
Requirement

Requirement
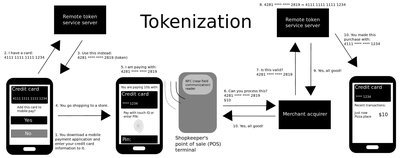
Tokenization (Data Security)

Tokenization (Data Security)
VS
VS
Requirement
VS
Tokenization (Data Security)
Condition that must be satisfied for an engineered work to be acceptable
Concept in data security
Open the question; AI will answer
Dialectical Questions
General
How are Requirement and Tokenization (Data Security) the same?
AI will reply...
How are Requirement and Tokenization (Data Security) different?
AI will reply...
What does Requirement highlight about Tokenization (Data Security)?
AI will reply...
What does Tokenization (Data Security) highlight about Requirement?
AI will reply...
Where do Requirement and Tokenization (Data Security) most directly clash?
AI will reply...
Where do Requirement and Tokenization (Data Security) unexpectedly connect?
AI will reply...
What are the main strengths of Requirement compared to Tokenization (Data Security)?
AI will reply...
What are the main strengths of Tokenization (Data Security) compared to Requirement?
AI will reply...
What are the main weaknesses of Requirement compared to Tokenization (Data Security)?
AI will reply...
What are the main weaknesses of Tokenization (Data Security) compared to Requirement?
AI will reply...
What larger context includes both Requirement and Tokenization (Data Security)?
AI will reply...
How might Requirement and Tokenization (Data Security) balance or complement each other?
AI will reply...
What would the world look like if Requirement dominated?
AI will reply...
What would the world look like if Tokenization (Data Security) dominated?
AI will reply...
What would be lost if Requirement disappeared?
AI will reply...
What would be lost if Tokenization (Data Security) disappeared?
AI will reply...
How might Requirement and Tokenization (Data Security) depend on each other?
AI will reply...
What hidden patterns link Requirement and Tokenization (Data Security)?
AI will reply...
How might Requirement and Tokenization (Data Security) evolve in the future?
AI will reply...
Can the conflict between Requirement and Tokenization (Data Security) be resolved—or only managed?
AI will reply...
Self & Identity
How do Requirement and Tokenization (Data Security) shape ideas of identity?
AI will reply...
What does choosing Requirement over Tokenization (Data Security) say about the self?
AI will reply...
How might people identify with Requirement differently than with Tokenization (Data Security)?
AI will reply...
Culture & Symbol
What cultural meanings are attached to Requirement and to Tokenization (Data Security)?
AI will reply...
How are Requirement and Tokenization (Data Security) represented in symbols, stories, or media?
AI will reply...
What metaphors capture the tension between Requirement and Tokenization (Data Security)?
AI will reply...
History & Memory
How has history treated Requirement compared to Tokenization (Data Security)?
AI will reply...
What past conflicts or links between Requirement and Tokenization (Data Security) still matter today?
AI will reply...
How do memories of Requirement affect the way we see Tokenization (Data Security)?
AI will reply...
Nature & Cosmos
How do Requirement and Tokenization (Data Security) relate to the natural world?
AI will reply...
How does Requirement reflect universal laws differently from Tokenization (Data Security)?
AI will reply...
What natural metaphors describe Requirement and Tokenization (Data Security)?
AI will reply...
Body & Health
How do Requirement and Tokenization (Data Security) each affect human wellbeing?
AI will reply...
What emotions or sensations are tied to Requirement versus Tokenization (Data Security)?
AI will reply...
How do Requirement and Tokenization (Data Security) relate to survival or resilience?
AI will reply...
Economy & Work
How do Requirement and Tokenization (Data Security) change the meaning of work or value?
AI will reply...
How do Requirement and Tokenization (Data Security) compete for resources?
AI will reply...
What would everyday life look like under Requirement versus Tokenization (Data Security)?
AI will reply...
Power & Control
How does Requirement try to control or influence Tokenization (Data Security)?
AI will reply...
How does Tokenization (Data Security) try to control or influence Requirement?
AI will reply...
Who gains power if Requirement dominates Tokenization (Data Security), or if Tokenization (Data Security) dominates Requirement?
AI will reply...
Learning & Knowing
How do Requirement and Tokenization (Data Security) define knowledge differently?
AI will reply...
What kinds of truth are emphasized by Requirement versus Tokenization (Data Security)?
AI will reply...
How does comparing Requirement and Tokenization (Data Security) expand what we know?
AI will reply...
Technology & Tools
How do Requirement and Tokenization (Data Security) influence the tools people use?
AI will reply...
How do Requirement and Tokenization (Data Security) change through new technologies?
AI will reply...
How do Requirement and Tokenization (Data Security) shape the pace of progress?
AI will reply...
Imagination & Play
How do Requirement and Tokenization (Data Security) inspire creativity or play?
AI will reply...
What games or stories can be told about Requirement vs Tokenization (Data Security)?
AI will reply...
How do Requirement and Tokenization (Data Security) shape our dreams of the future?
AI will reply...
Emotion & Expression
What emotions are most connected to Requirement? To Tokenization (Data Security)?
AI will reply...
How would art or music express Requirement compared to Tokenization (Data Security)?
AI will reply...
What inner conflicts arise when choosing between Requirement and Tokenization (Data Security)?
AI will reply...
Paradigms & Patterns
What assumptions about reality are revealed by Requirement versus Tokenization (Data Security)?
AI will reply...
What patterns link Requirement and Tokenization (Data Security)?
AI will reply...
How could Requirement and Tokenization (Data Security) be combined into a new paradigm?
AI will reply...