Leveraging Graph-Based Representations to Enhance Machine Learning Performance in IIoT Network Security and Attack Detection Article Swipe
 YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.3390/app13137774
YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.3390/app13137774
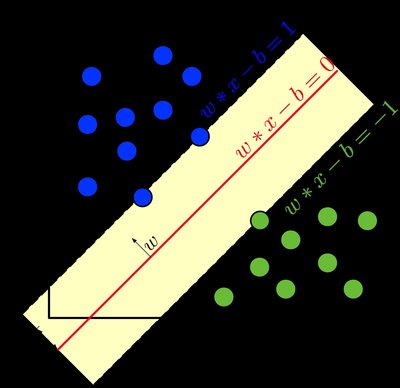
In the dynamic and ever-evolving realm of network security, the ability to accurately identify and classify portscan attacks both inside and outside networks is of paramount importance. This study delves into the underexplored potential of fusing graph theory with machine learning models to elevate their anomaly detection capabilities in the context of industrial Internet of things (IIoT) network data analysis. We employed a comprehensive experimental approach, encompassing data preprocessing, visualization, feature analysis, and machine learning model comparison, to assess the efficacy of graph theory representation in improving classification accuracy. More specifically, we converted network traffic data into a graph-based representation, where nodes represent devices and edges represent communication instances. We then incorporated these graph features into our machine learning models. Our findings reveal that incorporating graph theory into the analysis of network data results in a modest-yet-meaningful improvement in the performance of the tested machine learning models, including logistic regression, support vector machines, and K-means clustering. These results underscore the significance of graph theory representation in bolstering the discriminative capabilities of machine learning algorithms when applied to network data.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.3390/app13137774
- https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411
- OA Status
- gold
- Cited By
- 11
- References
- 38
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4382982133
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4382982133Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.3390/app13137774Digital Object Identifier
- Title
-
Leveraging Graph-Based Representations to Enhance Machine Learning Performance in IIoT Network Security and Attack DetectionWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2023Year of publication
- Publication date
-
2023-06-30Full publication date if available
- Authors
-
Bader Alwasel, Abdulaziz Aldribi, Mohammed Alreshoodi, Ibrahim S. Alsukayti, Mohammed AlsuhaibaniList of authors in order
- Landing page
-
https://doi.org/10.3390/app13137774Publisher landing page
- PDF URL
-
https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411Direct link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
goldOpen access status per OpenAlex
- OA URL
-
https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411Direct OA link when available
- Concepts
-
Computer science, Machine learning, Artificial intelligence, Graph kernel, Graph, Feature learning, Cluster analysis, Support vector machine, Network security, Graph theory, Preprocessor, Discriminative model, Data mining, Data pre-processing, Theoretical computer science, Kernel method, Radial basis function kernel, Computer security, Mathematics, CombinatoricsTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
11Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 5, 2024: 5, 2023: 1Per-year citation counts (last 5 years)
- References (count)
-
38Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4382982133 |
|---|---|
| doi | https://doi.org/10.3390/app13137774 |
| ids.doi | https://doi.org/10.3390/app13137774 |
| ids.openalex | https://openalex.org/W4382982133 |
| fwci | 4.83507521 |
| type | article |
| title | Leveraging Graph-Based Representations to Enhance Machine Learning Performance in IIoT Network Security and Attack Detection |
| biblio.issue | 13 |
| biblio.volume | 13 |
| biblio.last_page | 7774 |
| biblio.first_page | 7774 |
| topics[0].id | https://openalex.org/T10400 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9990000128746033 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1705 |
