Network Forensic Analysis Article Swipe
 YOU?
·
· 2016
· Open Access
·
· DOI: https://doi.org/10.1007/978-1-4471-7299-4_6
YOU?
·
· 2016
· Open Access
·
· DOI: https://doi.org/10.1007/978-1-4471-7299-4_6
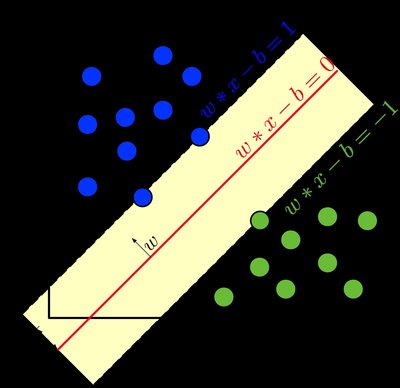
Network forensic analysis is the activity performed by investigators to reconstruct the network activity over a period. The approach is commonly used to investigate individuals suspected of crimes and reconstruct a chain of events during a network-based activity tool. Machine learning is one of the popular approaches used to analyze the network events that adds computer the power to adopt and react according to the situation. These algorithms are used to build models and make predictions based on previous experiences. Michalski et al. (Machine learning: an artificial intelligence approach. Springer Science & Business Media, Berlin, 2013) precisely defined as a computer program is learning from experience E and increasing its performance P. Machine learning algorithms are used widely in data mining, pattern classification, medical fields, and intrusion detection for analyzing network traffic. It can be broadly classified into three categories as supervised, unsupervised, and semi-supervised. Supervised machine learning algorithms are those algorithms which are used to learn patterns from labeled input data sets. These algorithms build classifier model from these inputs and then that model is used to classify unknown labels. Algorithms like naive Bayes, decision tree, SVM, and KNN come under this category. In unsupervised algorithms unlabeled data set is provided for building model, and the data is categorized according to similar properties of same class data and different properties for different class data. These algorithms are also called clustering techniques. Examples of unsupervised machine learning algorithms are DBSCAN, one-class SVM, K-means, etc. Semi-supervised algorithm combines the features of both supervised and unsupervised algorithms. They provide high performance for unlabeled data set.
Related Topics
- Type
- book-chapter
- Language
- en
- Landing Page
- https://doi.org/10.1007/978-1-4471-7299-4_6
- OA Status
- hybrid
- Cited By
- 1
- References
- 40
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W2558000730
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W2558000730Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1007/978-1-4471-7299-4_6Digital Object Identifier
- Title
-
Network Forensic AnalysisWork title
- Type
-
book-chapterOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2016Year of publication
- Publication date
-
2016-01-01Full publication date if available
- Authors
-
R. C. Joshi, Emmanuel S. PilliList of authors in order
- Landing page
-
https://doi.org/10.1007/978-1-4471-7299-4_6Publisher landing page
- Open access
-
YesWhether a free full text is available
- OA status
-
hybridOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.1007/978-1-4471-7299-4_6Direct OA link when available
- Concepts
-
Artificial intelligence, Machine learning, Computer science, Unsupervised learning, Support vector machine, Decision tree, Cluster analysis, Supervised learning, Semi-supervised learning, Naive Bayes classifier, Classifier (UML), One-class classification, Instance-based learning, Data mining, Artificial neural networkTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
1Total citation count in OpenAlex
- Citations by year (recent)
-
2024: 1Per-year citation counts (last 5 years)
- References (count)
-
40Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W2558000730 |
|---|---|
| doi | https://doi.org/10.1007/978-1-4471-7299-4_6 |
| ids.doi | https://doi.org/10.1007/978-1-4471-7299-4_6 |
| ids.mag | 2558000730 |
| ids.openalex | https://openalex.org/W2558000730 |
| fwci | 0.0 |
| type | book-chapter |
| title | Network Forensic Analysis |
| biblio.issue | |
| biblio.volume | |
| biblio.last_page | 129 |
| biblio.first_page | 107 |
| topics[0].id | https://openalex.org/T10400 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9998999834060669 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1705 |
| topics[0].subfield.display_name | Computer Networks and Communications |
| topics[0].display_name | Network Security and Intrusion Detection |
| topics[1].id | https://openalex.org/T11241 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9986000061035156 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1711 |
| topics[1].subfield.display_name | Signal Processing |
| topics[1].display_name | Advanced Malware Detection Techniques |
| topics[2].id | https://openalex.org/T11512 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9986000061035156 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1702 |
| topics[2].subfield.display_name | Artificial Intelligence |
| topics[2].display_name | Anomaly Detection Techniques and Applications |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C154945302 |
| concepts[0].level | 1 |
| concepts[0].score | 0.7773353457450867 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[0].display_name | Artificial intelligence |
| concepts[1].id | https://openalex.org/C119857082 |
| concepts[1].level | 1 |
| concepts[1].score | 0.7706810832023621 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q2539 |
| concepts[1].display_name | Machine learning |
| concepts[2].id | https://openalex.org/C41008148 |
| concepts[2].level | 0 |
| concepts[2].score | 0.7539136409759521 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[2].display_name | Computer science |
| concepts[3].id | https://openalex.org/C8038995 |
| concepts[3].level | 2 |
| concepts[3].score | 0.5977007150650024 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q1152135 |
| concepts[3].display_name | Unsupervised learning |
| concepts[4].id | https://openalex.org/C12267149 |
| concepts[4].level | 2 |
| concepts[4].score | 0.5221936106681824 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q282453 |
| concepts[4].display_name | Support vector machine |
| concepts[5].id | https://openalex.org/C84525736 |
| concepts[5].level | 2 |
| concepts[5].score | 0.49396711587905884 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q831366 |
| concepts[5].display_name | Decision tree |
| concepts[6].id | https://openalex.org/C73555534 |
| concepts[6].level | 2 |
| concepts[6].score | 0.4932693839073181 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q622825 |
| concepts[6].display_name | Cluster analysis |
| concepts[7].id | https://openalex.org/C136389625 |
| concepts[7].level | 3 |
| concepts[7].score | 0.4859422445297241 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q334384 |
| concepts[7].display_name | Supervised learning |
| concepts[8].id | https://openalex.org/C58973888 |
| concepts[8].level | 2 |
| concepts[8].score | 0.47300201654434204 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q1041418 |
| concepts[8].display_name | Semi-supervised learning |
| concepts[9].id | https://openalex.org/C52001869 |
| concepts[9].level | 3 |
| concepts[9].score | 0.4328461289405823 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q812530 |
| concepts[9].display_name | Naive Bayes classifier |
| concepts[10].id | https://openalex.org/C95623464 |
| concepts[10].level | 2 |
| concepts[10].score | 0.4299563765525818 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q1096149 |
| concepts[10].display_name | Classifier (UML) |
| concepts[11].id | https://openalex.org/C34872919 |
| concepts[11].level | 3 |
| concepts[11].score | 0.4236806333065033 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q7092302 |
| concepts[11].display_name | One-class classification |
| concepts[12].id | https://openalex.org/C24138899 |
| concepts[12].level | 3 |
| concepts[12].score | 0.41312867403030396 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q17141258 |
| concepts[12].display_name | Instance-based learning |
| concepts[13].id | https://openalex.org/C124101348 |
| concepts[13].level | 1 |
| concepts[13].score | 0.3884737193584442 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q172491 |
| concepts[13].display_name | Data mining |
| concepts[14].id | https://openalex.org/C50644808 |
| concepts[14].level | 2 |
| concepts[14].score | 0.36651337146759033 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q192776 |
| concepts[14].display_name | Artificial neural network |
| keywords[0].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[0].score | 0.7773353457450867 |
| keywords[0].display_name | Artificial intelligence |
| keywords[1].id | https://openalex.org/keywords/machine-learning |
| keywords[1].score | 0.7706810832023621 |
| keywords[1].display_name | Machine learning |
| keywords[2].id | https://openalex.org/keywords/computer-science |
| keywords[2].score | 0.7539136409759521 |
| keywords[2].display_name | Computer science |
| keywords[3].id | https://openalex.org/keywords/unsupervised-learning |
| keywords[3].score | 0.5977007150650024 |
| keywords[3].display_name | Unsupervised learning |
| keywords[4].id | https://openalex.org/keywords/support-vector-machine |
| keywords[4].score | 0.5221936106681824 |
| keywords[4].display_name | Support vector machine |
| keywords[5].id | https://openalex.org/keywords/decision-tree |
| keywords[5].score | 0.49396711587905884 |
| keywords[5].display_name | Decision tree |
| keywords[6].id | https://openalex.org/keywords/cluster-analysis |
| keywords[6].score | 0.4932693839073181 |
| keywords[6].display_name | Cluster analysis |
| keywords[7].id | https://openalex.org/keywords/supervised-learning |
| keywords[7].score | 0.4859422445297241 |
| keywords[7].display_name | Supervised learning |
| keywords[8].id | https://openalex.org/keywords/semi-supervised-learning |
| keywords[8].score | 0.47300201654434204 |
| keywords[8].display_name | Semi-supervised learning |
| keywords[9].id | https://openalex.org/keywords/naive-bayes-classifier |
| keywords[9].score | 0.4328461289405823 |
| keywords[9].display_name | Naive Bayes classifier |
| keywords[10].id | https://openalex.org/keywords/classifier |
| keywords[10].score | 0.4299563765525818 |
| keywords[10].display_name | Classifier (UML) |
| keywords[11].id | https://openalex.org/keywords/one-class-classification |
| keywords[11].score | 0.4236806333065033 |
| keywords[11].display_name | One-class classification |
| keywords[12].id | https://openalex.org/keywords/instance-based-learning |
| keywords[12].score | 0.41312867403030396 |
| keywords[12].display_name | Instance-based learning |
| keywords[13].id | https://openalex.org/keywords/data-mining |
| keywords[13].score | 0.3884737193584442 |
| keywords[13].display_name | Data mining |
| keywords[14].id | https://openalex.org/keywords/artificial-neural-network |
| keywords[14].score | 0.36651337146759033 |
| keywords[14].display_name | Artificial neural network |
| language | en |
| locations[0].id | doi:10.1007/978-1-4471-7299-4_6 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210175725 |
| locations[0].source.issn | 1617-7975, 2197-8433 |
| locations[0].source.type | book series |
| locations[0].source.is_oa | False |
| locations[0].source.issn_l | 1617-7975 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | Computer communications and networks |
| locations[0].source.host_organization | |
| locations[0].source.host_organization_name | |
| locations[0].license | cc-by-nc |
| locations[0].pdf_url | |
| locations[0].version | publishedVersion |
| locations[0].raw_type | book-chapter |
| locations[0].license_id | https://openalex.org/licenses/cc-by-nc |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | Computer Communications and Networks |
| locations[0].landing_page_url | https://doi.org/10.1007/978-1-4471-7299-4_6 |
| indexed_in | crossref |
| authorships[0].author.id | https://openalex.org/A5101884639 |
| authorships[0].author.orcid | https://orcid.org/0000-0001-9612-2691 |
| authorships[0].author.display_name | R. C. Joshi |
| authorships[0].countries | IN |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I60054993 |
| authorships[0].affiliations[0].raw_affiliation_string | Graphic Era University, Dehradun, India |
| authorships[0].institutions[0].id | https://openalex.org/I60054993 |
| authorships[0].institutions[0].ror | https://ror.org/03wqgqd89 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I60054993 |
| authorships[0].institutions[0].country_code | IN |
| authorships[0].institutions[0].display_name | Graphic Era University |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | R. C. Joshi |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Graphic Era University, Dehradun, India |
| authorships[1].author.id | https://openalex.org/A5040360984 |
| authorships[1].author.orcid | https://orcid.org/0000-0002-6056-1147 |
| authorships[1].author.display_name | Emmanuel S. Pilli |
| authorships[1].countries | IN |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I83205935 |
| authorships[1].affiliations[0].raw_affiliation_string | Malaviya National Institute of Technology, Jaipur, India |
| authorships[1].institutions[0].id | https://openalex.org/I83205935 |
| authorships[1].institutions[0].ror | https://ror.org/0077k1j32 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I83205935 |
| authorships[1].institutions[0].country_code | IN |
| authorships[1].institutions[0].display_name | Malaviya National Institute of Technology Jaipur |
| authorships[1].author_position | last |
| authorships[1].raw_author_name | Emmanuel S. Pilli |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Malaviya National Institute of Technology, Jaipur, India |
| has_content.pdf | False |
| has_content.grobid_xml | False |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.1007/978-1-4471-7299-4_6 |
| open_access.oa_status | hybrid |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Network Forensic Analysis |
| has_fulltext | False |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10400 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9998999834060669 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1705 |
| primary_topic.subfield.display_name | Computer Networks and Communications |
| primary_topic.display_name | Network Security and Intrusion Detection |
| related_works | https://openalex.org/W3148060700, https://openalex.org/W2794908468, https://openalex.org/W2531570999, https://openalex.org/W2098239572, https://openalex.org/W2042184006, https://openalex.org/W4319302697, https://openalex.org/W2921630034, https://openalex.org/W2621411691, https://openalex.org/W3210156800, https://openalex.org/W4310801741 |
| cited_by_count | 1 |
| counts_by_year[0].year | 2024 |
| counts_by_year[0].cited_by_count | 1 |
| locations_count | 1 |
| best_oa_location.id | doi:10.1007/978-1-4471-7299-4_6 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210175725 |
| best_oa_location.source.issn | 1617-7975, 2197-8433 |
| best_oa_location.source.type | book series |
| best_oa_location.source.is_oa | False |
| best_oa_location.source.issn_l | 1617-7975 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | Computer communications and networks |
| best_oa_location.source.host_organization | |
| best_oa_location.source.host_organization_name | |
| best_oa_location.license | cc-by-nc |
| best_oa_location.pdf_url | |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | book-chapter |
| best_oa_location.license_id | https://openalex.org/licenses/cc-by-nc |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | Computer Communications and Networks |
| best_oa_location.landing_page_url | https://doi.org/10.1007/978-1-4471-7299-4_6 |
| primary_location.id | doi:10.1007/978-1-4471-7299-4_6 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210175725 |
| primary_location.source.issn | 1617-7975, 2197-8433 |
| primary_location.source.type | book series |
| primary_location.source.is_oa | False |
| primary_location.source.issn_l | 1617-7975 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | Computer communications and networks |
| primary_location.source.host_organization | |
| primary_location.source.host_organization_name | |
| primary_location.license | cc-by-nc |
| primary_location.pdf_url | |
| primary_location.version | publishedVersion |
| primary_location.raw_type | book-chapter |
| primary_location.license_id | https://openalex.org/licenses/cc-by-nc |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | Computer Communications and Networks |
| primary_location.landing_page_url | https://doi.org/10.1007/978-1-4471-7299-4_6 |
| publication_date | 2016-01-01 |
| publication_year | 2016 |
| referenced_works | https://openalex.org/W2101109743, https://openalex.org/W2084496302, https://openalex.org/W2169768310, https://openalex.org/W2002304261, https://openalex.org/W2606796776, https://openalex.org/W2105819382, https://openalex.org/W2016070752, https://openalex.org/W4256561644, https://openalex.org/W4256647193, https://openalex.org/W1977838479, https://openalex.org/W2017380649, https://openalex.org/W4256177618, https://openalex.org/W1988180775, https://openalex.org/W4239510810, https://openalex.org/W2120617515, https://openalex.org/W4206139345, https://openalex.org/W2043914017, https://openalex.org/W2142827986, https://openalex.org/W2081395750, https://openalex.org/W2331979113, https://openalex.org/W1673310716, https://openalex.org/W2148603752, https://openalex.org/W2119821739, https://openalex.org/W2015401436, https://openalex.org/W2110106247, https://openalex.org/W4230674625, https://openalex.org/W2156909104, https://openalex.org/W2802348331, https://openalex.org/W15008180, https://openalex.org/W4240728089, https://openalex.org/W2130676130, https://openalex.org/W1967320885, https://openalex.org/W1988833430, https://openalex.org/W2141409867, https://openalex.org/W2913593077, https://openalex.org/W1826109706, https://openalex.org/W1484413656, https://openalex.org/W2117646649, https://openalex.org/W2125283600, https://openalex.org/W1596324102 |
| referenced_works_count | 40 |
| abstract_inverted_index.& | 91 |
| abstract_inverted_index.E | 106 |
| abstract_inverted_index.a | 15, 30, 35, 99 |
| abstract_inverted_index.In | 194 |
| abstract_inverted_index.It | 132 |
| abstract_inverted_index.P. | 111 |
| abstract_inverted_index.an | 85 |
| abstract_inverted_index.as | 98, 140 |
| abstract_inverted_index.be | 134 |
| abstract_inverted_index.by | 7 |
| abstract_inverted_index.et | 81 |
| abstract_inverted_index.in | 118 |
| abstract_inverted_index.is | 3, 19, 41, 102, 175, 200, 208 |
| abstract_inverted_index.of | 26, 32, 43, 214, 233, 249 |
| abstract_inverted_index.on | 77 |
| abstract_inverted_index.to | 9, 22, 48, 58, 63, 70, 155, 177, 211 |
| abstract_inverted_index.KNN | 189 |
| abstract_inverted_index.The | 17 |
| abstract_inverted_index.al. | 82 |
| abstract_inverted_index.and | 28, 60, 73, 107, 125, 143, 171, 188, 205, 218, 252 |
| abstract_inverted_index.are | 68, 115, 149, 153, 227, 238 |
| abstract_inverted_index.can | 133 |
| abstract_inverted_index.for | 128, 202, 221, 259 |
| abstract_inverted_index.its | 109 |
| abstract_inverted_index.one | 42 |
| abstract_inverted_index.set | 199 |
| abstract_inverted_index.the | 4, 11, 44, 50, 56, 64, 206, 247 |
| abstract_inverted_index.SVM, | 187, 241 |
| abstract_inverted_index.They | 255 |
| abstract_inverted_index.adds | 54 |
| abstract_inverted_index.also | 228 |
| abstract_inverted_index.both | 250 |
| abstract_inverted_index.come | 190 |
| abstract_inverted_index.data | 119, 161, 198, 207, 217, 261 |
| abstract_inverted_index.etc. | 243 |
| abstract_inverted_index.from | 104, 158, 168 |
| abstract_inverted_index.high | 257 |
| abstract_inverted_index.into | 137 |
| abstract_inverted_index.like | 182 |
| abstract_inverted_index.make | 74 |
| abstract_inverted_index.over | 14 |
| abstract_inverted_index.same | 215 |
| abstract_inverted_index.set. | 262 |
| abstract_inverted_index.that | 53, 173 |
| abstract_inverted_index.then | 172 |
| abstract_inverted_index.this | 192 |
| abstract_inverted_index.used | 21, 47, 69, 116, 154, 176 |
| abstract_inverted_index.2013) | 95 |
| abstract_inverted_index.These | 66, 163, 225 |
| abstract_inverted_index.adopt | 59 |
| abstract_inverted_index.based | 76 |
| abstract_inverted_index.build | 71, 165 |
| abstract_inverted_index.chain | 31 |
| abstract_inverted_index.class | 216, 223 |
| abstract_inverted_index.data. | 224 |
| abstract_inverted_index.input | 160 |
| abstract_inverted_index.learn | 156 |
| abstract_inverted_index.model | 167, 174 |
| abstract_inverted_index.naive | 183 |
| abstract_inverted_index.power | 57 |
| abstract_inverted_index.react | 61 |
| abstract_inverted_index.sets. | 162 |
| abstract_inverted_index.these | 169 |
| abstract_inverted_index.those | 150 |
| abstract_inverted_index.three | 138 |
| abstract_inverted_index.tool. | 38 |
| abstract_inverted_index.tree, | 186 |
| abstract_inverted_index.under | 191 |
| abstract_inverted_index.which | 152 |
| abstract_inverted_index.Bayes, | 184 |
| abstract_inverted_index.Media, | 93 |
| abstract_inverted_index.called | 229 |
| abstract_inverted_index.crimes | 27 |
| abstract_inverted_index.during | 34 |
| abstract_inverted_index.events | 33, 52 |
| abstract_inverted_index.inputs | 170 |
| abstract_inverted_index.model, | 204 |
| abstract_inverted_index.models | 72 |
| abstract_inverted_index.widely | 117 |
| abstract_inverted_index.Berlin, | 94 |
| abstract_inverted_index.DBSCAN, | 239 |
| abstract_inverted_index.Machine | 39, 112 |
| abstract_inverted_index.Network | 0 |
| abstract_inverted_index.Science | 90 |
| abstract_inverted_index.analyze | 49 |
| abstract_inverted_index.broadly | 135 |
| abstract_inverted_index.defined | 97 |
| abstract_inverted_index.fields, | 124 |
| abstract_inverted_index.labeled | 159 |
| abstract_inverted_index.labels. | 180 |
| abstract_inverted_index.machine | 146, 235 |
| abstract_inverted_index.medical | 123 |
| abstract_inverted_index.mining, | 120 |
| abstract_inverted_index.network | 12, 51, 130 |
| abstract_inverted_index.pattern | 121 |
| abstract_inverted_index.period. | 16 |
| abstract_inverted_index.popular | 45 |
| abstract_inverted_index.program | 101 |
| abstract_inverted_index.provide | 256 |
| abstract_inverted_index.similar | 212 |
| abstract_inverted_index.unknown | 179 |
| abstract_inverted_index.(Machine | 83 |
| abstract_inverted_index.Business | 92 |
| abstract_inverted_index.Examples | 232 |
| abstract_inverted_index.K-means, | 242 |
| abstract_inverted_index.Springer | 89 |
| abstract_inverted_index.activity | 5, 13, 37 |
| abstract_inverted_index.analysis | 2 |
| abstract_inverted_index.approach | 18 |
| abstract_inverted_index.building | 203 |
| abstract_inverted_index.classify | 178 |
| abstract_inverted_index.combines | 246 |
| abstract_inverted_index.commonly | 20 |
| abstract_inverted_index.computer | 55, 100 |
| abstract_inverted_index.decision | 185 |
| abstract_inverted_index.features | 248 |
| abstract_inverted_index.forensic | 1 |
| abstract_inverted_index.learning | 40, 103, 113, 147, 236 |
| abstract_inverted_index.patterns | 157 |
| abstract_inverted_index.previous | 78 |
| abstract_inverted_index.provided | 201 |
| abstract_inverted_index.traffic. | 131 |
| abstract_inverted_index.Michalski | 80 |
| abstract_inverted_index.according | 62, 210 |
| abstract_inverted_index.algorithm | 245 |
| abstract_inverted_index.analyzing | 129 |
| abstract_inverted_index.approach. | 88 |
| abstract_inverted_index.category. | 193 |
| abstract_inverted_index.detection | 127 |
| abstract_inverted_index.different | 219, 222 |
| abstract_inverted_index.intrusion | 126 |
| abstract_inverted_index.learning: | 84 |
| abstract_inverted_index.one-class | 240 |
| abstract_inverted_index.performed | 6 |
| abstract_inverted_index.precisely | 96 |
| abstract_inverted_index.suspected | 25 |
| abstract_inverted_index.unlabeled | 197, 260 |
| abstract_inverted_index.Algorithms | 181 |
| abstract_inverted_index.Supervised | 145 |
| abstract_inverted_index.algorithms | 67, 114, 148, 151, 164, 196, 226, 237 |
| abstract_inverted_index.approaches | 46 |
| abstract_inverted_index.artificial | 86 |
| abstract_inverted_index.categories | 139 |
| abstract_inverted_index.classified | 136 |
| abstract_inverted_index.classifier | 166 |
| abstract_inverted_index.clustering | 230 |
| abstract_inverted_index.experience | 105 |
| abstract_inverted_index.increasing | 108 |
| abstract_inverted_index.properties | 213, 220 |
| abstract_inverted_index.situation. | 65 |
| abstract_inverted_index.supervised | 251 |
| abstract_inverted_index.algorithms. | 254 |
| abstract_inverted_index.categorized | 209 |
| abstract_inverted_index.individuals | 24 |
| abstract_inverted_index.investigate | 23 |
| abstract_inverted_index.performance | 110, 258 |
| abstract_inverted_index.predictions | 75 |
| abstract_inverted_index.reconstruct | 10, 29 |
| abstract_inverted_index.supervised, | 141 |
| abstract_inverted_index.techniques. | 231 |
| abstract_inverted_index.experiences. | 79 |
| abstract_inverted_index.intelligence | 87 |
| abstract_inverted_index.unsupervised | 195, 234, 253 |
| abstract_inverted_index.investigators | 8 |
| abstract_inverted_index.network-based | 36 |
| abstract_inverted_index.unsupervised, | 142 |
| abstract_inverted_index.Semi-supervised | 244 |
| abstract_inverted_index.classification, | 122 |
| abstract_inverted_index.semi-supervised. | 144 |
| cited_by_percentile_year.max | 94 |
| cited_by_percentile_year.min | 90 |
| countries_distinct_count | 1 |
| institutions_distinct_count | 2 |
| sustainable_development_goals[0].id | https://metadata.un.org/sdg/16 |
| sustainable_development_goals[0].score | 0.7699999809265137 |
| sustainable_development_goals[0].display_name | Peace, Justice and strong institutions |
| citation_normalized_percentile.value | 0.30113636 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |