698919415473938 |
| keywords[6].display_name | World Wide Web |
| keywords[7].id | https://openalex.org/keywords/the-internet |
| keywords[7].score | 0.2543611526489258 |
| keywords[7].display_name | The Internet |
| keywords[8].id | https://openalex.org/keywords/operating-system |
| keywords[8].score | 0.06998735666275024 |
| keywords[8].display_name | Operating system |
| language | en |
| locations[0].id | doi:10.1016/j.aej.2024.09.115 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S2764413287 |
| locations[0].source.issn | 1110-0168, 2090-2670 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 1110-0168 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | Alexandria Engineering Journal |
| locations[0].source.host_organization | https://openalex.org/P4310320990 |
| locations[0].source.host_organization_name | Elsevier BV |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310320990 |
| locations[0].source.host_organization_lineage_names | Elsevier BV |
| locations[0].license | |
| locations[0].pdf_url | |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Alexandria Engineering Journal |
| locations[0].landing_page_url | https://doi.org/10.1016/j.aej.2024.09.115 |
| locations[1].id | pmh:oai:doaj.org/article:b513f55e163a4ee1971ff215181b4452 |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306401280 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[1].source.host_organization | |
| locations[1].source.host_organization_name | |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | submittedVersion |
| locations[1].raw_type | article |
| locations[1].license_id | |
| locations[1].is_accepted | False |
| locations[1].is_published | False |
| locations[1].raw_source_name | Alexandria Engineering Journal, Vol 110, Iss , Pp 490-505 (2025) |
| locations[1].landing_page_url | https://doaj.org/article/b513f55e163a4ee1971ff215181b4452 |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5088482440 |
| authorships[0].author.orcid | https://orcid.org/0000-0002-9165-3036 |
| authorships[0].author.display_name | Sultan Alotaibi |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Sultan Refa Alotaibi |
| authorships[0].is_corresponding | False |
| authorships[1].author.id | https://openalex.org/A5058485751 |
| authorships[1].author.orcid | https://orcid.org/0000-0001-7507-5267 |
| authorships[1].author.display_name | Hend Khalid Alkahtani |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Hend Khalid Alkahtani |
| authorships[1].is_corresponding | False |
| authorships[2].author.id | https://openalex.org/A5025820678 |
| authorships[2].author.orcid | https://orcid.org/0000-0002-6295-733X |
| authorships[2].author.display_name | Mohammed Aljebreen |
| authorships[2].author_position | middle |
| authorships[2].raw_author_name | Mohammed Aljebreen |
| authorships[2].is_corresponding | False |
| authorships[3].author.id | https://openalex.org/A5056520942 |
| authorships[3].author.orcid | https://orcid.org/0000-0002-4110-9657 |
| authorships[3].author.display_name | Asma Alshuhail |
| authorships[3].author_position | middle |
| authorships[3].raw_author_name | Asma Alshuhail |
| authorships[3].is_corresponding | False |
| authorships[4].author.id | https://openalex.org/A5040314610 |
| authorships[4].author.orcid | https://orcid.org/0000-0002-9300-2157 |
| authorships[4].author.display_name | Muhammad Kashif Saeed |
| authorships[4].author_position | middle |
| authorships[4].raw_author_name | Muhammad Kashif Saeed |
| authorships[4].is_corresponding | False |
| authorships[5].author.id | https://openalex.org/A5031341129 |
| authorships[5].author.orcid | https://orcid.org/0000-0003-1043-2774 |
| authorships[5].author.display_name | Shouki A. Ebad |
| authorships[5].author_position | middle |
| authorships[5].raw_author_name | Shouki A. Ebad |
| authorships[5].is_corresponding | False |
| authorships[6].author.id | https://openalex.org/A5065270510 |
| authorships[6].author.orcid | https://orcid.org/0000-0003-3980-0710 |
| authorships[6].author.display_name | Wafa Almukadi |
| authorships[6].author_position | middle |
| authorships[6].raw_author_name | Wafa Sulaiman Almukadi |
| authorships[6].is_corresponding | False |
| authorships[7].author.id | https://openalex.org/A5071479102 |
| authorships[7].author.orcid | https://orcid.org/0000-0002-0074-8153 |
| authorships[7].author.display_name | Moneerah Alotaibi |
| authorships[7].author_position | last |
| authorships[7].raw_author_name | Moneerah Alotaibi |
| authorships[7].is_corresponding | False |
| has_content.pdf | False |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.1016/j.aej.2024.09.115 |
| open_access.oa_status | gold |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Explainable artificial intelligence in web phishing classification on secure IoT with cloud-based cyber-physical systems |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10270 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9951000213623047 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1710 |
| primary_topic.subfield.display_name | Information Systems |
| primary_topic.display_name | Blockchain Technology Applications and Security |
| related_works | https://openalex.org/W2149202530, https://openalex.org/W2807822918, https://openalex.org/W2921723332, https://openalex.org/W2482950156, https://openalex.org/W4396966040, https://openalex.org/W2305322260, https://openalex.org/W3139248031, https://openalex.org/W3042334625, https://openalex.org/W4200017362, https://openalex.org/W4388020458 |
| cited_by_count | 12 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 12 |
| locations_count | 2 |
| best_oa_location.id | doi:10.1016/j.aej.2024.09.115 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S2764413287 |
| best_oa_location.source.issn | 1110-0168, 2090-2670 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 1110-0168 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | Alexandria Engineering Journal |
| best_oa_location.source.host_organization | https://openalex.org/P4310320990 |
| best_oa_location.source.host_organization_name | Elsevier BV |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310320990 |
| best_oa_location.source.host_organization_lineage_names | Elsevier BV |
| best_oa_location.license | |
| best_oa_location.pdf_url | |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Alexandria Engineering Journal |
| best_oa_location.landing_page_url | https://doi.org/10.1016/j.aej.2024.09.115 |
| primary_location.id | doi:10.1016/j.aej.2024.09.115 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S2764413287 |
| primary_location.source.issn | 1110-0168, 2090-2670 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 1110-0168 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | Alexandria Engineering Journal |
| primary_location.source.host_organization | https://openalex.org/P4310320990 |
| primary_location.source.host_organization_name | Elsevier BV |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310320990 |
| primary_location.source.host_organization_lineage_names | Elsevier BV |
| primary_location.license | |
| primary_location.pdf_url | |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Alexandria Engineering Journal |
| primary_location.landing_page_url | https://doi.org/10.1016/j.aej.2024.09.115 |
| publication_date | 2024-10-15 |
| publication_year | 2024 |
| referenced_works | https://openalex.org/W4213081600, https://openalex.org/W6794192134, https://openalex.org/W3134340954, https://openalex.org/W3199502129, https://openalex.org/W3029404970, https://openalex.org/W6801301350, https://openalex.org/W6784990468, https://openalex.org/W2736809319, https://openalex.org/W6788330746, https://openalex.org/W3184796286, https://openalex.org/W6862709095, https://openalex.org/W4382278693, https://openalex.org/W4292387506, https://openalex.org/W4353046955, https://openalex.org/W4324057055, https://openalex.org/W4396930243, https://openalex.org/W4309756669, https://openalex.org/W4399906580, https://openalex.org/W6774808126, https://openalex.org/W4320917975, https://openalex.org/W4320919468, https://openalex.org/W4391947465, https://openalex.org/W4387007813, https://openalex.org/W4390670372, https://openalex.org/W6852370126, https://openalex.org/W4400749015, https://openalex.org/W4399370694, https://openalex.org/W4393875137, https://openalex.org/W4400351652, https://openalex.org/W4400405742, https://openalex.org/W4391986380, https://openalex.org/W4280569680, https://openalex.org/W4313588323, https://openalex.org/W4400459041, https://openalex.org/W4392988374, https://openalex.org/W4244615858, https://openalex.org/W3098409150, https://openalex.org/W4392052394, https://openalex.org/W4255466807 |
| referenced_works_count | 39 |
| abstract_inverted_index.% | 315 |
| abstract_inverted_index.a | 45, 64, 108, 234, 298, 309 |
| abstract_inverted_index.At | 264 |
| abstract_inverted_index.In | 198 |
| abstract_inverted_index.an | 163 |
| abstract_inverted_index.as | 141 |
| abstract_inverted_index.by | 56, 97, 256 |
| abstract_inverted_index.in | 48, 171 |
| abstract_inverted_index.is | 1, 59, 107, 203, 224, 295 |
| abstract_inverted_index.of | 8, 11, 99, 192, 250, 279, 286, 291, 304, 313 |
| abstract_inverted_index.on | 177, 196, 206, 297 |
| abstract_inverted_index.to | 16, 24, 67, 90, 129, 148, 226 |
| abstract_inverted_index.IoT | 0 |
| abstract_inverted_index.The | 42, 181, 230, 288, 301 |
| abstract_inverted_index.Web | 172 |
| abstract_inverted_index.XAI | 271 |
| abstract_inverted_index.act | 122 |
| abstract_inverted_index.all | 9 |
| abstract_inverted_index.and | 21, 32, 51, 83, 94, 102, 145, 155, 190, 213, 277 |
| abstract_inverted_index.are | 36, 254 |
| abstract_inverted_index.for | 76, 116, 242, 274, 283 |
| abstract_inverted_index.out | 205 |
| abstract_inverted_index.the | 2, 6, 14, 52, 86, 187, 199, 216, 247, 251, 258, 266, 270, 280, 292, 305 |
| abstract_inverted_index.use | 138 |
| abstract_inverted_index.web | 193, 243 |
| abstract_inverted_index.(ML) | 74 |
| abstract_inverted_index.CPS. | 197 |
| abstract_inverted_index.LIME | 273 |
| abstract_inverted_index.This | 61, 120, 160 |
| abstract_inverted_index.aids | 5 |
| abstract_inverted_index.aims | 89 |
| abstract_inverted_index.data | 209 |
| abstract_inverted_index.fake | 146 |
| abstract_inverted_index.from | 157 |
| abstract_inverted_index.into | 132 |
| abstract_inverted_index.like | 153 |
| abstract_inverted_index.long | 237 |
| abstract_inverted_index.over | 13, 316 |
| abstract_inverted_index.role | 47 |
| abstract_inverted_index.such | 140 |
| abstract_inverted_index.text | 211 |
| abstract_inverted_index.that | 4, 111 |
| abstract_inverted_index.this | 69 |
| abstract_inverted_index.with | 39, 167 |
| abstract_inverted_index.(AOA) | 262 |
| abstract_inverted_index.(CPS) | 29 |
| abstract_inverted_index.99.29 | 314 |
| abstract_inverted_index.Hawks | 218 |
| abstract_inverted_index.based | 195 |
| abstract_inverted_index.data, | 18 |
| abstract_inverted_index.data. | 135 |
| abstract_inverted_index.first | 200 |
| abstract_inverted_index.kinds | 10 |
| abstract_inverted_index.last, | 265 |
| abstract_inverted_index.model | 241, 272 |
| abstract_inverted_index.novel | 65 |
| abstract_inverted_index.plays | 44 |
| abstract_inverted_index.three | 207 |
| abstract_inverted_index.users | 118 |
| abstract_inverted_index.using | 71, 257 |
| abstract_inverted_index.value | 312 |
| abstract_inverted_index.which | 35 |
| abstract_inverted_index.Aquila | 168, 259 |
| abstract_inverted_index.caused | 55 |
| abstract_inverted_index.causes | 112 |
| abstract_inverted_index.clever | 127 |
| abstract_inverted_index.create | 25 |
| abstract_inverted_index.derive | 227 |
| abstract_inverted_index.emails | 147 |
| abstract_inverted_index.lives, | 50 |
| abstract_inverted_index.losses | 115 |
| abstract_inverted_index.mainly | 185 |
| abstract_inverted_index.memory | 239 |
| abstract_inverted_index.method | 88, 223, 232, 268, 294, 307 |
| abstract_inverted_index.model. | 263 |
| abstract_inverted_index.modern | 49 |
| abstract_inverted_index.phase, | 201 |
| abstract_inverted_index.secure | 178 |
| abstract_inverted_index.threat | 110 |
| abstract_inverted_index.Harris' | 217 |
| abstract_inverted_index.acquire | 150 |
| abstract_inverted_index.address | 68 |
| abstract_inverted_index.applied | 225 |
| abstract_inverted_index.article | 161 |
| abstract_inverted_index.assured | 38 |
| abstract_inverted_index.attacks | 58 |
| abstract_inverted_index.between | 92 |
| abstract_inverted_index.carried | 204 |
| abstract_inverted_index.contain | 30 |
| abstract_inverted_index.control | 31 |
| abstract_inverted_index.deceive | 130 |
| abstract_inverted_index.details | 152 |
| abstract_inverted_index.devices | 12, 20 |
| abstract_inverted_index.enhance | 22 |
| abstract_inverted_index.feature | 81, 220, 228 |
| abstract_inverted_index.hackers | 125 |
| abstract_inverted_index.levels: | 208 |
| abstract_inverted_index.machine | 72 |
| abstract_inverted_index.methods | 75 |
| abstract_inverted_index.monitor | 19 |
| abstract_inverted_index.outcome | 290 |
| abstract_inverted_index.precise | 284 |
| abstract_inverted_index.problem | 70 |
| abstract_inverted_index.process | 282 |
| abstract_inverted_index.replace | 17 |
| abstract_inverted_index.systems | 28 |
| abstract_inverted_index.website | 78 |
| abstract_inverted_index.yearly. | 119 |
| abstract_inverted_index.(HHO-FS) | 222 |
| abstract_inverted_index.Besides, | 246 |
| abstract_inverted_index.MHA-LSTM | 252 |
| abstract_inverted_index.Phishing | 106, 173 |
| abstract_inverted_index.Systems. | 180 |
| abstract_inverted_index.accuracy | 311 |
| abstract_inverted_index.advanced | 142 |
| abstract_inverted_index.approach | 66, 176, 184, 253 |
| abstract_inverted_index.attempts | 101 |
| abstract_inverted_index.develops | 162 |
| abstract_inverted_index.enhanced | 255 |
| abstract_inverted_index.examined | 296 |
| abstract_inverted_index.existing | 317 |
| abstract_inverted_index.features | 98 |
| abstract_inverted_index.identity | 124 |
| abstract_inverted_index.includes | 123 |
| abstract_inverted_index.inherent | 104 |
| abstract_inverted_index.internet | 15, 43, 117 |
| abstract_inverted_index.learning | 73 |
| abstract_inverted_index.outcomes | 249 |
| abstract_inverted_index.phishers | 137 |
| abstract_inverted_index.phishing | 57, 77, 100, 143, 194, 244 |
| abstract_inverted_index.physical | 40 |
| abstract_inverted_index.presents | 63 |
| abstract_inverted_index.research | 62 |
| abstract_inverted_index.software | 144 |
| abstract_inverted_index.subsets. | 229 |
| abstract_inverted_index.superior | 275, 310 |
| abstract_inverted_index.utilizes | 233 |
| abstract_inverted_index.websites | 96 |
| abstract_inverted_index.Algorithm | 170 |
| abstract_inverted_index.accounts. | 159 |
| abstract_inverted_index.actuators | 23 |
| abstract_inverted_index.algorithm | 261 |
| abstract_inverted_index.analyzing | 103 |
| abstract_inverted_index.benchmark | 299 |
| abstract_inverted_index.black-box | 281 |
| abstract_inverted_index.challenge | 54 |
| abstract_inverted_index.cleaning, | 210 |
| abstract_inverted_index.compactly | 37 |
| abstract_inverted_index.database. | 300 |
| abstract_inverted_index.detection | 248 |
| abstract_inverted_index.developed | 182 |
| abstract_inverted_index.effectual | 188 |
| abstract_inverted_index.exhibited | 308 |
| abstract_inverted_index.extensive | 113 |
| abstract_inverted_index.financial | 114, 158 |
| abstract_inverted_index.illegally | 149 |
| abstract_inverted_index.malicious | 93 |
| abstract_inverted_index.outcomes. | 26 |
| abstract_inverted_index.passwords | 156 |
| abstract_inverted_index.patterns. | 105 |
| abstract_inverted_index.projected | 87 |
| abstract_inverted_index.prominent | 46 |
| abstract_inverted_index.revealing | 133 |
| abstract_inverted_index.selection | 221 |
| abstract_inverted_index.sensitive | 134 |
| abstract_inverted_index.usernames | 154 |
| abstract_inverted_index.utilizing | 126 |
| abstract_inverted_index.(MHA-LSTM) | 240 |
| abstract_inverted_index.Artificial | 165 |
| abstract_inverted_index.Generally, | 136 |
| abstract_inverted_index.Leveraging | 80 |
| abstract_inverted_index.XAIAOA-WPC | 183, 231, 267, 293, 306 |
| abstract_inverted_index.approaches | 128 |
| abstract_inverted_index.emphasizes | 186 |
| abstract_inverted_index.extraction | 82 |
| abstract_inverted_index.fraudulent | 121 |
| abstract_inverted_index.innovative | 84 |
| abstract_inverted_index.legitimate | 95 |
| abstract_inverted_index.multi-head | 235 |
| abstract_inverted_index.perception | 276 |
| abstract_inverted_index.short-term | 238 |
| abstract_inverted_index.simulation | 289 |
| abstract_inverted_index.strategies | 139 |
| abstract_inverted_index.technology | 3 |
| abstract_inverted_index.validation | 303 |
| abstract_inverted_index.Explainable | 164 |
| abstract_inverted_index.algorithms, | 85 |
| abstract_inverted_index.components, | 34 |
| abstract_inverted_index.computation | 33 |
| abstract_inverted_index.distinguish | 91 |
| abstract_inverted_index.individuals | 131 |
| abstract_inverted_index.intrusions. | 287 |
| abstract_inverted_index.procedures. | 41 |
| abstract_inverted_index.recognition | 191 |
| abstract_inverted_index.significant | 109 |
| abstract_inverted_index.techniques. | 318 |
| abstract_inverted_index.(XAIAOA-WPC) | 175 |
| abstract_inverted_index.Furthermore, | 215 |
| abstract_inverted_index.Intelligence | 166 |
| abstract_inverted_index.Optimization | 169 |
| abstract_inverted_index.confidential | 151 |
| abstract_inverted_index.experimental | 302 |
| abstract_inverted_index.incorporates | 269 |
| abstract_inverted_index.optimization | 260 |
| abstract_inverted_index.recognition. | 245 |
| abstract_inverted_index.significant. | 60 |
| abstract_inverted_index.cybersecurity | 53 |
| abstract_inverted_index.preprocessing | 202 |
| abstract_inverted_index.Classification | 174 |
| abstract_inverted_index.Cyber-Physical | 179 |
| abstract_inverted_index.Cyber-physical | 27 |
| abstract_inverted_index.classification | 189 |
| abstract_inverted_index.explainability | 278 |
| abstract_inverted_index.identification | 285 |
| abstract_inverted_index.preprocessing, | 212 |
| abstract_inverted_index.attention-based | 236 |
| abstract_inverted_index.classification. | 79 |
| abstract_inverted_index.interconnection | 7 |
| abstract_inverted_index.standardization. | 214 |
| abstract_inverted_index.optimization-based | 219 |
| cited_by_percentile_year.max | 99 |
| cited_by_percentile_year.min | 98 |
| countries_distinct_count | 0 |
| institutions_distinct_count | 8 |
| citation_normalized_percentile.value | 0.98583905 |
| citation_normalized_percentile.is_in_top_1_percent | True |
| citation_normalized_percentile.is_in_top_10_percent | True |