| topics[0].subfield.display_name | Computer Networks and Communications |
| topics[0].display_name | Network Security and Intrusion Detection |
| topics[1].id | https://openalex.org/T10064 |
| topics[1].field.id | https://openalex.org/fields/31 |
| topics[1].field.display_name | Physics and Astronomy |
| topics[1].score | 0.9983999729156494 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/3109 |
| topics[1].subfield.display_name | Statistical and Nonlinear Physics |
| topics[1].display_name | Complex Network Analysis Techniques |
| topics[2].id | https://openalex.org/T11273 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9739000201225281 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1702 |
| topics[2].subfield.display_name | Artificial Intelligence |
| topics[2].display_name | Advanced Graph Neural Networks |
| is_xpac | False |
| apc_list.value | 2300 |
| apc_list.currency | CHF |
| apc_list.value_usd | 2490 |
| apc_paid.value | 2300 |
| apc_paid.currency | CHF |
| apc_paid.value_usd | 2490 |
| concepts[0].id | https://openalex.org/C41008148 |
| concepts[0].level | 0 |
| concepts[0].score | 0.7659865617752075 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[0].display_name | Computer science |
| concepts[1].id | https://openalex.org/C119857082 |
| concepts[1].level | 1 |
| concepts[1].score | 0.6126763224601746 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q2539 |
| concepts[1].display_name | Machine learning |
| concepts[2].id | https://openalex.org/C154945302 |
| concepts[2].level | 1 |
| concepts[2].score | 0.6097229719161987 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[2].display_name | Artificial intelligence |
| concepts[3].id | https://openalex.org/C100595998 |
| concepts[3].level | 5 |
| concepts[3].score | 0.4956921339035034 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q11731931 |
| concepts[3].display_name | Graph kernel |
| concepts[4].id | https://openalex.org/C132525143 |
| concepts[4].level | 2 |
| concepts[4].score | 0.49321430921554565 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q141488 |
| concepts[4].display_name | Graph |
| concepts[5].id | https://openalex.org/C59404180 |
| concepts[5].level | 2 |
| concepts[5].score | 0.49116966128349304 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q17013334 |
| concepts[5].display_name | Feature learning |
| concepts[6].id | https://openalex.org/C73555534 |
| concepts[6].level | 2 |
| concepts[6].score | 0.4844396412372589 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q622825 |
| concepts[6].display_name | Cluster analysis |
| concepts[7].id | https://openalex.org/C12267149 |
| concepts[7].level | 2 |
| concepts[7].score | 0.4696204960346222 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q282453 |
| concepts[7].display_name | Support vector machine |
| concepts[8].id | https://openalex.org/C182590292 |
| concepts[8].level | 2 |
| concepts[8].score | 0.44951510429382324 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q989632 |
| concepts[8].display_name | Network security |
| concepts[9].id | https://openalex.org/C88230418 |
| concepts[9].level | 2 |
| concepts[9].score | 0.44638559222221375 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q131476 |
| concepts[9].display_name | Graph theory |
| concepts[10].id | https://openalex.org/C34736171 |
| concepts[10].level | 2 |
| concepts[10].score | 0.441877156496048 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q918333 |
| concepts[10].display_name | Preprocessor |
| concepts[11].id | https://openalex.org/C97931131 |
| concepts[11].level | 2 |
| concepts[11].score | 0.42815542221069336 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q5282087 |
| concepts[11].display_name | Discriminative model |
| concepts[12].id | https://openalex.org/C124101348 |
| concepts[12].level | 1 |
| concepts[12].score | 0.4187767803668976 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q172491 |
| concepts[12].display_name | Data mining |
| concepts[13].id | https://openalex.org/C10551718 |
| concepts[13].level | 2 |
| concepts[13].score | 0.41292405128479004 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q5227332 |
| concepts[13].display_name | Data pre-processing |
| concepts[14].id | https://openalex.org/C80444323 |
| concepts[14].level | 1 |
| concepts[14].score | 0.333370566368103 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q2878974 |
| concepts[14].display_name | Theoretical computer science |
| concepts[15].id | https://openalex.org/C122280245 |
| concepts[15].level | 3 |
| concepts[15].score | 0.23449701070785522 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q620622 |
| concepts[15].display_name | Kernel method |
| concepts[16].id | https://openalex.org/C75866337 |
| concepts[16].level | 4 |
| concepts[16].score | 0.12123218178749084 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q7280263 |
| concepts[16].display_name | Radial basis function kernel |
| concepts[17].id | https://openalex.org/C38652104 |
| concepts[17].level | 1 |
| concepts[17].score | 0.0909644365310669 |
| concepts[17].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[17].display_name | Computer security |
| concepts[18].id | https://openalex.org/C33923547 |
| concepts[18].level | 0 |
| concepts[18].score | 0.0 |
| concepts[18].wikidata | https://www.wikidata.org/wiki/Q395 |
| concepts[18].display_name | Mathematics |
| concepts[19].id | https://openalex.org/C114614502 |
| concepts[19].level | 1 |
| concepts[19].score | 0.0 |
| concepts[19].wikidata | https://www.wikidata.org/wiki/Q76592 |
| concepts[19].display_name | Combinatorics |
| keywords[0].id | https://openalex.org/keywords/computer-science |
| keywords[0].score | 0.7659865617752075 |
| keywords[0].display_name | Computer science |
| keywords[1].id | https://openalex.org/keywords/machine-learning |
| keywords[1].score | 0.6126763224601746 |
| keywords[1].display_name | Machine learning |
| keywords[2].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[2].score | 0.6097229719161987 |
| keywords[2].display_name | Artificial intelligence |
| keywords[3].id | https://openalex.org/keywords/graph-kernel |
| keywords[3].score | 0.4956921339035034 |
| keywords[3].display_name | Graph kernel |
| keywords[4].id | https://openalex.org/keywords/graph |
| keywords[4].score | 0.49321430921554565 |
| keywords[4].display_name | Graph |
| keywords[5].id | https://openalex.org/keywords/feature-learning |
| keywords[5].score | 0.49116966128349304 |
| keywords[5].display_name | Feature learning |
| keywords[6].id | https://openalex.org/keywords/cluster-analysis |
| keywords[6].score | 0.4844396412372589 |
| keywords[6].display_name | Cluster analysis |
| keywords[7].id | https://openalex.org/keywords/support-vector-machine |
| keywords[7].score | 0.4696204960346222 |
| keywords[7].display_name | Support vector machine |
| keywords[8].id | https://openalex.org/keywords/network-security |
| keywords[8].score | 0.44951510429382324 |
| keywords[8].display_name | Network security |
| keywords[9].id | https://openalex.org/keywords/graph-theory |
| keywords[9].score | 0.44638559222221375 |
| keywords[9].display_name | Graph theory |
| keywords[10].id | https://openalex.org/keywords/preprocessor |
| keywords[10].score | 0.441877156496048 |
| keywords[10].display_name | Preprocessor |
| keywords[11].id | https://openalex.org/keywords/discriminative-model |
| keywords[11].score | 0.42815542221069336 |
| keywords[11].display_name | Discriminative model |
| keywords[12].id | https://openalex.org/keywords/data-mining |
| keywords[12].score | 0.4187767803668976 |
| keywords[12].display_name | Data mining |
| keywords[13].id | https://openalex.org/keywords/data-pre-processing |
| keywords[13].score | 0.41292405128479004 |
| keywords[13].display_name | Data pre-processing |
| keywords[14].id | https://openalex.org/keywords/theoretical-computer-science |
| keywords[14].score | 0.333370566368103 |
| keywords[14].display_name | Theoretical computer science |
| keywords[15].id | https://openalex.org/keywords/kernel-method |
| keywords[15].score | 0.23449701070785522 |
| keywords[15].display_name | Kernel method |
| keywords[16].id | https://openalex.org/keywords/radial-basis-function-kernel |
| keywords[16].score | 0.12123218178749084 |
| keywords[16].display_name | Radial basis function kernel |
| keywords[17].id | https://openalex.org/keywords/computer-security |
| keywords[17].score | 0.0909644365310669 |
| keywords[17].display_name | Computer security |
| language | en |
| locations[0].id | doi:10.3390/app13137774 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210205812 |
| locations[0].source.issn | 2076-3417 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2076-3417 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | Applied Sciences |
| locations[0].source.host_organization | https://openalex.org/P4310310987 |
| locations[0].source.host_organization_name | Multidisciplinary Digital Publishing Institute |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310310987 |
| locations[0].source.host_organization_lineage_names | Multidisciplinary Digital Publishing Institute |
| locations[0].license | cc-by |
| locations[0].pdf_url | https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411 |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | https://openalex.org/licenses/cc-by |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Applied Sciences |
| locations[0].landing_page_url | https://doi.org/10.3390/app13137774 |
| locations[1].id | pmh:oai:doaj.org/article:05c3a752fe6d489ebf23c0f6d41e9b31 |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306401280 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[1].source.host_organization | |
| locations[1].source.host_organization_name | |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | submittedVersion |
| locations[1].raw_type | article |
| locations[1].license_id | |
| locations[1].is_accepted | False |
| locations[1].is_published | False |
| locations[1].raw_source_name | Applied Sciences, Vol 13, Iss 13, p 7774 (2023) |
| locations[1].landing_page_url | https://doaj.org/article/05c3a752fe6d489ebf23c0f6d41e9b31 |
| locations[2].id | pmh:oai:mdpi.com:/2076-3417/13/13/7774/ |
| locations[2].is_oa | True |
| locations[2].source.id | https://openalex.org/S4306400947 |
| locations[2].source.issn | |
| locations[2].source.type | repository |
| locations[2].source.is_oa | True |
| locations[2].source.issn_l | |
| locations[2].source.is_core | False |
| locations[2].source.is_in_doaj | False |
| locations[2].source.display_name | MDPI (MDPI AG) |
| locations[2].source.host_organization | https://openalex.org/I4210097602 |
| locations[2].source.host_organization_name | Multidisciplinary Digital Publishing Institute (Switzerland) |
| locations[2].source.host_organization_lineage | https://openalex.org/I4210097602 |
| locations[2].license | cc-by |
| locations[2].pdf_url | |
| locations[2].version | submittedVersion |
| locations[2].raw_type | Text |
| locations[2].license_id | https://openalex.org/licenses/cc-by |
| locations[2].is_accepted | False |
| locations[2].is_published | False |
| locations[2].raw_source_name | Applied Sciences; Volume 13; Issue 13; Pages: 7774 |
| locations[2].landing_page_url | https://dx.doi.org/10.3390/app13137774 |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5043031770 |
| authorships[0].author.orcid | https://orcid.org/0000-0002-9822-7080 |
| authorships[0].author.display_name | Bader Alwasel |
| authorships[0].countries | SA |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I156216236, https://openalex.org/I4210092650 |
| authorships[0].affiliations[0].raw_affiliation_string | Unit of Scientific Research, Applied College, Qassim University, Buraydah 52571, Saudi Arabia |
| authorships[0].institutions[0].id | https://openalex.org/I4210092650 |
| authorships[0].institutions[0].ror | https://ror.org/00j0krs40 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I4210092650 |
| authorships[0].institutions[0].country_code | SA |
| authorships[0].institutions[0].display_name | Buraydah Colleges |
| authorships[0].institutions[1].id | https://openalex.org/I156216236 |
| authorships[0].institutions[1].ror | https://ror.org/01wsfe280 |
| authorships[0].institutions[1].type | education |
| authorships[0].institutions[1].lineage | https://openalex.org/I156216236 |
| authorships[0].institutions[1].country_code | SA |
| authorships[0].institutions[1].display_name | Qassim University |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Bader Alwasel |
| authorships[0].is_corresponding | True |
| authorships[0].raw_affiliation_strings | Unit of Scientific Research, Applied College, Qassim University, Buraydah 52571, Saudi Arabia |
| authorships[1].author.id | https://openalex.org/A5011563378 |
| authorships[1].author.orcid | https://orcid.org/0000-0001-5975-3929 |
| authorships[1].author.display_name | Abdulaziz Aldribi |
| authorships[1].countries | SA |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I156216236 |
| authorships[1].affiliations[0].raw_affiliation_string | Department of Computer Science, College of Computer, Qassim University, Buraydah 51452, Saudi Arabia |
| authorships[1].institutions[0].id | https://openalex.org/I156216236 |
| authorships[1].institutions[0].ror | https://ror.org/01wsfe280 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I156216236 |
| authorships[1].institutions[0].country_code | SA |
| authorships[1].institutions[0].display_name | Qassim University |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Abdulaziz Aldribi |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Department of Computer Science, College of Computer, Qassim University, Buraydah 51452, Saudi Arabia |
| authorships[2].author.id | https://openalex.org/A5012245972 |
| authorships[2].author.orcid | https://orcid.org/0000-0002-3066-6909 |
| authorships[2].author.display_name | Mohammed Alreshoodi |
| authorships[2].countries | SA |
| authorships[2].affiliations[0].institution_ids | https://openalex.org/I156216236, https://openalex.org/I4210092650 |
| authorships[2].affiliations[0].raw_affiliation_string | Unit of Scientific Research, Applied College, Qassim University, Buraydah 52571, Saudi Arabia |
| authorships[2].institutions[0].id | https://openalex.org/I4210092650 |
| authorships[2].institutions[0].ror | https://ror.org/00j0krs40 |
| authorships[2].institutions[0].type | education |
| authorships[2].institutions[0].lineage | https://openalex.org/I4210092650 |
| authorships[2].institutions[0].country_code | SA |
| authorships[2].institutions[0].display_name | Buraydah Colleges |
| authorships[2].institutions[1].id | https://openalex.org/I156216236 |
| authorships[2].institutions[1].ror | https://ror.org/01wsfe280 |
| authorships[2].institutions[1].type | education |
| authorships[2].institutions[1].lineage | https://openalex.org/I156216236 |
| authorships[2].institutions[1].country_code | SA |
| authorships[2].institutions[1].display_name | Qassim University |
| authorships[2].author_position | middle |
| authorships[2].raw_author_name | Mohammed Alreshoodi |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | Unit of Scientific Research, Applied College, Qassim University, Buraydah 52571, Saudi Arabia |
| authorships[3].author.id | https://openalex.org/A5029886621 |
| authorships[3].author.orcid | https://orcid.org/0000-0002-6925-598X |
| authorships[3].author.display_name | Ibrahim S. Alsukayti |
| authorships[3].countries | SA |
| authorships[3].affiliations[0].institution_ids | https://openalex.org/I156216236 |
| authorships[3].affiliations[0].raw_affiliation_string | Department of Computer Science, College of Computer, Qassim University, Buraydah 51452, Saudi Arabia |
| authorships[3].institutions[0].id | https://openalex.org/I156216236 |
| authorships[3].institutions[0].ror | https://ror.org/01wsfe280 |
| authorships[3].institutions[0].type | education |
| authorships[3].institutions[0].lineage | https://openalex.org/I156216236 |
| authorships[3].institutions[0].country_code | SA |
| authorships[3].institutions[0].display_name | Qassim University |
| authorships[3].author_position | middle |
| authorships[3].raw_author_name | Ibrahim S. Alsukayti |
| authorships[3].is_corresponding | False |
| authorships[3].raw_affiliation_strings | Department of Computer Science, College of Computer, Qassim University, Buraydah 51452, Saudi Arabia |
| authorships[4].author.id | https://openalex.org/A5007714861 |
| authorships[4].author.orcid | https://orcid.org/0000-0001-6567-6413 |
| authorships[4].author.display_name | Mohammed Alsuhaibani |
| authorships[4].countries | SA |
| authorships[4].affiliations[0].institution_ids | https://openalex.org/I156216236 |
| authorships[4].affiliations[0].raw_affiliation_string | Department of Computer Science, College of Computer, Qassim University, Buraydah 51452, Saudi Arabia |
| authorships[4].institutions[0].id | https://openalex.org/I156216236 |
| authorships[4].institutions[0].ror | https://ror.org/01wsfe280 |
| authorships[4].institutions[0].type | education |
| authorships[4].institutions[0].lineage | https://openalex.org/I156216236 |
| authorships[4].institutions[0].country_code | SA |
| authorships[4].institutions[0].display_name | Qassim University |
| authorships[4].author_position | last |
| authorships[4].raw_author_name | Mohammed Alsuhaibani |
| authorships[4].is_corresponding | False |
| authorships[4].raw_affiliation_strings | Department of Computer Science, College of Computer, Qassim University, Buraydah 51452, Saudi Arabia |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411 |
| open_access.oa_status | gold |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Leveraging Graph-Based Representations to Enhance Machine Learning Performance in IIoT Network Security and Attack Detection |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10400 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9990000128746033 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1705 |
| primary_topic.subfield.display_name | Computer Networks and Communications |
| primary_topic.display_name | Network Security and Intrusion Detection |
| related_works | https://openalex.org/W4388920589, https://openalex.org/W3202554610, https://openalex.org/W138569904, https://openalex.org/W102552829, https://openalex.org/W2574115973, https://openalex.org/W2186437798, https://openalex.org/W2363125016, https://openalex.org/W2952736244, https://openalex.org/W4248881655, https://openalex.org/W2952582877 |
| cited_by_count | 11 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 5 |
| counts_by_year[1].year | 2024 |
| counts_by_year[1].cited_by_count | 5 |
| counts_by_year[2].year | 2023 |
| counts_by_year[2].cited_by_count | 1 |
| locations_count | 3 |
| best_oa_location.id | doi:10.3390/app13137774 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210205812 |
| best_oa_location.source.issn | 2076-3417 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2076-3417 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | Applied Sciences |
| best_oa_location.source.host_organization | https://openalex.org/P4310310987 |
| best_oa_location.source.host_organization_name | Multidisciplinary Digital Publishing Institute |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310310987 |
| best_oa_location.source.host_organization_lineage_names | Multidisciplinary Digital Publishing Institute |
| best_oa_location.license | cc-by |
| best_oa_location.pdf_url | https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411 |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Applied Sciences |
| best_oa_location.landing_page_url | https://doi.org/10.3390/app13137774 |
| primary_location.id | doi:10.3390/app13137774 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210205812 |
| primary_location.source.issn | 2076-3417 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2076-3417 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | Applied Sciences |
| primary_location.source.host_organization | https://openalex.org/P4310310987 |
| primary_location.source.host_organization_name | Multidisciplinary Digital Publishing Institute |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310310987 |
| primary_location.source.host_organization_lineage_names | Multidisciplinary Digital Publishing Institute |
| primary_location.license | cc-by |
| primary_location.pdf_url | https://www.mdpi.com/2076-3417/13/13/7774/pdf?version=1688353411 |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | https://openalex.org/licenses/cc-by |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Applied Sciences |
| primary_location.landing_page_url | https://doi.org/10.3390/app13137774 |
| publication_date | 2023-06-30 |
| publication_year | 2023 |
| referenced_works | https://openalex.org/W3006526650, https://openalex.org/W3035366542, https://openalex.org/W3095531713, https://openalex.org/W3108589888, https://openalex.org/W3165101997, https://openalex.org/W3198054520, https://openalex.org/W3191300801, https://openalex.org/W3159151987, https://openalex.org/W3166989303, https://openalex.org/W3014810737, https://openalex.org/W3121022046, https://openalex.org/W3179240416, https://openalex.org/W2969022468, https://openalex.org/W3087344973, https://openalex.org/W3158507034, https://openalex.org/W3157871125, https://openalex.org/W3117906366, https://openalex.org/W3185928824, https://openalex.org/W3091724539, https://openalex.org/W2032280284, https://openalex.org/W3036484052, https://openalex.org/W3208773001, https://openalex.org/W3027095011, https://openalex.org/W3127433831, https://openalex.org/W3174736870, https://openalex.org/W3011561529, https://openalex.org/W3144096578, https://openalex.org/W3000480569, https://openalex.org/W3185681649, https://openalex.org/W3009422166, https://openalex.org/W3133369889, https://openalex.org/W3119918144, https://openalex.org/W3129836451, https://openalex.org/W4323669313, https://openalex.org/W4317103224, https://openalex.org/W4283775720, https://openalex.org/W4237605206, https://openalex.org/W2979560086 |
| referenced_works_count | 38 |
| abstract_inverted_index.a | 62, 97, 135 |
| abstract_inverted_index.In | 0 |
| abstract_inverted_index.We | 60, 109 |
| abstract_inverted_index.in | 48, 85, 134, 138, 165 |
| abstract_inverted_index.is | 23 |
| abstract_inverted_index.of | 6, 24, 34, 51, 54, 81, 130, 141, 161, 170 |
| abstract_inverted_index.to | 11, 42, 77, 176 |
| abstract_inverted_index.we | 91 |
| abstract_inverted_index.Our | 120 |
| abstract_inverted_index.and | 3, 14, 20, 72, 104, 153 |
| abstract_inverted_index.our | 116 |
| abstract_inverted_index.the | 1, 9, 31, 49, 79, 128, 139, 142, 159, 167 |
| abstract_inverted_index.More | 89 |
| abstract_inverted_index.This | 27 |
| abstract_inverted_index.both | 18 |
| abstract_inverted_index.data | 58, 67, 95, 132 |
| abstract_inverted_index.into | 30, 96, 115, 127 |
| abstract_inverted_index.that | 123 |
| abstract_inverted_index.then | 110 |
| abstract_inverted_index.when | 174 |
| abstract_inverted_index.with | 38 |
| abstract_inverted_index.These | 156 |
| abstract_inverted_index.data. | 178 |
| abstract_inverted_index.edges | 105 |
| abstract_inverted_index.graph | 36, 82, 113, 125, 162 |
| abstract_inverted_index.model | 75 |
| abstract_inverted_index.nodes | 101 |
| abstract_inverted_index.realm | 5 |
| abstract_inverted_index.study | 28 |
| abstract_inverted_index.their | 44 |
| abstract_inverted_index.these | 112 |
| abstract_inverted_index.where | 100 |
| abstract_inverted_index.(IIoT) | 56 |
| abstract_inverted_index.assess | 78 |
| abstract_inverted_index.delves | 29 |
| abstract_inverted_index.fusing | 35 |
| abstract_inverted_index.inside | 19 |
| abstract_inverted_index.models | 41 |
| abstract_inverted_index.reveal | 122 |
| abstract_inverted_index.tested | 143 |
| abstract_inverted_index.theory | 37, 83, 126, 163 |
| abstract_inverted_index.things | 55 |
| abstract_inverted_index.vector | 151 |
| abstract_inverted_index.K-means | 154 |
| abstract_inverted_index.ability | 10 |
| abstract_inverted_index.anomaly | 45 |
| abstract_inverted_index.applied | 175 |
| abstract_inverted_index.attacks | 17 |
| abstract_inverted_index.context | 50 |
| abstract_inverted_index.devices | 103 |
| abstract_inverted_index.dynamic | 2 |
| abstract_inverted_index.elevate | 43 |
| abstract_inverted_index.feature | 70 |
| abstract_inverted_index.machine | 39, 73, 117, 144, 171 |
| abstract_inverted_index.models, | 146 |
| abstract_inverted_index.models. | 119 |
| abstract_inverted_index.network | 7, 57, 93, 131, 177 |
| abstract_inverted_index.outside | 21 |
| abstract_inverted_index.results | 133, 157 |
| abstract_inverted_index.support | 150 |
| abstract_inverted_index.traffic | 94 |
| abstract_inverted_index.Internet | 53 |
| abstract_inverted_index.analysis | 129 |
| abstract_inverted_index.classify | 15 |
| abstract_inverted_index.efficacy | 80 |
| abstract_inverted_index.employed | 61 |
| abstract_inverted_index.features | 114 |
| abstract_inverted_index.findings | 121 |
| abstract_inverted_index.identify | 13 |
| abstract_inverted_index.learning | 40, 74, 118, 145, 172 |
| abstract_inverted_index.logistic | 148 |
| abstract_inverted_index.networks | 22 |
| abstract_inverted_index.portscan | 16 |
| abstract_inverted_index.accuracy. | 88 |
| abstract_inverted_index.analysis, | 71 |
| abstract_inverted_index.analysis. | 59 |
| abstract_inverted_index.approach, | 65 |
| abstract_inverted_index.converted | 92 |
| abstract_inverted_index.detection | 46 |
| abstract_inverted_index.improving | 86 |
| abstract_inverted_index.including | 147 |
| abstract_inverted_index.machines, | 152 |
| abstract_inverted_index.paramount | 25 |
| abstract_inverted_index.potential | 33 |
| abstract_inverted_index.represent | 102, 106 |
| abstract_inverted_index.security, | 8 |
| abstract_inverted_index.accurately | 12 |
| abstract_inverted_index.algorithms | 173 |
| abstract_inverted_index.bolstering | 166 |
| abstract_inverted_index.industrial | 52 |
| abstract_inverted_index.instances. | 108 |
| abstract_inverted_index.underscore | 158 |
| abstract_inverted_index.clustering. | 155 |
| abstract_inverted_index.comparison, | 76 |
| abstract_inverted_index.graph-based | 98 |
| abstract_inverted_index.importance. | 26 |
| abstract_inverted_index.improvement | 137 |
| abstract_inverted_index.performance | 140 |
| abstract_inverted_index.regression, | 149 |
| abstract_inverted_index.capabilities | 47, 169 |
| abstract_inverted_index.encompassing | 66 |
| abstract_inverted_index.experimental | 64 |
| abstract_inverted_index.incorporated | 111 |
| abstract_inverted_index.significance | 160 |
| abstract_inverted_index.communication | 107 |
| abstract_inverted_index.comprehensive | 63 |
| abstract_inverted_index.ever-evolving | 4 |
| abstract_inverted_index.incorporating | 124 |
| abstract_inverted_index.specifically, | 90 |
| abstract_inverted_index.underexplored | 32 |
| abstract_inverted_index.classification | 87 |
| abstract_inverted_index.discriminative | 168 |
| abstract_inverted_index.preprocessing, | 68 |
| abstract_inverted_index.representation | 84, 164 |
| abstract_inverted_index.visualization, | 69 |
| abstract_inverted_index.representation, | 99 |
| abstract_inverted_index.modest-yet-meaningful | 136 |
| cited_by_percentile_year.max | 98 |
| cited_by_percentile_year.min | 89 |
| corresponding_author_ids | https://openalex.org/A5043031770 |
| countries_distinct_count | 1 |
| institutions_distinct_count | 5 |
| corresponding_institution_ids | https://openalex.org/I156216236, https://openalex.org/I4210092650 |
| sustainable_development_goals[0].id | https://metadata.un.org/sdg/10 |
| sustainable_development_goals[0].score | 0.6800000071525574 |
| sustainable_development_goals[0].display_name | Reduced inequalities |
| citation_normalized_percentile.value | 0.90185082 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |