Online Banking User Authentication Methods: A Systematic Literature Review Article Swipe
 YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.1109/access.2023.3346045
YOU?
·
· 2023
· Open Access
·
· DOI: https://doi.org/10.1109/access.2023.3346045
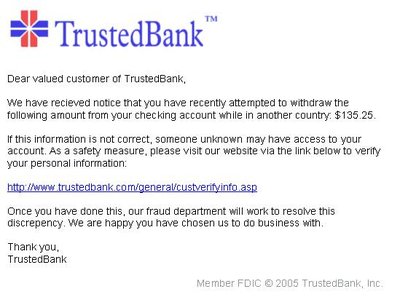
Online banking has become increasingly popular in recent years, making it a target for cyberattacks. Banks have implemented various user authentication methods to protect their customers’ online accounts. This paper reviews the state-of-the-art user authentication methods used in online banking and potential cyber threats. This paper starts by exploring different user authentication methods, such as knowledge-based authentication (KBA), biometrics-based authentication (BBA), possession-based authentication (PBA), and other methods. The advantages and disadvantages of each user authentication method are then discussed. Furthermore, the paper discusses the various cyber threats that can compromise user authentication for online banking systems, such as malware attacks, social engineering, phishing attacks, man-in-the-middle (MiTM) attacks, denial of service (DoS) attacks, session hijacking, weak passwords, keyloggers, SQL injection, and replay attacks. Also, the paper explores the user authentication methods used by popular banks, which can provide insights into best practices for safeguarding online banking accounts and future user authentication methods in online banking and cyber threats. It states that the increasing use of BBA, two-factor authentication (2FA), and multi-factor authentication (MFA) will help improve the security of online banking systems. However, the paper also warns that new cyber challenges will emerge, and banks need to be vigilant in protecting their customers’ online banking accounts.
Related Topics
- Type
- article
- Language
- en
- Landing Page
- https://doi.org/10.1109/access.2023.3346045
- https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdf
- OA Status
- gold
- Cited By
- 23
- References
- 139
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W4390120028
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W4390120028Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.1109/access.2023.3346045Digital Object Identifier
- Title
-
Online Banking User Authentication Methods: A Systematic Literature ReviewWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2023Year of publication
- Publication date
-
2023-12-22Full publication date if available
- Authors
-
Nader Abdel Karim, Osama A. Khashan, Hasan Kanaker, Waleed K. Abdulraheem, Mohammad Alshinwan, Abedal-Kareem Al-BannaList of authors in order
- Landing page
-
https://doi.org/10.1109/access.2023.3346045Publisher landing page
- PDF URL
-
https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdfDirect link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
goldOpen access status per OpenAlex
- OA URL
-
https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdfDirect OA link when available
- Concepts
-
Phishing, Computer security, Multi-factor authentication, Computer science, Chip Authentication Program, Authentication (law), Challenge-Handshake Authentication Protocol, Authentication protocol, Email authentication, Password, Denial-of-service attack, Lightweight Extensible Authentication Protocol, Challenge–response authentication, Generic Bootstrapping Architecture, Session (web analytics), Identity theft, Man-in-the-middle attack, Botnet, Mobile banking, Internet privacy, The Internet, World Wide WebTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
23Total citation count in OpenAlex
- Citations by year (recent)
-
2025: 17, 2024: 6Per-year citation counts (last 5 years)
- References (count)
-
139Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W4390120028 |
|---|---|
| doi | https://doi.org/10.1109/access.2023.3346045 |
| ids.doi | https://doi.org/10.1109/access.2023.3346045 |
| ids.openalex | https://openalex.org/W4390120028 |
| fwci | 14.22521542 |
| type | article |
| title | Online Banking User Authentication Methods: A Systematic Literature Review |
| biblio.issue | |
| biblio.volume | 12 |
| biblio.last_page | 757 |
| biblio.first_page | 741 |
| topics[0].id | https://openalex.org/T11800 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 0.9997000098228455 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1710 |
| topics[0].subfield.display_name | Information Systems |
| topics[0].display_name | User Authentication and Security Systems |
| topics[1].id | https://openalex.org/T11644 |
| topics[1].field.id | https://openalex.org/fields/17 |
| topics[1].field.display_name | Computer Science |
| topics[1].score | 0.9987999796867371 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/1710 |
| topics[1].subfield.display_name | Information Systems |
| topics[1].display_name | Spam and Phishing Detection |
| topics[2].id | https://openalex.org/T11045 |
| topics[2].field.id | https://openalex.org/fields/33 |
| topics[2].field.display_name | Social Sciences |
| topics[2].score | 0.994700014591217 |
| topics[2].domain.id | https://openalex.org/domains/2 |
| topics[2].domain.display_name | Social Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/3312 |
| topics[2].subfield.display_name | Sociology and Political Science |
| topics[2].display_name | Privacy, Security, and Data Protection |
| is_xpac | False |
| apc_list.value | 1850 |
| apc_list.currency | USD |
| apc_list.value_usd | 1850 |
| apc_paid.value | 1850 |
| apc_paid.currency | USD |
| apc_paid.value_usd | 1850 |
| concepts[0].id | https://openalex.org/C83860907 |
| concepts[0].level | 3 |
| concepts[0].score | 0.7697000503540039 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q135005 |
| concepts[0].display_name | Phishing |
| concepts[1].id | https://openalex.org/C38652104 |
| concepts[1].level | 1 |
| concepts[1].score | 0.7547808885574341 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q3510521 |
| concepts[1].display_name | Computer security |
| concepts[2].id | https://openalex.org/C194699767 |
| concepts[2].level | 4 |
| concepts[2].score | 0.7471520900726318 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q7878662 |
| concepts[2].display_name | Multi-factor authentication |
| concepts[3].id | https://openalex.org/C41008148 |
| concepts[3].level | 0 |
| concepts[3].score | 0.7165207266807556 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[3].display_name | Computer science |
| concepts[4].id | https://openalex.org/C142124187 |
| concepts[4].level | 5 |
| concepts[4].score | 0.6904182434082031 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q5101471 |
| concepts[4].display_name | Chip Authentication Program |
| concepts[5].id | https://openalex.org/C148417208 |
| concepts[5].level | 2 |
| concepts[5].score | 0.6382116675376892 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q4825882 |
| concepts[5].display_name | Authentication (law) |
| concepts[6].id | https://openalex.org/C207828512 |
| concepts[6].level | 4 |
| concepts[6].score | 0.5639559030532837 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q1060131 |
| concepts[6].display_name | Challenge-Handshake Authentication Protocol |
| concepts[7].id | https://openalex.org/C21564112 |
| concepts[7].level | 3 |
| concepts[7].score | 0.5448333024978638 |
| concepts[7].wikidata | https://www.wikidata.org/wiki/Q4825885 |
| concepts[7].display_name | Authentication protocol |
| concepts[8].id | https://openalex.org/C550791530 |
| concepts[8].level | 5 |
| concepts[8].score | 0.5420329570770264 |
| concepts[8].wikidata | https://www.wikidata.org/wiki/Q5368811 |
| concepts[8].display_name | Email authentication |
| concepts[9].id | https://openalex.org/C109297577 |
| concepts[9].level | 2 |
| concepts[9].score | 0.5341697335243225 |
| concepts[9].wikidata | https://www.wikidata.org/wiki/Q161157 |
| concepts[9].display_name | Password |
| concepts[10].id | https://openalex.org/C38822068 |
| concepts[10].level | 3 |
| concepts[10].score | 0.4875571131706238 |
| concepts[10].wikidata | https://www.wikidata.org/wiki/Q131406 |
| concepts[10].display_name | Denial-of-service attack |
| concepts[11].id | https://openalex.org/C167169670 |
| concepts[11].level | 4 |
| concepts[11].score | 0.4825981855392456 |
| concepts[11].wikidata | https://www.wikidata.org/wiki/Q1824705 |
| concepts[11].display_name | Lightweight Extensible Authentication Protocol |
| concepts[12].id | https://openalex.org/C131129157 |
| concepts[12].level | 4 |
| concepts[12].score | 0.48108288645744324 |
| concepts[12].wikidata | https://www.wikidata.org/wiki/Q1059963 |
| concepts[12].display_name | Challenge–response authentication |
| concepts[13].id | https://openalex.org/C174953433 |
| concepts[13].level | 5 |
| concepts[13].score | 0.4786989986896515 |
| concepts[13].wikidata | https://www.wikidata.org/wiki/Q5532650 |
| concepts[13].display_name | Generic Bootstrapping Architecture |
| concepts[14].id | https://openalex.org/C2779182362 |
| concepts[14].level | 2 |
| concepts[14].score | 0.4630129039287567 |
| concepts[14].wikidata | https://www.wikidata.org/wiki/Q17126187 |
| concepts[14].display_name | Session (web analytics) |
| concepts[15].id | https://openalex.org/C522325796 |
| concepts[15].level | 2 |
| concepts[15].score | 0.45470839738845825 |
| concepts[15].wikidata | https://www.wikidata.org/wiki/Q471880 |
| concepts[15].display_name | Identity theft |
| concepts[16].id | https://openalex.org/C196491621 |
| concepts[16].level | 3 |
| concepts[16].score | 0.44766801595687866 |
| concepts[16].wikidata | https://www.wikidata.org/wiki/Q554830 |
| concepts[16].display_name | Man-in-the-middle attack |
| concepts[17].id | https://openalex.org/C22735295 |
| concepts[17].level | 3 |
| concepts[17].score | 0.4423671364784241 |
| concepts[17].wikidata | https://www.wikidata.org/wiki/Q317671 |
| concepts[17].display_name | Botnet |
| concepts[18].id | https://openalex.org/C2775930393 |
| concepts[18].level | 2 |
| concepts[18].score | 0.44233325123786926 |
| concepts[18].wikidata | https://www.wikidata.org/wiki/Q1941439 |
| concepts[18].display_name | Mobile banking |
| concepts[19].id | https://openalex.org/C108827166 |
| concepts[19].level | 1 |
| concepts[19].score | 0.4133955240249634 |
| concepts[19].wikidata | https://www.wikidata.org/wiki/Q175975 |
| concepts[19].display_name | Internet privacy |
| concepts[20].id | https://openalex.org/C110875604 |
| concepts[20].level | 2 |
| concepts[20].score | 0.24850159883499146 |
| concepts[20].wikidata | https://www.wikidata.org/wiki/Q75 |
| concepts[20].display_name | The Internet |
| concepts[21].id | https://openalex.org/C136764020 |
| concepts[21].level | 1 |
| concepts[21].score | 0.24588608741760254 |
| concepts[21].wikidata | https://www.wikidata.org/wiki/Q466 |
| concepts[21].display_name | World Wide Web |
| keywords[0].id | https://openalex.org/keywords/phishing |
| keywords[0].score | 0.7697000503540039 |
| keywords[0].display_name | Phishing |
| keywords[1].id | https://openalex.org/keywords/computer-security |
| keywords[1].score | 0.7547808885574341 |
| keywords[1].display_name | Computer security |
| keywords[2].id | https://openalex.org/keywords/multi-factor-authentication |
| keywords[2].score | 0.7471520900726318 |
| keywords[2].display_name | Multi-factor authentication |
| keywords[3].id | https://openalex.org/keywords/computer-science |
| keywords[3].score | 0.7165207266807556 |
| keywords[3].display_name | Computer science |
| keywords[4].id | https://openalex.org/keywords/chip-authentication-program |
| keywords[4].score | 0.6904182434082031 |
| keywords[4].display_name | Chip Authentication Program |
| keywords[5].id | https://openalex.org/keywords/authentication |
| keywords[5].score | 0.6382116675376892 |
| keywords[5].display_name | Authentication (law) |
| keywords[6].id | https://openalex.org/keywords/challenge-handshake-authentication-protocol |
| keywords[6].score | 0.5639559030532837 |
| keywords[6].display_name | Challenge-Handshake Authentication Protocol |
| keywords[7].id | https://openalex.org/keywords/authentication-protocol |
| keywords[7].score | 0.5448333024978638 |
| keywords[7].display_name | Authentication protocol |
| keywords[8].id | https://openalex.org/keywords/email-authentication |
| keywords[8].score | 0.5420329570770264 |
| keywords[8].display_name | Email authentication |
| keywords[9].id | https://openalex.org/keywords/password |
| keywords[9].score | 0.5341697335243225 |
| keywords[9].display_name | Password |
| keywords[10].id | https://openalex.org/keywords/denial-of-service-attack |
| keywords[10].score | 0.4875571131706238 |
| keywords[10].display_name | Denial-of-service attack |
| keywords[11].id | https://openalex.org/keywords/lightweight-extensible-authentication-protocol |
| keywords[11].score | 0.4825981855392456 |
| keywords[11].display_name | Lightweight Extensible Authentication Protocol |
| keywords[12].id | https://openalex.org/keywords/challenge–response-authentication |
| keywords[12].score | 0.48108288645744324 |
| keywords[12].display_name | Challenge–response authentication |
| keywords[13].id | https://openalex.org/keywords/generic-bootstrapping-architecture |
| keywords[13].score | 0.4786989986896515 |
| keywords[13].display_name | Generic Bootstrapping Architecture |
| keywords[14].id | https://openalex.org/keywords/session |
| keywords[14].score | 0.4630129039287567 |
| keywords[14].display_name | Session (web analytics) |
| keywords[15].id | https://openalex.org/keywords/identity-theft |
| keywords[15].score | 0.45470839738845825 |
| keywords[15].display_name | Identity theft |
| keywords[16].id | https://openalex.org/keywords/man-in-the-middle-attack |
| keywords[16].score | 0.44766801595687866 |
| keywords[16].display_name | Man-in-the-middle attack |
| keywords[17].id | https://openalex.org/keywords/botnet |
| keywords[17].score | 0.4423671364784241 |
| keywords[17].display_name | Botnet |
| keywords[18].id | https://openalex.org/keywords/mobile-banking |
| keywords[18].score | 0.44233325123786926 |
| keywords[18].display_name | Mobile banking |
| keywords[19].id | https://openalex.org/keywords/internet-privacy |
| keywords[19].score | 0.4133955240249634 |
| keywords[19].display_name | Internet privacy |
| keywords[20].id | https://openalex.org/keywords/the-internet |
| keywords[20].score | 0.24850159883499146 |
| keywords[20].display_name | The Internet |
| keywords[21].id | https://openalex.org/keywords/world-wide-web |
| keywords[21].score | 0.24588608741760254 |
| keywords[21].display_name | World Wide Web |
| language | en |
| locations[0].id | doi:10.1109/access.2023.3346045 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S2485537415 |
| locations[0].source.issn | 2169-3536 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | True |
| locations[0].source.issn_l | 2169-3536 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | True |
| locations[0].source.display_name | IEEE Access |
| locations[0].source.host_organization | https://openalex.org/P4310319808 |
| locations[0].source.host_organization_name | Institute of Electrical and Electronics Engineers |
| locations[0].source.host_organization_lineage | https://openalex.org/P4310319808 |
| locations[0].license | |
| locations[0].pdf_url | https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdf |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | IEEE Access |
| locations[0].landing_page_url | https://doi.org/10.1109/access.2023.3346045 |
| locations[1].id | pmh:oai:doaj.org/article:93ec896433ad409aa555dc70113761fa |
| locations[1].is_oa | False |
| locations[1].source.id | https://openalex.org/S4306401280 |
| locations[1].source.issn | |
| locations[1].source.type | repository |
| locations[1].source.is_oa | False |
| locations[1].source.issn_l | |
| locations[1].source.is_core | False |
| locations[1].source.is_in_doaj | False |
| locations[1].source.display_name | DOAJ (DOAJ: Directory of Open Access Journals) |
| locations[1].source.host_organization | |
| locations[1].source.host_organization_name | |
| locations[1].source.host_organization_lineage | |
| locations[1].license | |
| locations[1].pdf_url | |
| locations[1].version | submittedVersion |
| locations[1].raw_type | article |
| locations[1].license_id | |
| locations[1].is_accepted | False |
| locations[1].is_published | False |
| locations[1].raw_source_name | IEEE Access, Vol 12, Pp 741-757 (2024) |
| locations[1].landing_page_url | https://doaj.org/article/93ec896433ad409aa555dc70113761fa |
| indexed_in | crossref, doaj |
| authorships[0].author.id | https://openalex.org/A5042749439 |
| authorships[0].author.orcid | |
| authorships[0].author.display_name | Nader Abdel Karim |
| authorships[0].countries | JO |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I33926330 |
| authorships[0].affiliations[0].raw_affiliation_string | Department of Intelligent Systems, Faculty of Artificial Intelligence, Al-Balqa Applied University, Al-Salt, Jordan |
| authorships[0].institutions[0].id | https://openalex.org/I33926330 |
| authorships[0].institutions[0].ror | https://ror.org/00qedmt22 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I33926330 |
| authorships[0].institutions[0].country_code | JO |
| authorships[0].institutions[0].display_name | Al-Balqa Applied University |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Nader Abdel Karim |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Department of Intelligent Systems, Faculty of Artificial Intelligence, Al-Balqa Applied University, Al-Salt, Jordan |
| authorships[1].author.id | https://openalex.org/A5057174588 |
| authorships[1].author.orcid | https://orcid.org/0000-0003-1965-1869 |
| authorships[1].author.display_name | Osama A. Khashan |
| authorships[1].countries | AE |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I4210164135 |
| authorships[1].affiliations[0].raw_affiliation_string | Research and Innovation Centers, Rabdan Academy, Abu Dhabi, United Arab Emirates |
| authorships[1].institutions[0].id | https://openalex.org/I4210164135 |
| authorships[1].institutions[0].ror | https://ror.org/05jnbme07 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I4210164135, https://openalex.org/I74796645 |
| authorships[1].institutions[0].country_code | AE |
| authorships[1].institutions[0].display_name | Birla Institute of Technology and Science, Pilani - Dubai Campus |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Osama Ahmed Khashan |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Research and Innovation Centers, Rabdan Academy, Abu Dhabi, United Arab Emirates |
| authorships[2].author.id | https://openalex.org/A5046625030 |
| authorships[2].author.orcid | https://orcid.org/0009-0000-9504-3844 |
| authorships[2].author.display_name | Hasan Kanaker |
| authorships[2].countries | JO |
| authorships[2].affiliations[0].institution_ids | https://openalex.org/I92449659 |
| authorships[2].affiliations[0].raw_affiliation_string | Department of Cyber Security, Isra University, Amman, Jordan |
| authorships[2].institutions[0].id | https://openalex.org/I92449659 |
| authorships[2].institutions[0].ror | https://ror.org/04d4bt482 |
| authorships[2].institutions[0].type | education |
| authorships[2].institutions[0].lineage | https://openalex.org/I92449659 |
| authorships[2].institutions[0].country_code | JO |
| authorships[2].institutions[0].display_name | Isra University |
| authorships[2].author_position | middle |
| authorships[2].raw_author_name | Hasan Kanaker |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | Department of Cyber Security, Isra University, Amman, Jordan |
| authorships[3].author.id | https://openalex.org/A5052373934 |
| authorships[3].author.orcid | https://orcid.org/0009-0001-5043-8276 |
| authorships[3].author.display_name | Waleed K. Abdulraheem |
| authorships[3].countries | JO |
| authorships[3].affiliations[0].institution_ids | https://openalex.org/I3132651366 |
| authorships[3].affiliations[0].raw_affiliation_string | Information Systems and Networks Department, The World Islamic Sciences and Education University, Amman, Jordan |
| authorships[3].institutions[0].id | https://openalex.org/I3132651366 |
| authorships[3].institutions[0].ror | https://ror.org/051mkwn17 |
| authorships[3].institutions[0].type | education |
| authorships[3].institutions[0].lineage | https://openalex.org/I3132651366 |
| authorships[3].institutions[0].country_code | JO |
| authorships[3].institutions[0].display_name | World Islamic Sciences and Education University |
| authorships[3].author_position | middle |
| authorships[3].raw_author_name | Waleed K. Abdulraheem |
| authorships[3].is_corresponding | False |
| authorships[3].raw_affiliation_strings | Information Systems and Networks Department, The World Islamic Sciences and Education University, Amman, Jordan |
| authorships[4].author.id | https://openalex.org/A5102843496 |
| authorships[4].author.orcid | https://orcid.org/0000-0002-3864-7323 |
| authorships[4].author.display_name | Mohammad Alshinwan |
| authorships[4].countries | JO |
| authorships[4].affiliations[0].institution_ids | https://openalex.org/I91633459 |
| authorships[4].affiliations[0].raw_affiliation_string | MEU Research Unit, Middle East University, Amman, Jordan |
| authorships[4].affiliations[1].institution_ids | https://openalex.org/I146367977 |
| authorships[4].affiliations[1].raw_affiliation_string | Faculty of Information Technology, Applied Science Private University, Amman, Jordan |
| authorships[4].institutions[0].id | https://openalex.org/I146367977 |
| authorships[4].institutions[0].ror | https://ror.org/01ah6nb52 |
| authorships[4].institutions[0].type | education |
| authorships[4].institutions[0].lineage | https://openalex.org/I146367977 |
| authorships[4].institutions[0].country_code | JO |
| authorships[4].institutions[0].display_name | Applied Science Private University |
| authorships[4].institutions[1].id | https://openalex.org/I91633459 |
| authorships[4].institutions[1].ror | https://ror.org/059bgad73 |
| authorships[4].institutions[1].type | education |
| authorships[4].institutions[1].lineage | https://openalex.org/I91633459 |
| authorships[4].institutions[1].country_code | JO |
| authorships[4].institutions[1].display_name | Middle East University |
| authorships[4].author_position | middle |
| authorships[4].raw_author_name | Mohammad Alshinwan |
| authorships[4].is_corresponding | False |
| authorships[4].raw_affiliation_strings | Faculty of Information Technology, Applied Science Private University, Amman, Jordan, MEU Research Unit, Middle East University, Amman, Jordan |
| authorships[5].author.id | https://openalex.org/A5051365658 |
| authorships[5].author.orcid | https://orcid.org/0009-0004-8598-0948 |
| authorships[5].author.display_name | Abedal-Kareem Al-Banna |
| authorships[5].countries | JO |
| authorships[5].affiliations[0].institution_ids | https://openalex.org/I36622005 |
| authorships[5].affiliations[0].raw_affiliation_string | AI and Data Science Department, University of Petra, Amman, Jordan |
| authorships[5].institutions[0].id | https://openalex.org/I36622005 |
| authorships[5].institutions[0].ror | https://ror.org/039d9es10 |
| authorships[5].institutions[0].type | education |
| authorships[5].institutions[0].lineage | https://openalex.org/I36622005 |
| authorships[5].institutions[0].country_code | JO |
| authorships[5].institutions[0].display_name | Petra University |
| authorships[5].author_position | last |
| authorships[5].raw_author_name | Abedal-Kareem Al-Banna |
| authorships[5].is_corresponding | False |
| authorships[5].raw_affiliation_strings | AI and Data Science Department, University of Petra, Amman, Jordan |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdf |
| open_access.oa_status | gold |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Online Banking User Authentication Methods: A Systematic Literature Review |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T11800 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 0.9997000098228455 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1710 |
| primary_topic.subfield.display_name | Information Systems |
| primary_topic.display_name | User Authentication and Security Systems |
| related_works | https://openalex.org/W2393298610, https://openalex.org/W2314541983, https://openalex.org/W2390304521, https://openalex.org/W4253316174, https://openalex.org/W2093798919, https://openalex.org/W2161818407, https://openalex.org/W2941888532, https://openalex.org/W2610546334, https://openalex.org/W4385414233, https://openalex.org/W2017959161 |
| cited_by_count | 23 |
| counts_by_year[0].year | 2025 |
| counts_by_year[0].cited_by_count | 17 |
| counts_by_year[1].year | 2024 |
| counts_by_year[1].cited_by_count | 6 |
| locations_count | 2 |
| best_oa_location.id | doi:10.1109/access.2023.3346045 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S2485537415 |
| best_oa_location.source.issn | 2169-3536 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | True |
| best_oa_location.source.issn_l | 2169-3536 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | True |
| best_oa_location.source.display_name | IEEE Access |
| best_oa_location.source.host_organization | https://openalex.org/P4310319808 |
| best_oa_location.source.host_organization_name | Institute of Electrical and Electronics Engineers |
| best_oa_location.source.host_organization_lineage | https://openalex.org/P4310319808 |
| best_oa_location.license | |
| best_oa_location.pdf_url | https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdf |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | IEEE Access |
| best_oa_location.landing_page_url | https://doi.org/10.1109/access.2023.3346045 |
| primary_location.id | doi:10.1109/access.2023.3346045 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S2485537415 |
| primary_location.source.issn | 2169-3536 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | True |
| primary_location.source.issn_l | 2169-3536 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | True |
| primary_location.source.display_name | IEEE Access |
| primary_location.source.host_organization | https://openalex.org/P4310319808 |
| primary_location.source.host_organization_name | Institute of Electrical and Electronics Engineers |
| primary_location.source.host_organization_lineage | https://openalex.org/P4310319808 |
| primary_location.license | |
| primary_location.pdf_url | https://ieeexplore.ieee.org/ielx7/6287639/6514899/10371293.pdf |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | IEEE Access |
| primary_location.landing_page_url | https://doi.org/10.1109/access.2023.3346045 |
| publication_date | 2023-12-22 |
| publication_year | 2023 |
| referenced_works | https://openalex.org/W6785869951, https://openalex.org/W3165321135, https://openalex.org/W3007255691, https://openalex.org/W6687962928, https://openalex.org/W2784017372, https://openalex.org/W4205285701, https://openalex.org/W2565831528, https://openalex.org/W1036019587, https://openalex.org/W2991088662, https://openalex.org/W3207350613, https://openalex.org/W6734412033, https://openalex.org/W3004890695, https://openalex.org/W4376480471, https://openalex.org/W3048532300, https://openalex.org/W2095281944, https://openalex.org/W2560395019, https://openalex.org/W3001873791, https://openalex.org/W4224233547, https://openalex.org/W4388104767, https://openalex.org/W4388098609, https://openalex.org/W2414348368, https://openalex.org/W3034298130, https://openalex.org/W6717096619, https://openalex.org/W2966043835, https://openalex.org/W2325542339, https://openalex.org/W116614623, https://openalex.org/W2182961761, https://openalex.org/W2587816121, https://openalex.org/W2686168333, https://openalex.org/W2670081103, https://openalex.org/W2512984140, https://openalex.org/W2972125575, https://openalex.org/W2982187354, https://openalex.org/W2941386561, https://openalex.org/W3085083883, https://openalex.org/W6803982756, https://openalex.org/W4211207655, https://openalex.org/W3155740371, https://openalex.org/W3201014121, https://openalex.org/W6794624705, https://openalex.org/W3154693879, https://openalex.org/W4283362180, https://openalex.org/W4283332669, https://openalex.org/W4286454908, https://openalex.org/W4361295257, https://openalex.org/W3110918311, https://openalex.org/W3158726383, https://openalex.org/W3033179496, https://openalex.org/W3009201963, https://openalex.org/W2900323813, https://openalex.org/W4291518194, https://openalex.org/W2902076153, https://openalex.org/W3045909547, https://openalex.org/W2556222309, https://openalex.org/W2138392687, https://openalex.org/W2957834903, https://openalex.org/W4226459728, https://openalex.org/W2783762289, https://openalex.org/W4380203129, https://openalex.org/W4200313210, https://openalex.org/W84998977, https://openalex.org/W4380537452, https://openalex.org/W3214331061, https://openalex.org/W2545591399, https://openalex.org/W4292747815, https://openalex.org/W4296060533, https://openalex.org/W4206973885, https://openalex.org/W4210851361, https://openalex.org/W4360778083, https://openalex.org/W2335995781, https://openalex.org/W3120577282, https://openalex.org/W4295923975, https://openalex.org/W6732243383, https://openalex.org/W3204773249, https://openalex.org/W2500275115, https://openalex.org/W3202196563, https://openalex.org/W1973061367, https://openalex.org/W2040397597, https://openalex.org/W2533019400, https://openalex.org/W3171830332, https://openalex.org/W2946143896, https://openalex.org/W2054989590, https://openalex.org/W2807581297, https://openalex.org/W2550679009, https://openalex.org/W4403576724, https://openalex.org/W4290995898, https://openalex.org/W3125868980, https://openalex.org/W4225355822, https://openalex.org/W4317564936, https://openalex.org/W3093885175, https://openalex.org/W2979323854, https://openalex.org/W6782305964, https://openalex.org/W3045292544, https://openalex.org/W3046453918, https://openalex.org/W4319791240, https://openalex.org/W4283369124, https://openalex.org/W4293211096, https://openalex.org/W4388819944, https://openalex.org/W3086312460, https://openalex.org/W3195319211, https://openalex.org/W3042776832, https://openalex.org/W4302026739, https://openalex.org/W3207931346, https://openalex.org/W3163687697, https://openalex.org/W3186663351, https://openalex.org/W4220772272, https://openalex.org/W4285407538, https://openalex.org/W4313438408, https://openalex.org/W1993743592, https://openalex.org/W3093469966, https://openalex.org/W3021476248, https://openalex.org/W4386546030, https://openalex.org/W3196598991, https://openalex.org/W2316671440, https://openalex.org/W3090820577, https://openalex.org/W4385805359, https://openalex.org/W4385255087, https://openalex.org/W3173768230, https://openalex.org/W3108671495, https://openalex.org/W3113824005, https://openalex.org/W4286641499, https://openalex.org/W3190367510, https://openalex.org/W3135300972, https://openalex.org/W4304128419, https://openalex.org/W3210854102, https://openalex.org/W3094117827, https://openalex.org/W4381597113, https://openalex.org/W4386963510, https://openalex.org/W2908400479, https://openalex.org/W4282837375, https://openalex.org/W4211255456, https://openalex.org/W2570225859, https://openalex.org/W2418884073, https://openalex.org/W2590368506, https://openalex.org/W3079289086, https://openalex.org/W2560078380, https://openalex.org/W3102624465, https://openalex.org/W2207138462, https://openalex.org/W2799658831 |
| referenced_works_count | 139 |
| abstract_inverted_index.a | 11 |
| abstract_inverted_index.It | 157 |
| abstract_inverted_index.as | 54, 97 |
| abstract_inverted_index.be | 196 |
| abstract_inverted_index.by | 47, 131 |
| abstract_inverted_index.in | 6, 37, 151, 198 |
| abstract_inverted_index.it | 10 |
| abstract_inverted_index.of | 71, 108, 163, 177 |
| abstract_inverted_index.to | 22, 195 |
| abstract_inverted_index.SQL | 117 |
| abstract_inverted_index.The | 67 |
| abstract_inverted_index.and | 40, 64, 69, 119, 146, 154, 168, 192 |
| abstract_inverted_index.are | 76 |
| abstract_inverted_index.can | 88, 135 |
| abstract_inverted_index.for | 13, 92, 141 |
| abstract_inverted_index.has | 2 |
| abstract_inverted_index.new | 187 |
| abstract_inverted_index.the | 31, 80, 83, 123, 126, 160, 175, 182 |
| abstract_inverted_index.use | 162 |
| abstract_inverted_index.BBA, | 164 |
| abstract_inverted_index.This | 28, 44 |
| abstract_inverted_index.also | 184 |
| abstract_inverted_index.best | 139 |
| abstract_inverted_index.each | 72 |
| abstract_inverted_index.have | 16 |
| abstract_inverted_index.help | 173 |
| abstract_inverted_index.into | 138 |
| abstract_inverted_index.need | 194 |
| abstract_inverted_index.such | 53, 96 |
| abstract_inverted_index.that | 87, 159, 186 |
| abstract_inverted_index.then | 77 |
| abstract_inverted_index.used | 36, 130 |
| abstract_inverted_index.user | 19, 33, 50, 73, 90, 127, 148 |
| abstract_inverted_index.weak | 114 |
| abstract_inverted_index.will | 172, 190 |
| abstract_inverted_index.(DoS) | 110 |
| abstract_inverted_index.(MFA) | 171 |
| abstract_inverted_index.Also, | 122 |
| abstract_inverted_index.Banks | 15 |
| abstract_inverted_index.banks | 193 |
| abstract_inverted_index.cyber | 42, 85, 155, 188 |
| abstract_inverted_index.other | 65 |
| abstract_inverted_index.paper | 29, 45, 81, 124, 183 |
| abstract_inverted_index.their | 24, 200 |
| abstract_inverted_index.warns | 185 |
| abstract_inverted_index.which | 134 |
| abstract_inverted_index.(2FA), | 167 |
| abstract_inverted_index.(BBA), | 60 |
| abstract_inverted_index.(KBA), | 57 |
| abstract_inverted_index.(MiTM) | 105 |
| abstract_inverted_index.(PBA), | 63 |
| abstract_inverted_index.Online | 0 |
| abstract_inverted_index.banks, | 133 |
| abstract_inverted_index.become | 3 |
| abstract_inverted_index.denial | 107 |
| abstract_inverted_index.future | 147 |
| abstract_inverted_index.making | 9 |
| abstract_inverted_index.method | 75 |
| abstract_inverted_index.online | 26, 38, 93, 143, 152, 178, 202 |
| abstract_inverted_index.recent | 7 |
| abstract_inverted_index.replay | 120 |
| abstract_inverted_index.social | 100 |
| abstract_inverted_index.starts | 46 |
| abstract_inverted_index.states | 158 |
| abstract_inverted_index.target | 12 |
| abstract_inverted_index.years, | 8 |
| abstract_inverted_index.banking | 1, 39, 94, 144, 153, 179, 203 |
| abstract_inverted_index.emerge, | 191 |
| abstract_inverted_index.improve | 174 |
| abstract_inverted_index.malware | 98 |
| abstract_inverted_index.methods | 21, 35, 129, 150 |
| abstract_inverted_index.popular | 5, 132 |
| abstract_inverted_index.protect | 23 |
| abstract_inverted_index.provide | 136 |
| abstract_inverted_index.reviews | 30 |
| abstract_inverted_index.service | 109 |
| abstract_inverted_index.session | 112 |
| abstract_inverted_index.threats | 86 |
| abstract_inverted_index.various | 18, 84 |
| abstract_inverted_index.However, | 181 |
| abstract_inverted_index.accounts | 145 |
| abstract_inverted_index.attacks, | 99, 103, 106, 111 |
| abstract_inverted_index.attacks. | 121 |
| abstract_inverted_index.explores | 125 |
| abstract_inverted_index.insights | 137 |
| abstract_inverted_index.methods, | 52 |
| abstract_inverted_index.methods. | 66 |
| abstract_inverted_index.phishing | 102 |
| abstract_inverted_index.security | 176 |
| abstract_inverted_index.systems, | 95 |
| abstract_inverted_index.systems. | 180 |
| abstract_inverted_index.threats. | 43, 156 |
| abstract_inverted_index.vigilant | 197 |
| abstract_inverted_index.accounts. | 27, 204 |
| abstract_inverted_index.different | 49 |
| abstract_inverted_index.discusses | 82 |
| abstract_inverted_index.exploring | 48 |
| abstract_inverted_index.potential | 41 |
| abstract_inverted_index.practices | 140 |
| abstract_inverted_index.advantages | 68 |
| abstract_inverted_index.challenges | 189 |
| abstract_inverted_index.compromise | 89 |
| abstract_inverted_index.discussed. | 78 |
| abstract_inverted_index.hijacking, | 113 |
| abstract_inverted_index.increasing | 161 |
| abstract_inverted_index.injection, | 118 |
| abstract_inverted_index.passwords, | 115 |
| abstract_inverted_index.protecting | 199 |
| abstract_inverted_index.two-factor | 165 |
| abstract_inverted_index.implemented | 17 |
| abstract_inverted_index.keyloggers, | 116 |
| abstract_inverted_index.Furthermore, | 79 |
| abstract_inverted_index.engineering, | 101 |
| abstract_inverted_index.increasingly | 4 |
| abstract_inverted_index.multi-factor | 169 |
| abstract_inverted_index.safeguarding | 142 |
| abstract_inverted_index.cyberattacks. | 14 |
| abstract_inverted_index.disadvantages | 70 |
| abstract_inverted_index.authentication | 20, 34, 51, 56, 59, 62, 74, 91, 128, 149, 166, 170 |
| abstract_inverted_index.knowledge-based | 55 |
| abstract_inverted_index.biometrics-based | 58 |
| abstract_inverted_index.possession-based | 61 |
| abstract_inverted_index.state-of-the-art | 32 |
| abstract_inverted_index.customers’ | 25, 201 |
| abstract_inverted_index.man-in-the-middle | 104 |
| cited_by_percentile_year.max | 100 |
| cited_by_percentile_year.min | 98 |
| countries_distinct_count | 2 |
| institutions_distinct_count | 6 |
| sustainable_development_goals[0].id | https://metadata.un.org/sdg/16 |
| sustainable_development_goals[0].score | 0.6200000047683716 |
| sustainable_development_goals[0].display_name | Peace, Justice and strong institutions |
| citation_normalized_percentile.value | 0.98572613 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | True |