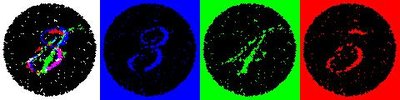
Optimizing Image Steganography using Particle Swarm Optimization Algorithm Article Swipe
R. Teixeira De Lima
,
Warley Gramacho
,
Ary Henrique
·
 YOU?
·
· 2017
· Open Access
·
· DOI: https://doi.org/10.5120/ijca2017913686
YOU?
·
· 2017
· Open Access
·
· DOI: https://doi.org/10.5120/ijca2017913686
 YOU?
·
· 2017
· Open Access
·
· DOI: https://doi.org/10.5120/ijca2017913686
YOU?
·
· 2017
· Open Access
·
· DOI: https://doi.org/10.5120/ijca2017913686
Image Steganography is the computing field of hiding information from a source into a target image in a way that it becomes almost imperceptible from one's eyes.Despite the high capacity of hiding information, the usual Least Significant Bit (LSB) techniques could be easily discovered.In order to hide information in more significant bits, the target image should be optimized.In this paper, it is proposed an optimization solution based on the Standard Particle Swarm Optimization 2011 (PSO), which has been compared with a previous Genetic Algorithm-based approach showing promising results.Specifically, it is shown an adaptation in the solution in order to keep the essence of PSO while remaining message hosted bits unchanged.
Related Topics
Concepts
Metadata
- Type
- article
- Language
- en
- Landing Page
- http://doi.org/10.5120/ijca2017913686
- https://doi.org/10.5120/ijca2017913686
- OA Status
- bronze
- Cited By
- 16
- References
- 13
- Related Works
- 10
- OpenAlex ID
- https://openalex.org/W2626248599
All OpenAlex metadata
Raw OpenAlex JSON
- OpenAlex ID
-
https://openalex.org/W2626248599Canonical identifier for this work in OpenAlex
- DOI
-
https://doi.org/10.5120/ijca2017913686Digital Object Identifier
- Title
-
Optimizing Image Steganography using Particle Swarm Optimization AlgorithmWork title
- Type
-
articleOpenAlex work type
- Language
-
enPrimary language
- Publication year
-
2017Year of publication
- Publication date
-
2017-04-17Full publication date if available
- Authors
-
R. Teixeira De Lima, Warley Gramacho, Ary HenriqueList of authors in order
- Landing page
-
https://doi.org/10.5120/ijca2017913686Publisher landing page
- PDF URL
-
https://doi.org/10.5120/ijca2017913686Direct link to full text PDF
- Open access
-
YesWhether a free full text is available
- OA status
-
bronzeOpen access status per OpenAlex
- OA URL
-
https://doi.org/10.5120/ijca2017913686Direct OA link when available
- Concepts
-
Computer science, Steganography, Particle swarm optimization, Image (mathematics), Algorithm, Swarm behaviour, Artificial intelligenceTop concepts (fields/topics) attached by OpenAlex
- Cited by
-
16Total citation count in OpenAlex
- Citations by year (recent)
-
2024: 1, 2023: 4, 2022: 4, 2021: 2, 2020: 3Per-year citation counts (last 5 years)
- References (count)
-
13Number of works referenced by this work
- Related works (count)
-
10Other works algorithmically related by OpenAlex
Full payload
| id | https://openalex.org/W2626248599 |
|---|---|
| doi | https://doi.org/10.5120/ijca2017913686 |
| ids.doi | https://doi.org/10.5120/ijca2017913686 |
| ids.mag | 2626248599 |
| ids.openalex | https://openalex.org/W2626248599 |
| fwci | 0.63555111 |
| type | article |
| title | Optimizing Image Steganography using Particle Swarm Optimization Algorithm |
| biblio.issue | 7 |
| biblio.volume | 164 |
| biblio.last_page | 5 |
| biblio.first_page | 1 |
| topics[0].id | https://openalex.org/T10388 |
| topics[0].field.id | https://openalex.org/fields/17 |
| topics[0].field.display_name | Computer Science |
| topics[0].score | 1.0 |
| topics[0].domain.id | https://openalex.org/domains/3 |
| topics[0].domain.display_name | Physical Sciences |
| topics[0].subfield.id | https://openalex.org/subfields/1707 |
| topics[0].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[0].display_name | Advanced Steganography and Watermarking Techniques |
| topics[1].id | https://openalex.org/T12707 |
| topics[1].field.id | https://openalex.org/fields/22 |
| topics[1].field.display_name | Engineering |
| topics[1].score | 0.9987999796867371 |
| topics[1].domain.id | https://openalex.org/domains/3 |
| topics[1].domain.display_name | Physical Sciences |
| topics[1].subfield.id | https://openalex.org/subfields/2214 |
| topics[1].subfield.display_name | Media Technology |
| topics[1].display_name | Vehicle License Plate Recognition |
| topics[2].id | https://openalex.org/T11017 |
| topics[2].field.id | https://openalex.org/fields/17 |
| topics[2].field.display_name | Computer Science |
| topics[2].score | 0.9950000047683716 |
| topics[2].domain.id | https://openalex.org/domains/3 |
| topics[2].domain.display_name | Physical Sciences |
| topics[2].subfield.id | https://openalex.org/subfields/1707 |
| topics[2].subfield.display_name | Computer Vision and Pattern Recognition |
| topics[2].display_name | Chaos-based Image/Signal Encryption |
| is_xpac | False |
| apc_list | |
| apc_paid | |
| concepts[0].id | https://openalex.org/C41008148 |
| concepts[0].level | 0 |
| concepts[0].score | 0.872703492641449 |
| concepts[0].wikidata | https://www.wikidata.org/wiki/Q21198 |
| concepts[0].display_name | Computer science |
| concepts[1].id | https://openalex.org/C108801101 |
| concepts[1].level | 3 |
| concepts[1].score | 0.8145222663879395 |
| concepts[1].wikidata | https://www.wikidata.org/wiki/Q15032 |
| concepts[1].display_name | Steganography |
| concepts[2].id | https://openalex.org/C85617194 |
| concepts[2].level | 2 |
| concepts[2].score | 0.7764053344726562 |
| concepts[2].wikidata | https://www.wikidata.org/wiki/Q2072794 |
| concepts[2].display_name | Particle swarm optimization |
| concepts[3].id | https://openalex.org/C115961682 |
| concepts[3].level | 2 |
| concepts[3].score | 0.5487455129623413 |
| concepts[3].wikidata | https://www.wikidata.org/wiki/Q860623 |
| concepts[3].display_name | Image (mathematics) |
| concepts[4].id | https://openalex.org/C11413529 |
| concepts[4].level | 1 |
| concepts[4].score | 0.491551011800766 |
| concepts[4].wikidata | https://www.wikidata.org/wiki/Q8366 |
| concepts[4].display_name | Algorithm |
| concepts[5].id | https://openalex.org/C181335050 |
| concepts[5].level | 2 |
| concepts[5].score | 0.42277759313583374 |
| concepts[5].wikidata | https://www.wikidata.org/wiki/Q14915018 |
| concepts[5].display_name | Swarm behaviour |
| concepts[6].id | https://openalex.org/C154945302 |
| concepts[6].level | 1 |
| concepts[6].score | 0.3753994107246399 |
| concepts[6].wikidata | https://www.wikidata.org/wiki/Q11660 |
| concepts[6].display_name | Artificial intelligence |
| keywords[0].id | https://openalex.org/keywords/computer-science |
| keywords[0].score | 0.872703492641449 |
| keywords[0].display_name | Computer science |
| keywords[1].id | https://openalex.org/keywords/steganography |
| keywords[1].score | 0.8145222663879395 |
| keywords[1].display_name | Steganography |
| keywords[2].id | https://openalex.org/keywords/particle-swarm-optimization |
| keywords[2].score | 0.7764053344726562 |
| keywords[2].display_name | Particle swarm optimization |
| keywords[3].id | https://openalex.org/keywords/image |
| keywords[3].score | 0.5487455129623413 |
| keywords[3].display_name | Image (mathematics) |
| keywords[4].id | https://openalex.org/keywords/algorithm |
| keywords[4].score | 0.491551011800766 |
| keywords[4].display_name | Algorithm |
| keywords[5].id | https://openalex.org/keywords/swarm-behaviour |
| keywords[5].score | 0.42277759313583374 |
| keywords[5].display_name | Swarm behaviour |
| keywords[6].id | https://openalex.org/keywords/artificial-intelligence |
| keywords[6].score | 0.3753994107246399 |
| keywords[6].display_name | Artificial intelligence |
| language | en |
| locations[0].id | doi:10.5120/ijca2017913686 |
| locations[0].is_oa | True |
| locations[0].source.id | https://openalex.org/S4210206007 |
| locations[0].source.issn | 0975-8887 |
| locations[0].source.type | journal |
| locations[0].source.is_oa | False |
| locations[0].source.issn_l | 0975-8887 |
| locations[0].source.is_core | True |
| locations[0].source.is_in_doaj | False |
| locations[0].source.display_name | International Journal of Computer Applications |
| locations[0].source.host_organization | |
| locations[0].source.host_organization_name | |
| locations[0].license | |
| locations[0].pdf_url | https://doi.org/10.5120/ijca2017913686 |
| locations[0].version | publishedVersion |
| locations[0].raw_type | journal-article |
| locations[0].license_id | |
| locations[0].is_accepted | True |
| locations[0].is_published | True |
| locations[0].raw_source_name | International Journal of Computer Applications |
| locations[0].landing_page_url | http://doi.org/10.5120/ijca2017913686 |
| indexed_in | crossref |
| authorships[0].author.id | https://openalex.org/A5114375423 |
| authorships[0].author.orcid | https://orcid.org/0000-0001-5545-6513 |
| authorships[0].author.display_name | R. Teixeira De Lima |
| authorships[0].countries | BR |
| authorships[0].affiliations[0].institution_ids | https://openalex.org/I41458283 |
| authorships[0].affiliations[0].raw_affiliation_string | Computer Science Department University Federal of Tocantins Palmas/Tocantins -Brazil |
| authorships[0].institutions[0].id | https://openalex.org/I41458283 |
| authorships[0].institutions[0].ror | https://ror.org/053xy8k29 |
| authorships[0].institutions[0].type | education |
| authorships[0].institutions[0].lineage | https://openalex.org/I41458283 |
| authorships[0].institutions[0].country_code | BR |
| authorships[0].institutions[0].display_name | Universidade Federal do Tocantins |
| authorships[0].author_position | first |
| authorships[0].raw_author_name | Rafael Lima |
| authorships[0].is_corresponding | False |
| authorships[0].raw_affiliation_strings | Computer Science Department University Federal of Tocantins Palmas/Tocantins -Brazil |
| authorships[1].author.id | https://openalex.org/A5113785550 |
| authorships[1].author.orcid | |
| authorships[1].author.display_name | Warley Gramacho |
| authorships[1].countries | BR |
| authorships[1].affiliations[0].institution_ids | https://openalex.org/I41458283 |
| authorships[1].affiliations[0].raw_affiliation_string | Computer Science Department University Federal of Tocantins Palmas/Tocantins -Brazil |
| authorships[1].institutions[0].id | https://openalex.org/I41458283 |
| authorships[1].institutions[0].ror | https://ror.org/053xy8k29 |
| authorships[1].institutions[0].type | education |
| authorships[1].institutions[0].lineage | https://openalex.org/I41458283 |
| authorships[1].institutions[0].country_code | BR |
| authorships[1].institutions[0].display_name | Universidade Federal do Tocantins |
| authorships[1].author_position | middle |
| authorships[1].raw_author_name | Warley Gramacho |
| authorships[1].is_corresponding | False |
| authorships[1].raw_affiliation_strings | Computer Science Department University Federal of Tocantins Palmas/Tocantins -Brazil |
| authorships[2].author.id | https://openalex.org/A5021764918 |
| authorships[2].author.orcid | |
| authorships[2].author.display_name | Ary Henrique |
| authorships[2].countries | BR |
| authorships[2].affiliations[0].institution_ids | https://openalex.org/I41458283 |
| authorships[2].affiliations[0].raw_affiliation_string | Computer Science Department University Federal of Tocantins Palmas/Tocantins -Brazil |
| authorships[2].institutions[0].id | https://openalex.org/I41458283 |
| authorships[2].institutions[0].ror | https://ror.org/053xy8k29 |
| authorships[2].institutions[0].type | education |
| authorships[2].institutions[0].lineage | https://openalex.org/I41458283 |
| authorships[2].institutions[0].country_code | BR |
| authorships[2].institutions[0].display_name | Universidade Federal do Tocantins |
| authorships[2].author_position | last |
| authorships[2].raw_author_name | Ary Henrique |
| authorships[2].is_corresponding | False |
| authorships[2].raw_affiliation_strings | Computer Science Department University Federal of Tocantins Palmas/Tocantins -Brazil |
| has_content.pdf | True |
| has_content.grobid_xml | True |
| is_paratext | False |
| open_access.is_oa | True |
| open_access.oa_url | https://doi.org/10.5120/ijca2017913686 |
| open_access.oa_status | bronze |
| open_access.any_repository_has_fulltext | False |
| created_date | 2025-10-10T00:00:00 |
| display_name | Optimizing Image Steganography using Particle Swarm Optimization Algorithm |
| has_fulltext | True |
| is_retracted | False |
| updated_date | 2025-11-06T03:46:38.306776 |
| primary_topic.id | https://openalex.org/T10388 |
| primary_topic.field.id | https://openalex.org/fields/17 |
| primary_topic.field.display_name | Computer Science |
| primary_topic.score | 1.0 |
| primary_topic.domain.id | https://openalex.org/domains/3 |
| primary_topic.domain.display_name | Physical Sciences |
| primary_topic.subfield.id | https://openalex.org/subfields/1707 |
| primary_topic.subfield.display_name | Computer Vision and Pattern Recognition |
| primary_topic.display_name | Advanced Steganography and Watermarking Techniques |
| related_works | https://openalex.org/W2969135852, https://openalex.org/W2188948172, https://openalex.org/W2736680465, https://openalex.org/W4288714711, https://openalex.org/W38533693, https://openalex.org/W3200708550, https://openalex.org/W2153696906, https://openalex.org/W2892069487, https://openalex.org/W2771637876, https://openalex.org/W2741842698 |
| cited_by_count | 16 |
| counts_by_year[0].year | 2024 |
| counts_by_year[0].cited_by_count | 1 |
| counts_by_year[1].year | 2023 |
| counts_by_year[1].cited_by_count | 4 |
| counts_by_year[2].year | 2022 |
| counts_by_year[2].cited_by_count | 4 |
| counts_by_year[3].year | 2021 |
| counts_by_year[3].cited_by_count | 2 |
| counts_by_year[4].year | 2020 |
| counts_by_year[4].cited_by_count | 3 |
| counts_by_year[5].year | 2019 |
| counts_by_year[5].cited_by_count | 1 |
| counts_by_year[6].year | 2018 |
| counts_by_year[6].cited_by_count | 1 |
| locations_count | 1 |
| best_oa_location.id | doi:10.5120/ijca2017913686 |
| best_oa_location.is_oa | True |
| best_oa_location.source.id | https://openalex.org/S4210206007 |
| best_oa_location.source.issn | 0975-8887 |
| best_oa_location.source.type | journal |
| best_oa_location.source.is_oa | False |
| best_oa_location.source.issn_l | 0975-8887 |
| best_oa_location.source.is_core | True |
| best_oa_location.source.is_in_doaj | False |
| best_oa_location.source.display_name | International Journal of Computer Applications |
| best_oa_location.source.host_organization | |
| best_oa_location.source.host_organization_name | |
| best_oa_location.license | |
| best_oa_location.pdf_url | https://doi.org/10.5120/ijca2017913686 |
| best_oa_location.version | publishedVersion |
| best_oa_location.raw_type | journal-article |
| best_oa_location.license_id | |
| best_oa_location.is_accepted | True |
| best_oa_location.is_published | True |
| best_oa_location.raw_source_name | International Journal of Computer Applications |
| best_oa_location.landing_page_url | http://doi.org/10.5120/ijca2017913686 |
| primary_location.id | doi:10.5120/ijca2017913686 |
| primary_location.is_oa | True |
| primary_location.source.id | https://openalex.org/S4210206007 |
| primary_location.source.issn | 0975-8887 |
| primary_location.source.type | journal |
| primary_location.source.is_oa | False |
| primary_location.source.issn_l | 0975-8887 |
| primary_location.source.is_core | True |
| primary_location.source.is_in_doaj | False |
| primary_location.source.display_name | International Journal of Computer Applications |
| primary_location.source.host_organization | |
| primary_location.source.host_organization_name | |
| primary_location.license | |
| primary_location.pdf_url | https://doi.org/10.5120/ijca2017913686 |
| primary_location.version | publishedVersion |
| primary_location.raw_type | journal-article |
| primary_location.license_id | |
| primary_location.is_accepted | True |
| primary_location.is_published | True |
| primary_location.raw_source_name | International Journal of Computer Applications |
| primary_location.landing_page_url | http://doi.org/10.5120/ijca2017913686 |
| publication_date | 2017-04-17 |
| publication_year | 2017 |
| referenced_works | https://openalex.org/W1666784313, https://openalex.org/W4232483350, https://openalex.org/W2083122891, https://openalex.org/W1500538633, https://openalex.org/W2329101434, https://openalex.org/W6683284539, https://openalex.org/W2057035153, https://openalex.org/W1541501294, https://openalex.org/W2568426016, https://openalex.org/W2246105787, https://openalex.org/W1508120902, https://openalex.org/W2543580944, https://openalex.org/W2157470389 |
| referenced_works_count | 13 |
| abstract_inverted_index.a | 10, 13, 17, 80 |
| abstract_inverted_index.an | 63, 91 |
| abstract_inverted_index.be | 41, 56 |
| abstract_inverted_index.in | 16, 48, 93, 96 |
| abstract_inverted_index.is | 2, 61, 89 |
| abstract_inverted_index.it | 20, 60, 88 |
| abstract_inverted_index.of | 6, 30, 102 |
| abstract_inverted_index.on | 67 |
| abstract_inverted_index.to | 45, 98 |
| abstract_inverted_index.Bit | 37 |
| abstract_inverted_index.PSO | 103 |
| abstract_inverted_index.has | 76 |
| abstract_inverted_index.the | 3, 27, 33, 52, 68, 94, 100 |
| abstract_inverted_index.way | 18 |
| abstract_inverted_index.2011 | 73 |
| abstract_inverted_index.been | 77 |
| abstract_inverted_index.bits | 108 |
| abstract_inverted_index.from | 9, 24 |
| abstract_inverted_index.hide | 46 |
| abstract_inverted_index.high | 28 |
| abstract_inverted_index.into | 12 |
| abstract_inverted_index.keep | 99 |
| abstract_inverted_index.more | 49 |
| abstract_inverted_index.that | 19 |
| abstract_inverted_index.this | 58 |
| abstract_inverted_index.with | 79 |
| abstract_inverted_index.(LSB) | 38 |
| abstract_inverted_index.Image | 0 |
| abstract_inverted_index.Least | 35 |
| abstract_inverted_index.Swarm | 71 |
| abstract_inverted_index.based | 66 |
| abstract_inverted_index.bits, | 51 |
| abstract_inverted_index.could | 40 |
| abstract_inverted_index.field | 5 |
| abstract_inverted_index.image | 15, 54 |
| abstract_inverted_index.one's | 25 |
| abstract_inverted_index.order | 44, 97 |
| abstract_inverted_index.shown | 90 |
| abstract_inverted_index.usual | 34 |
| abstract_inverted_index.which | 75 |
| abstract_inverted_index.while | 104 |
| abstract_inverted_index.(PSO), | 74 |
| abstract_inverted_index.almost | 22 |
| abstract_inverted_index.easily | 42 |
| abstract_inverted_index.hiding | 7, 31 |
| abstract_inverted_index.hosted | 107 |
| abstract_inverted_index.paper, | 59 |
| abstract_inverted_index.should | 55 |
| abstract_inverted_index.source | 11 |
| abstract_inverted_index.target | 14, 53 |
| abstract_inverted_index.Genetic | 82 |
| abstract_inverted_index.becomes | 21 |
| abstract_inverted_index.essence | 101 |
| abstract_inverted_index.message | 106 |
| abstract_inverted_index.showing | 85 |
| abstract_inverted_index.Particle | 70 |
| abstract_inverted_index.Standard | 69 |
| abstract_inverted_index.approach | 84 |
| abstract_inverted_index.capacity | 29 |
| abstract_inverted_index.compared | 78 |
| abstract_inverted_index.previous | 81 |
| abstract_inverted_index.proposed | 62 |
| abstract_inverted_index.solution | 65, 95 |
| abstract_inverted_index.computing | 4 |
| abstract_inverted_index.promising | 86 |
| abstract_inverted_index.remaining | 105 |
| abstract_inverted_index.adaptation | 92 |
| abstract_inverted_index.techniques | 39 |
| abstract_inverted_index.unchanged. | 109 |
| abstract_inverted_index.Significant | 36 |
| abstract_inverted_index.information | 8, 47 |
| abstract_inverted_index.significant | 50 |
| abstract_inverted_index.Optimization | 72 |
| abstract_inverted_index.eyes.Despite | 26 |
| abstract_inverted_index.information, | 32 |
| abstract_inverted_index.optimization | 64 |
| abstract_inverted_index.optimized.In | 57 |
| abstract_inverted_index.Steganography | 1 |
| abstract_inverted_index.discovered.In | 43 |
| abstract_inverted_index.imperceptible | 23 |
| abstract_inverted_index.Algorithm-based | 83 |
| abstract_inverted_index.results.Specifically, | 87 |
| cited_by_percentile_year.max | 97 |
| cited_by_percentile_year.min | 90 |
| countries_distinct_count | 1 |
| institutions_distinct_count | 3 |
| citation_normalized_percentile.value | 0.72537466 |
| citation_normalized_percentile.is_in_top_1_percent | False |
| citation_normalized_percentile.is_in_top_10_percent | False |