Identification of Phishing Attacks using Machine Learning Algorithm Article Swipe
 YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.1051/e3sconf/202339904010
YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.1051/e3sconf/202339904010
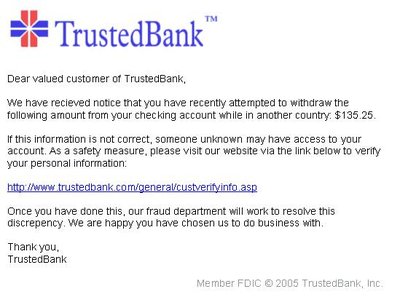
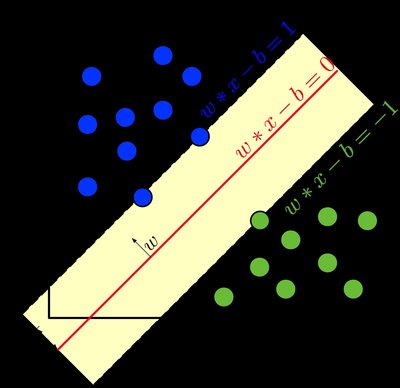
Phishing is a particular type of cybercrime that allows criminals to trick people and steal crucial data. The phishing assault has developed into a more complex attack vector since the first instance was published in 1990. Phishing is currently one of the most prevalent types of online fraud behavior. Phishing is done using a number of methods, such as through emails, phone calls, instant chats, adverts, pop-up windows on websites, and DNS poisoning. Phishing attacks can cause their victims to suffer significant losses, including the loss of confidential information, identity theft, businesses, and state secrets. By examining current phishing practises and assessing the state of phishing, this article seeks to assess these attacks. This article offers a fresh, in-depth model of phishing that takes into account attack stages, different types of attackers, threats, targets, attack media, and attacking strategies. Here, we categorise websites as real or phishing websites using machine learning techniques including Random Forest, XGBoost, and Logistic Regression. Additionally, the proposed anatomy will aid readers in comprehending the lifespan of a phishing attack, raising awareness of these attacks and the strategies employed as well as aiding in the creation of a comprehensive anti-phishing system.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.1051/e3sconf/202339904010
- https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdf
- OA Status
- diamond
- Cited By
- 15
- References
- 16
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4384572263
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4384572263Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1051/e3sconf/202339904010Digital Object Identifier
- Title
-
Identification of Phishing Attacks using Machine Learning AlgorithmWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2023Year of publication
- Publication date
-
2023-01-01Full publication date if available
- Authors
-
P. M. Dinesh, M Mukesh, B Navaneethan, R. S. Sabeenian, Paramasivam M.E, Manjunathan AlagarsamyList of authors in order
- Landing page
-
https://doi.org/10.1051/e3sconf/202339904010Publisher landing page
- PDF URL
-
https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdfDirect link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
diamondOpen access status per OpenAlex
- OA URL
-
https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdfDirect OA link when available
- Concepts
-
Phishing, Identity theft, Computer security, Computer science, Phone, Internet privacy, Identification (biology), Confidentiality, Cybercrime, Malware, Support vector machine, World Wide Web, Artificial intelligence, The Internet, Botany, Philosophy, Linguistics, BiologyTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
15Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 5, 2024: 10Per-year citation counts (last 5 years)
- References (count)
-
16Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4384572263 |
|---|---|
| doi | https://doi.org/10.1051/e3sconf/202339904010 |
| ids.doi | https://doi.org/10.1051/e3sconf/202339904010 |
| ids.openalex | https://openalex.org/W4384572263 |
| fwci | 9.2773144 |
| type | article |
| title | Identification of Phishing Attacks using Machine Learning Algorithm |
| biblio.issue | |
| biblio.volume | 399 |
| biblio.last_page | 04010 |
| biblio.first_page | 04010 |
| topics[0].id | https://openalex.org/T11644 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 1.0 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1710 |
| topics[0].subfield.display_name | Information Systems |
| topics[0].display_name | Spam and Phishing Detection |
| topics[1].id | https://openalex.org/T11241 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9911999702453613 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1711 |
| topics[1].subfield.display_name | Signal Processing |
| topics[1].display_name | Advanced Malware Detection Techniques |
| topics[2].id | https://openalex.org/T11800 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9876999855041504 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1710 |
| topics[2].subfield.display_name | Information Systems |
| topics[2].display_name | User Authentication and Security Systems |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C83860907 |
| concepts[0].level | 3 |
| concepts[0].score | 0.9863219261169434 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q135005 |
| concepts[0].display_name | Phishing |
| concepts[1].id | https://openalex.org/C522325796 |
| concepts[1].level | 2 |
| concepts[1].score | 0.7270259857177734 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q471880 |
| concepts[1].display_name | Identity theft |
| concepts[2].id | https://openalex.org/C38652104 |
| concepts[2].level | 1 |
| concepts[2].score | 0.6500922441482544 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[2].display_name | Computer security |
| concepts[3].id | https://openalex.org/C41008148 |
| concepts[3].level | 0 |
| concepts[3].score | 0.5679908990859985 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[3].display_name | Computer science |
| concepts[4].id | https://openalex.org/C2778707766 |
| concepts[4].level | 2 |
| concepts[4].score | 0.5344288349151611 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q202064 |
| concepts[4].display_name | Phone |
| concepts[5].id | https://openalex.org/C108827166 |
| concepts[5].level | 1 |
| concepts[5].score | 0.5227182507514954 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q175975 |
| concepts[5].display_name | Internet privacy |
| concepts[6].id | https://openalex.org/C116834253 |
| concepts[6].level | 2 |
| concepts[6].score | 0.5163984894752502 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q2039217 |
| concepts[6].display_name | Identification (biology) |
| concepts[7].id | https://openalex.org/C71745522 |
| concepts[7].level | 2 |
| concepts[7].score | 0.4915066659450531 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q2476929 |
| concepts[7].display_name | Confidentiality |
| concepts[8].id | https://openalex.org/C2779390178 |
| concepts[8].level | 3 |
| concepts[8].score | 0.49131837487220764 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q29137 |
| concepts[8].display_name | Cybercrime |
| concepts[9].id | https://openalex.org/C541664917 |
| concepts[9].level | 2 |
| concepts[9].score | 0.45457881689071655 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q14001 |
| concepts[9].display_name | Malware |
| concepts[10].id | https://openalex.org/C12267149 |
| concepts[10].level | 2 |
| concepts[10].score | 0.4493636190891266 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q282453 |
| concepts[10].display_name | Support vector machine |
| concepts[11].id | https://openalex.org/C136764020 |
| concepts[11].level | 1 |
| concepts[11].score | 0.32549941539764404 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q466 |
| concepts[11].display_name | World Wide Web |
| concepts[12].id | https://openalex.org/C154945302 |
| concepts[12].level | 1 |
| concepts[12].score | 0.3075921833515167 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[12].display_name | Artificial intelligence |
| concepts[13].id | https://openalex.org/C110875604 |
| concepts[13].level | 2 |
| concepts[13].score | 0.2918136417865753 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q75 |
| concepts[13].display_name | The Internet |
| concepts[14].id | https://openalex.org/C59822182 |
| concepts[14].level | 1 |
| concepts[14].score | 0.0 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q441 |
| concepts[14].display_name | Botany |
| concepts[15].id | https://openalex.org/C138885662 |
| concepts[15].level | 0 |
| concepts[15].score | 0.0 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q5891 |
| concepts[15].display_name | Philosophy |
| concepts[16].id | https://openalex.org/C41895202 |
| concepts[16].level | 1 |
| concepts[16].score | 0.0 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q8162 |
| concepts[16].display_name | Linguistics |
| concepts[17].id | https://openalex.org/C86803240 |
| concepts[17].level | 0 |
| concepts[17].score | 0.0 |
| concepts[17].wikidata | https://www.wikidata.org/wiki/Q420 |
| concepts[17].display_name | Biology |
| keywords[0].id | https://openalex.org/keywords/phishing |
| keywords[0].score | 0.9863219261169434 |
| keywords[0].display_name | Phishing |
| keywords[1].id | https://openalex.org/keywords/identity-theft |
| keywords[1].score | 0.7270259857177734 |
| keywords[1].display_name | Identity theft |
| keywords[2].id | https://openalex.org/keywords/computer-security |
| keywords[2].score | 0.6500922441482544 |
| keywords[2].display_name | Computer security |
| keywords[3].id | https://openalex.org/keywords/computer-science |
| keywords[3].score | 0.5679908990859985 |
| keywords[3].display_name | Computer science |
| keywords[4].id | https://openalex.org/keywords/phone |
| keywords[4].score | 0.5344288349151611 |
| keywords[4].display_name | Phone |
| keywords[5].id | https://openalex.org/keywords/internet-privacy |
| keywords[5].score | 0.5227182507514954 |
| keywords[5].display_name | Internet privacy |
| keywords[6].id | https://openalex.org/keywords/identification |
| keywords[6].score | 0.5163984894752502 |
| keywords[6].display_name | Identification (biology) |
| keywords[7].id | https://openalex.org/keywords/confidentiality |
| keywords[7].score | 0.4915066659450531 |
| keywords[7].display_name | Confidentiality |
| keywords[8].id | https://openalex.org/keywords/cybercrime |
| keywords[8].score | 0.49131837487220764 |
| keywords[8].display_name | Cybercrime |
| keywords[9].id | https://openalex.org/keywords/malware |
| keywords[9].score | 0.45457881689071655 |
| keywords[9].display_name | Malware |
| keywords[10].id | https://openalex.org/keywords/support-vector-machine |
| keywords[10].score | 0.4493636190891266 |
| keywords[10].display_name | Support vector machine |
| keywords[11].id | https://openalex.org/keywords/world-wide-web |
| keywords[11].score | 0.32549941539764404 |
| keywords[11].display_name | World Wide Web |
| keywords[12].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[12].score | 0.3075921833515167 |
| keywords[12].display_name | Artificial intelligence |
| keywords[13].id | https://openalex.org/keywords/the-internet |
| keywords[13].score | 0.2918136417865753 |
| keywords[13].display_name | The Internet |
| language | en |
| locations[0].id | doi:10.1051/e3sconf/202339904010 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210186093 |
| locations[0].source.issn | 2267-1242, 2555-0403 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2267-1242 |
| locations[0].source.is_core | False |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | E3S Web of Conferences |
| locations[0].source.host_organization | https://openalex.org/P4310319748 |
| locations[0].source.host_organization_name | EDP Sciences |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310319748 |
| locations[0].source.host_organization_lineage_names | EDP Sciences |
| locations[0].license | cc-by |
| locations[0].pdf_url | https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdf |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | E3S Web of Conferences |
| locations[0].landing_page_url | https://doi.org/10.1051/e3sconf/202339904010 |
| locations[1].id | pmh:oai:doaj.org/article:cbd877efc9dc4ecaba8c1cf019fd9580 |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306401280 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[1].source.host_organization | |
| locations[1].source.host_organization_name | |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | submittedVersion |
| locations[1].raw_type | article |
| locations[1].license_id | |
| locations[1].is_accepted | False |
| locations[1].is_published | False |
| locations[1].raw_source_name | E3S Web of Conferences, Vol 399, p 04010 (2023) |
| locations[1].landing_page_url | https://doaj.org/article/cbd877efc9dc4ecaba8c1cf019fd9580 |
| locations[2].id | pmh:oai:edpsciences.org:dkey/10.1051/e3sconf/202339904010 |
| locations[2].is_oa | False |
| locations[2].source.id | https://openalex.org/S4306400744 |
| locations[2].source.issn | |
| locations[2].source.type | repository |
| locations[2].source.is_oa | False |
| locations[2].source.issn_l | |
| locations[2].source.is_core | False |
| locations[2].source.is_in_doaj | False |
| locations[2].source.display_name | Springer Link (Chiba Institute of Technology) |
| locations[2].source.host_organization | https://openalex.org/I8488066 |
| locations[2].source.host_organization_name | Chiba Institute of Technology |
| locations[2].source.host_organization_lineage | https://openalex.org/I8488066 |
| locations[2].license | |
| locations[2].pdf_url | |
| locations[2].version | submittedVersion |
| locations[2].raw_type | Text |
| locations[2].license_id | |
| locations[2].is_accepted | False |
| locations[2].is_published | False |
| locations[2].raw_source_name | https://doi.org/10.1051/e3sconf/202339904010 |
| locations[2].landing_page_url | |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5010089660 |
| authorships[0].author.orcid | https://orcid.org/0000-0001-8740-8903 |
| authorships[0].author.display_name | P. M. Dinesh |
| authorships[0].affiliations[0].raw_affiliation_string | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Dinesh P.M |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[1].author.id | https://openalex.org/A5104144616 |
| authorships[1].author.orcid | |
| authorships[1].author.display_name | M Mukesh |
| authorships[1].affiliations[0].raw_affiliation_string | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Mukesh M |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[2].author.id | https://openalex.org/A5092488856 |
| authorships[2].author.orcid | |
| authorships[2].author.display_name | B Navaneethan |
| authorships[2].affiliations[0].raw_affiliation_string | Spring Five, Bangalore, India |
| authorships[2].author_position | middle |
| authorships[2].raw_author_name | Navaneethan B |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | Spring Five, Bangalore, India |
| authorships[3].author.id | https://openalex.org/A5091833836 |
| authorships[3].author.orcid | |
| authorships[3].author.display_name | R. S. Sabeenian |
| authorships[3].affiliations[0].raw_affiliation_string | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[3].author_position | middle |
| authorships[3].raw_author_name | Sabeenian R.S |
| authorships[3].is_corresponding | False |
| authorships[3].raw_affiliation_strings | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[4].author.id | https://openalex.org/A5112961755 |
| authorships[4].author.orcid | |
| authorships[4].author.display_name | Paramasivam M.E |
| authorships[4].affiliations[0].raw_affiliation_string | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[4].author_position | middle |
| authorships[4].raw_author_name | Paramasivam M.E |
| authorships[4].is_corresponding | False |
| authorships[4].raw_affiliation_strings | Department of Electronics and Communication Engineering, Sona College of Technology, Salem, India |
| authorships[5].author.id | https://openalex.org/A5047706793 |
| authorships[5].author.orcid | |
| authorships[5].author.display_name | Manjunathan Alagarsamy |
| authorships[5].affiliations[0].raw_affiliation_string | Department of Electronics and Communication Engineering, K.Ramakrishnan College of Technology, Trichy-621112, Tamil Nadu, India |
| authorships[5].author_position | last |
| authorships[5].raw_author_name | Manjunathan A |
| authorships[5].is_corresponding | False |
| authorships[5].raw_affiliation_strings | Department of Electronics and Communication Engineering, K.Ramakrishnan College of Technology, Trichy-621112, Tamil Nadu, India |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdf |
| open_access.oa_status | diamond |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Identification of Phishing Attacks using Machine Learning Algorithm |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T11644 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 1.0 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1710 |
| primary_topic.subfield.display_name | Information Systems |
| primary_topic.display_name | Spam and Phishing Detection |
| related_works | https://openalex.org/W1648378477, https://openalex.org/W2032900633, https://openalex.org/W2595760708, https://openalex.org/W182956790, https://openalex.org/W2911255625, https://openalex.org/W2186893595, https://openalex.org/W1981963489, https://openalex.org/W1559396486, https://openalex.org/W3214845967, https://openalex.org/W2121587354 |
| cited_by_count | 15 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 5 |
| counts_by_year[1].year | 2024 |
| counts_by_year[1].cited_by_count | 10 |
| locations_count | 3 |
| best_oa_location.id | doi:10.1051/e3sconf/202339904010 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210186093 |
| best_oa_location.source.issn | 2267-1242, 2555-0403 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2267-1242 |
| best_oa_location.source.is_core | False |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | E3S Web of Conferences |
| best_oa_location.source.host_organization | https://openalex.org/P4310319748 |
| best_oa_location.source.host_organization_name | EDP Sciences |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310319748 |
| best_oa_location.source.host_organization_lineage_names | EDP Sciences |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdf |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | E3S Web of Conferences |
| best_oa_location.landing_page_url | https://doi.org/10.1051/e3sconf/202339904010 |
| primary_location.id | doi:10.1051/e3sconf/202339904010 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210186093 |
| primary_location.source.issn | 2267-1242, 2555-0403 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2267-1242 |
| primary_location.source.is_core | False |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | E3S Web of Conferences |
| primary_location.source.host_organization | https://openalex.org/P4310319748 |
| primary_location.source.host_organization_name | EDP Sciences |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310319748 |
| primary_location.source.host_organization_lineage_names | EDP Sciences |
| primary_location.license | cc-by |
| primary_location.pdf_url | https://www.e3s-conferences.org/articles/e3sconf/pdf/2023/36/e3sconf_iconnect2023_04010.pdf |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | E3S Web of Conferences |
| primary_location.landing_page_url | https://doi.org/10.1051/e3sconf/202339904010 |
| publication_date | 2023-01-01 |
| publication_year | 2023 |
| referenced_works | https://openalex.org/W3133843004, https://openalex.org/W2783033852, https://openalex.org/W1964088283, https://openalex.org/W2166731089, https://openalex.org/W2100486461, https://openalex.org/W4295953858, https://openalex.org/W2890718808, https://openalex.org/W2792144656, https://openalex.org/W2525684119, https://openalex.org/W4247104955, https://openalex.org/W1953683851, https://openalex.org/W2221203134, https://openalex.org/W2053626416, https://openalex.org/W1534216444, https://openalex.org/W3119446614, https://openalex.org/W2761330267 |
| referenced_works_count | 16 |
| abstract_inverted_index.a | 2, 23, 53, 116, 171, 191 |
| abstract_inverted_index.By | 95 |
| abstract_inverted_index.as | 58, 143, 183, 185 |
| abstract_inverted_index.in | 34, 166, 187 |
| abstract_inverted_index.is | 1, 37, 50 |
| abstract_inverted_index.of | 5, 40, 45, 55, 86, 104, 120, 130, 170, 176, 190 |
| abstract_inverted_index.on | 68 |
| abstract_inverted_index.or | 145 |
| abstract_inverted_index.to | 10, 79, 109 |
| abstract_inverted_index.we | 140 |
| abstract_inverted_index.DNS | 71 |
| abstract_inverted_index.The | 17 |
| abstract_inverted_index.aid | 164 |
| abstract_inverted_index.and | 13, 70, 92, 100, 136, 156, 179 |
| abstract_inverted_index.can | 75 |
| abstract_inverted_index.has | 20 |
| abstract_inverted_index.one | 39 |
| abstract_inverted_index.the | 29, 41, 84, 102, 160, 168, 180, 188 |
| abstract_inverted_index.was | 32 |
| abstract_inverted_index.This | 113 |
| abstract_inverted_index.done | 51 |
| abstract_inverted_index.into | 22, 124 |
| abstract_inverted_index.loss | 85 |
| abstract_inverted_index.more | 24 |
| abstract_inverted_index.most | 42 |
| abstract_inverted_index.real | 144 |
| abstract_inverted_index.such | 57 |
| abstract_inverted_index.that | 7, 122 |
| abstract_inverted_index.this | 106 |
| abstract_inverted_index.type | 4 |
| abstract_inverted_index.well | 184 |
| abstract_inverted_index.will | 163 |
| abstract_inverted_index.1990. | 35 |
| abstract_inverted_index.Here, | 139 |
| abstract_inverted_index.cause | 76 |
| abstract_inverted_index.data. | 16 |
| abstract_inverted_index.first | 30 |
| abstract_inverted_index.fraud | 47 |
| abstract_inverted_index.model | 119 |
| abstract_inverted_index.phone | 61 |
| abstract_inverted_index.seeks | 108 |
| abstract_inverted_index.since | 28 |
| abstract_inverted_index.state | 93, 103 |
| abstract_inverted_index.steal | 14 |
| abstract_inverted_index.takes | 123 |
| abstract_inverted_index.their | 77 |
| abstract_inverted_index.these | 111, 177 |
| abstract_inverted_index.trick | 11 |
| abstract_inverted_index.types | 44, 129 |
| abstract_inverted_index.using | 52, 148 |
| abstract_inverted_index.Random | 153 |
| abstract_inverted_index.aiding | 186 |
| abstract_inverted_index.allows | 8 |
| abstract_inverted_index.assess | 110 |
| abstract_inverted_index.attack | 26, 126, 134 |
| abstract_inverted_index.calls, | 62 |
| abstract_inverted_index.chats, | 64 |
| abstract_inverted_index.fresh, | 117 |
| abstract_inverted_index.media, | 135 |
| abstract_inverted_index.number | 54 |
| abstract_inverted_index.offers | 115 |
| abstract_inverted_index.online | 46 |
| abstract_inverted_index.people | 12 |
| abstract_inverted_index.pop-up | 66 |
| abstract_inverted_index.suffer | 80 |
| abstract_inverted_index.theft, | 90 |
| abstract_inverted_index.vector | 27 |
| abstract_inverted_index.Forest, | 154 |
| abstract_inverted_index.account | 125 |
| abstract_inverted_index.anatomy | 162 |
| abstract_inverted_index.article | 107, 114 |
| abstract_inverted_index.assault | 19 |
| abstract_inverted_index.attack, | 173 |
| abstract_inverted_index.attacks | 74, 178 |
| abstract_inverted_index.complex | 25 |
| abstract_inverted_index.crucial | 15 |
| abstract_inverted_index.current | 97 |
| abstract_inverted_index.emails, | 60 |
| abstract_inverted_index.instant | 63 |
| abstract_inverted_index.losses, | 82 |
| abstract_inverted_index.machine | 149 |
| abstract_inverted_index.raising | 174 |
| abstract_inverted_index.readers | 165 |
| abstract_inverted_index.stages, | 127 |
| abstract_inverted_index.system. | 194 |
| abstract_inverted_index.through | 59 |
| abstract_inverted_index.victims | 78 |
| abstract_inverted_index.windows | 67 |
| abstract_inverted_index.Logistic | 157 |
| abstract_inverted_index.Phishing | 0, 36, 49, 73 |
| abstract_inverted_index.XGBoost, | 155 |
| abstract_inverted_index.adverts, | 65 |
| abstract_inverted_index.attacks. | 112 |
| abstract_inverted_index.creation | 189 |
| abstract_inverted_index.employed | 182 |
| abstract_inverted_index.identity | 89 |
| abstract_inverted_index.in-depth | 118 |
| abstract_inverted_index.instance | 31 |
| abstract_inverted_index.learning | 150 |
| abstract_inverted_index.lifespan | 169 |
| abstract_inverted_index.methods, | 56 |
| abstract_inverted_index.phishing | 18, 98, 121, 146, 172 |
| abstract_inverted_index.proposed | 161 |
| abstract_inverted_index.secrets. | 94 |
| abstract_inverted_index.targets, | 133 |
| abstract_inverted_index.threats, | 132 |
| abstract_inverted_index.websites | 142, 147 |
| abstract_inverted_index.assessing | 101 |
| abstract_inverted_index.attacking | 137 |
| abstract_inverted_index.awareness | 175 |
| abstract_inverted_index.behavior. | 48 |
| abstract_inverted_index.criminals | 9 |
| abstract_inverted_index.currently | 38 |
| abstract_inverted_index.developed | 21 |
| abstract_inverted_index.different | 128 |
| abstract_inverted_index.examining | 96 |
| abstract_inverted_index.including | 83, 152 |
| abstract_inverted_index.phishing, | 105 |
| abstract_inverted_index.practises | 99 |
| abstract_inverted_index.prevalent | 43 |
| abstract_inverted_index.published | 33 |
| abstract_inverted_index.websites, | 69 |
| abstract_inverted_index.attackers, | 131 |
| abstract_inverted_index.categorise | 141 |
| abstract_inverted_index.cybercrime | 6 |
| abstract_inverted_index.particular | 3 |
| abstract_inverted_index.poisoning. | 72 |
| abstract_inverted_index.strategies | 181 |
| abstract_inverted_index.techniques | 151 |
| abstract_inverted_index.Regression. | 158 |
| abstract_inverted_index.businesses, | 91 |
| abstract_inverted_index.significant | 81 |
| abstract_inverted_index.strategies. | 138 |
| abstract_inverted_index.confidential | 87 |
| abstract_inverted_index.information, | 88 |
| abstract_inverted_index.Additionally, | 159 |
| abstract_inverted_index.anti-phishing | 193 |
| abstract_inverted_index.comprehending | 167 |
| abstract_inverted_index.comprehensive | 192 |
| cited_by_percentile_year.max | 99 |
| cited_by_percentile_year.min | 98 |
| countries_distinct_count | 0 |
| institutions_distinct_count | 6 |
| sustainable_development_goals[0].id | https://metadata.un.org/sdg/16 |
| sustainable_development_goals[0].score | 0.8100000023841858 |
| sustainable_development_goals[0].display_name | Peace, Justice and strong institutions |
| citation_normalized_percentile.value | 0.97355586 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |